April 2002
This manual describes concepts and planning tasks to prepare you to use the Compaq TCP/IP Services for OpenVMS product.
Revision Information: This is a revised manual.
Operating Systems: OpenVMS Alpha Versions 7.2-2, 7.3 OpenVMS VAX Versions 7.2, 7.3
Software Version: Compaq TCP/IP Services for OpenVMS Version 5.3
Houston, Texas
April 2002
COMPAQ, the Compaq logo, Alpha, OpenVMS, Tru64, VAX, VMS, and the Compaq logo are trademarks of Compaq Information Technologies Group, L.P., in the U.S. and/or other countries.
Microsoft, MS-DOS, Visual C++, Windows, and Windows NT are trademarks of Microsoft Corporation in the U.S. and/or other countries.
Intel, Intel Inside, and Pentium are trademarks of Intel Corporation in the U.S. and/or other countries
Motif, OSF/1, and UNIX are trademarks of The Open Group in the U.S. and/or other countries.
Java and all Java-based marks are trademarks or registered trademarks of Sun Microsystems, Inc., in the U.S. and other countries.
All other product names mentioned herein may be trademarks of their respective companies.
Confidential computer software. Valid license from Compaq required for possession, use or copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor's standard commercial license.
Compaq shall not be liable for technical or editorial errors or omissions contained herein. The information is provided “as is” without warranty of any kind and is subject to change without notice. The warranties for Compaq products are set forth in the express limited warranty statements accompanying such products. Nothing herein should be construed as constituting an additional warranty.
Table of Contents
- Preface
- 1 Introducing Compaq TCP/IP Services for OpenVMS
- 1.1 Overview of TCP/IP Services
- 1.1.1 Data Link Layer
- 1.1.2 Internet Layer
- 1.1.3 Transport Layer
- 1.1.4 Application Layer
- 1.2 Application Support
- 1.3 APIs
- 1.4 Understanding RFCs
- 2 Understanding OpenVMS and UNIX Implementations
- 2.1 Evaluating the Computing Environment
- 2.2 File Compatibility
- 2.2.1 Directory Hierarchies
- 2.2.2 File Specifications
- 2.2.3 Absolute and Relative File Specifications
- 2.2.4 File Specifications
- 2.2.5 Case Sensitivity
- 2.2.6 File Types
- 2.2.7 Version Numbers
- 2.2.8 Linking Files
- 2.2.9 File Structures
- 2.2.10 File Ownership
- 2.2.11 File Protections
- 2.3 Portability
- 2.4 Determining Which File System to Use
- 3 OpenVMS Server and Network Configurations
- 3.1 Understanding OpenVMS VAX and Alpha Systems
- 3.1.1 User Environment
- 3.1.2 System Management Environment
- 3.1.3 Programming Environment
- 3.2 OpenVMS Cluster Configuration
- 3.2.1 Failover Capability
- 3.2.2 Connection Load Balancing
- 3.3 Multihoming and Multiple Interfaces
- 3.3.1 Multihomed Computers
- 3.3.2 Primary Interface
- 3.3.3 Pseudointerfaces
- 3.4 Serial Line Connections
- 4 OpenVMS Operating System TCP/IP Features
- 5 Network Server Services
- 5.1 Network Time Protocol (NTP)
- 5.2 Routing
- 5.2.1 Static Routing
- 5.2.2 Dynamic Routing
- 5.3 Remote Client Management (BOOTP/DHCP)
- 5.3.1 How DHCP Operates
- 5.3.2 How DHCP Allocates IP Addresses
- 5.3.3 Relationship Between DHCP and BOOTP
- 5.3.4 Client ID
- 5.4 File Transfer Services
- 5.4.1 FTP (File Transfer Protocol)
- 5.4.2 Trivial FTP (TFTP)
- 5.4.3 R Commands
- 5.4.4 Differences Between FTP and RCP
- 5.5 Simple Network Management Protocol (SNMP)
- 5.5.1 Configuring SNMP
- 5.5.2 Ensuring Access to Mounted Data
- 6 Mail Services
- 7 Connectivity Services
- 8 Domain Name System/BIND (DNS/BIND)
- 8.1 Overview of the BIND Service
- 8.2 BIND Service Components
- 8.3 Domains
- 8.4 Domain Names
- 8.4.1 Types of Domain Names
- 8.4.2 Domain Name Format
- 8.5 Zones
- 8.5.1 Delegation
- 8.6 Reverse Domains
- 8.7 BIND Server Functions
- 8.7.1 Root Name Servers
- 8.7.2 Master Name Server
- 8.7.3 Slave Name Server
- 8.7.4 Forwarder Servers
- 8.7.5 Caching-Only Servers
- 8.7.6 Configurations Without Internet Access
- 8.7.7 Zone Transfers
- 8.8 BIND Server Configuration Files
- 8.9 BIND Server Database Files
- 8.9.1 Master Zone File
- 8.9.2 Reverse Zone File
- 8.9.3 Loopback Interface Files
- 8.9.4 Hints File
- 8.10 BIND Resolver
- 8.10.1 Default Domain
- 8.10.2 Search List
- 8.10.3 Name Servers
- 9 IPv6
- 9.1 Understanding IPv6
- 9.1.1 Mobile IPv6
- 9.2 Understanding How Tunnels Work
- 9.3 Developing an Implementation Plan
- 9.4 Porting Existing IPv4 Applications
- 9.5 Obtaining IPv6 Addresses
- 9.6 Installing IPv6-Capable Routers
- 9.7 Configuring Domain Name System/BIND (DNS/BIND) Servers
- 9.8 Configuring IPv6 Routers
- 9.9 Configuring IPv6 Hosts
- Glossary
An open communications standard defined by the worldwide networking community, TCP/IP consists of numerous application, routing, transport, and network management protocols. These protocols enable any connected host to communicate with any other connected host, without needing to know details about the other host or the intervening network topology. Computers and networks from different manufacturers running different operating systems can interoperate seamlessly.
The Compaq TCP/IP Services for OpenVMS product is Compaq’s implementation of the TCP/IP networking protocol suite and internet services for OpenVMS Alpha and OpenVMS VAX systems.
This manual introduces the TCP/IP Services product and provides conceptual and planning information to help you configure and manage the product.
This manual is for anyone who needs an overview of the TCP/IP Services product.
See the Compaq TCP/IP Services for OpenVMS User’s Guide for information on using TCP/IP Services applications and the Compaq TCP/IP Services for OpenVMS Management guide for details on configuring and managing the TCP/IP Services product.
This manual contains the following chapters:
Chapter 1 provides an overview of the TCP/IP Services product.
Chapter 2 describes the network implementation differences between UNIX and OpenVMS.
Chapter 3 describes the many decisions you need to make about OpenVMS configuration options before configuring TCP/IP Services.
Chapter 4 describes OpenVMS operating system features that support the TCP/IP environment.
Chapter 5 describes key concepts of network server features: NTP, routing, BOOTP and DHCP, FTP, and SNMP.
Chapter 6 describes mail services: Post Office Protocol (POP), SMTP, and IMAP.
Chapter 7 discusses ways to connect to the network, such as TELNET, PPP and SLIP, DECnet-over-TCP/IP, NFS, and XDM.
Chapter 8 describes the TCP/IP Services implementation of the Berkeley Internet Name Domain (BIND) service.
Chapter 9 provides guidelines, scenarios, and checklists for deploying IPv6 on a single system in a network.
The Glossary defines terms and acronyms related to TCP/IP Services.
The following table lists the documents available with this version of Compaq TCP/IP Services for OpenVMS:
| Manual | Contents |
|---|---|
| Compaq TCP/IP Services for OpenVMS Concepts and Planning | This manual introduces TCP/IP Services and provides conceptual and planning information to help you configure and manage the product. This manual also provides a glossary of terms and acronyms, lists the RFCs associated with this product, and documents how to register your network and domain and name servers. |
| Compaq TCP/IP Services for OpenVMS Release Notes | This text file describes new features and changes to the software, including installation, upgrade, configuration, and compatibility information. These notes also describe new and existing software problems and restrictions, and software and documentation corrections. Print this text file at the beginning of the installation procedure and read it before you install Compaq TCP/IP Services for OpenVMS. |
| Compaq TCP/IP Services for OpenVMS Installation and Configuration | This manual explains how to install and configure the Compaq TCP/IP Services for OpenVMS product. |
| Compaq TCP/IP Services for OpenVMS User’s Guide | This manual describes how to use the applications available with Compaq TCP/IP Services for OpenVMS, such as remote file operations, e-mail, TELNET, TN3270, and network printing. This manual also explains how to use these services to communicate with systems on private internets or on the worldwide Internet. |
| Compaq TCP/IP Services for OpenVMS Management | This manual describes how to configure and manage the Compaq TCP/IP Services for OpenVMS product. Use this manual with the Compaq TCP/IP Services for OpenVMS Management Command Reference manual. |
| Compaq TCP/IP Services for OpenVMS Management Command Reference | This manual describes the Compaq TCP/IP Services for OpenVMS management commands. Use this manual with the Compaq TCP/IP Services for OpenVMS Management manual. |
| Compaq TCP/IP Services for OpenVMS ONC RPC Programming | This manual presents an overview of high-level programming using open network computing remote procedure calls (ONC RPC). This manual also describes the RPC programming interface and how to use the RPCGEN protocol compiler to create applications. |
| Compaq TCP/IP Services for OpenVMS Sockets API and System Services Programming | This manual describes how to use the Sockets API and OpenVMS system services to develop network-based applications. |
| Compaq TCP/IP Services for OpenVMS SNMP Programming and Reference | This manual describes the Simple Network Management Protocol (SNMP) and the SNMP application programming interface (eSNMP). It describes the subagents provided with TCP/IP Services, utilities provided for managing agents, and how to build your own subagents. |
| Compaq TCP/IP Services for OpenVMS Management Command Quick Reference Card | This reference card lists the TCP/IP management commands by component and describes the purpose of each command. |
| Compaq TCP/IP Services for OpenVMS UNIX Command Reference Card | This reference card contains information about commonly performed network management tasks and their corresponding TCP/IP management and Compaq Tru64 UNIX command formats. |
| Compaq TCP/IP Services for OpenVMS Tuning and Troubleshooting | This manual provides information about how to isolate the causes of network problems and how to tune the TCP/IP Services software for the best performance. |
| Compaq TCP/IP Services for OpenVMS Guide to IPv6 | This manual describes the IPv6 environment, the roles of systems in this environment, the types and function of the different IPv6 addresses, and how to configure TCP/IP Services to access the 6bone network. |
For additional information about TCP/IP Services for OpenVMS, access the Compaq OpenVMS World Wide Web site at the following URL:
This manual describes concepts that are specific to the Compaq TCP/IP Services for OpenVMS implementation of TCP/IP. If you are looking for a comprehensive overview of the TCP/IP protocol suite, you might find the following useful:
Comer, Douglas E. Internetworking with TCP/IP Volume 1: Principles, Protocols, and Architecture. 4th edition. Englewood Cliffs, NJ: Prentice Hall; ISBN: 0130183806, 2000.
Stevens, W. Richard. UNIX Network Programming Volume 1: Networking APIs: Sockets and XTI. Second edition, Prentice Hall PTR; ISBN: 013490012X, 1997
Compaq welcomes your comments on this manual. Please send comments to either of the following addresses:
| Internet: openvmsdoc@compaq.com |
| Mail: Compaq Computer Corporation |
| OSSG Documentation Group, ZKO3-4/U08 |
| 110 Spit Brook Rd. |
| Nashua, NH 03062-2698 |
Visit the following World Wide Web address for information about how to order additional documentation:
The following conventions are used in this manual:
- Ctrl/ x
Indicates that you must hold down the key labeled Ctrl while you press another key or a pointing device button.
- PF1x
A sequence such as PF1x indicates that you must first press and release the key labeled PF1 and then press and release another key or a pointing device button.
- Return
In an example, a key name enclosed in a box indicates that you press that key.
- …
A horizontal ellipsis in examples indicates one of the following possibilities:
A vertical ellipsis indicates the omission of items from a code example or command format; the items are omitted\par because they are not important to the topic being discussed.
- ( )
In command format descriptions, parentheses indicate that you must enclose choices in parentheses if you specify more than one.
- [ ]
In command format descriptions, brackets indicate optional choices. You can choose one or more items or no items. Do not type the brackets on the command line. However, you must include the brackets in the syntax for OpenVMS directory specifications and for a substring specification in an assignment statement.
- |
In command format descriptions, vertical bars separate choices within brackets or braces. Within brackets, the choices are optional; within braces, at least one choice is required. Do not type the vertical bars on the command line.
- { }
In command format descriptions, braces indicate required choices; you must choose at least one of the items listed. Do not type the braces on the command line.
- Type
This typeface represents the introduction of a new. It also represents the name of argument an attribute, or a reason.
- italics
Italic text indicates important information, complete titles of manuals, or variables. Variables include information that varies in system output (Internal error number), in command lines (/PRODUCER=name), and in command parameters in text (where (dd) represents the predefined par code for the device type.
- UPPERCASE TEXT
Uppercase text indicates a command, the name of a routine, the name of a file, or the abbreviation for a system privilege.
- Monospace text
Monospace type indicates code examples and interactive screen displays.
In the C programming language, monospace type in text identifies the following elements: keywords, the names of independently compiled externalfunctions and files, syntax summaries, and references to variables or identifiers introduced in an example.
- –
A hyphen at the end of a command format description, command line, or code line indicates that the command or statement continues on the following line.
- numbers
All numbers in text are assumed to be decimal unless otherwise noted. Nondecimal radixes---binary, octal, or hexadecimal---are explicitly indicated.
The Compaq TCP/IP Services for OpenVMS product is the OpenVMS implementation of the industry-standard TCP/IP suite of communications protocols. With TCP/IP Services, users, administrators, and programmers can perform tasks from anywhere in the network, such as:
Application development: developing TCP/IP applications for communication between local and remote hosts
Accessing user information: accessing information about other users logged onto local or remote hosts
Remote management: managing and monitoring the network and applications from remote hosts
Remote printing: sending print jobs to a remote printer, and receiving print jobs from a remote host
Networking booting: providing boot service for a remote host
Users can perform internetworking tasks seamlessly without worrying about the hardware details of each individual network. The TCP/IP Services provides interoperability and resource sharing between OpenVMS systems, UNIX systems, and other systems that support the TCP/IP protocol suite and Sun Microsystems Network File System (NFS). Internet hosts share data and resources by using standard TCP/IP protocols over a number of network hardware configurations including Ethernet, Fiber Distributed Data Interface (FDDI), Token Ring, and asynchronous transfer mode (ATM).
This chapter discusses the following topics. More details about these topics are provided elsewhere in this manual and in other Compaq TCP/IP Services for OpenVMS and OpenVMS documentation set manuals.
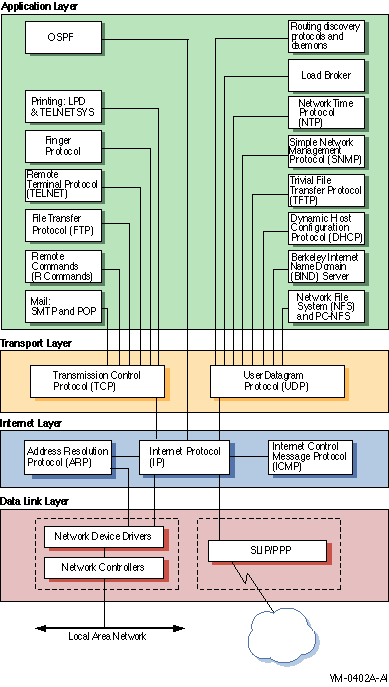
TCP/IP Services provides support for several protocols at every level of the TCP/IP model's protocol layers.
Figure 1–1 shows the various layers and protocols of the TCP/IP model. A description of each layer and protocol follows the figure.
At the base of the TCP/IP layers, the Data Link layer formats data and provides services that directly access the physical network.
This layer also receives data that is routed from the Internet layer and transmits the data to its destination, converting logical IP addressesto physical addresses of the network adapter or network interface cards (NICs) using the Address Resolution Protocol (ARP).
Some commonly used network architectures designed for the physical network are Ethernet and its variants, Token Ring, FDDI, and ATM.
A single host computer can have multiple NICs. This configuration is termed a multihomed host. Depending on your network setup, the Data Link layer's configuration may vary. For more information, see Chapter 3.
The Internet layer moves data around the internet. The Internet Protocol uses addressing to deliver and route packets across networks independently of the network cabling.
At this level, the protocols are:
The protocol also encapsulates datagram headers, sends ICMP error and control messages, and maps ARP address conversions.Routing protocols at this layer are:
For more information about these protocols, see Chapter 5.
The Transport layer enables a flow of data between two hosts. The protocols at this layer are either connection oriented, in which the protocol establishes and maintains the connection between communicating hosts to prevent errors, or connectionless, in which a one-way datagram is sent to a destination host.
The TCP/IP Services supports both transport protocols:
The connection-oriented protocol, Transmission Control Protocol (TCP) provides a reliable data flow between two hosts. TCP is used for complex, large packets that have an IP address.
The connectionless protocol, User Datagram Protocol (UDP) provides a much simpler service to the Application layer than TCP but does not guarantee reliability. UDP is used for simple, small packets and requests for dynamic IP address assignment. UDP packets have a MAC address.
The top layer of the TCP/IP protocol suite, the Application layer handles the details of the particular application, protocol, or user command; it is not concerned with the movement of data across the network.
TCP/IP Services supports the following TCP/IP applications, protocols, and user services:
Remote Computing Services
Remote computing applications enable networked users to run software on remote systems. TCP/IP Services include the following remote computing application components:
TELNET enables remote login to other hosts in the network. Compaq TCP/IP Services provides simultaneous multiple sessions, IBM3270 terminal emulation (TN3270) and two interface formats: DCL style and UNIX style.
XDM is a network-based graphics window system based on the client/server application model. It enables a system to display information output from an application that is running on another system in the network.
The FINGER utility is used to display user information for the network.
File Transfer Services
TCP/IP Services includes the following components that let users transfer data files between local and remote hosts:
File Transfer Protocol (FTP) transfers files between hosts.
Trivial File Transfer Protocol (TFTP) downloads and transfers files. Compaq TCP/IP Services supports downloading of system image and other information to client hosts.
Resource Services
Line printer/line printer daemon (LPR/LPD) provides printing services to local and remote hosts.
TELNET print symbiont (TELNETSYM) provides remote printing services that enable OpenVMS printing features not available with the LPR/LPD print service.
Network File System (NFS) is a protocol that allows computers to access remote files as if they were local files, regardless of operating system, hardware type, or architectural differences between the local and remote systems. This is accomplished in a client/server environment where specific implementations on NFS exist on both the client and server machines.
PC-NFS is a daemon that enables access to the NFS server from a PC by providing authentication services to PC-NFS clients.
Electronic Mail Services
Communication functions such a electronic mail are vital both within an organizational internet and across the Internet worldwide. The electronic mail components of TCP/IP Services are:
Simple Mail Transfer Protocol (SMTP) is the TCP/IP standard protocol for transferring electronic mail messages from one system to another.
IMAP is the Internet Message Access Protocol. IMAP enables clients to access email messages and folders from an IMAP server and synchronize them locally. This enables a client to organize email messages and folders without continuous access to the server.
Post Office Protocol (POP) is a mail repository used primarily by PCs.
Beyond the industry-standard TCP/IP application services, TCP/IP Services provides support for the following Compaq products:
The Compaq TCP/IP Services for OpenVMS software includes the PWIP driver and the PWIPACP network ancillary control process (ACP). The PWIP driver enables communication between OpenVMS systems running both PATHWORKS server and TCP/IP Services software, and personal computers running PATHWORKS client software. It also enables the DECnet-over-TCP/IP feature, which is included with the DECnet-Plus for OpenVMS Version 6.0 and later software. For more information, see Chapter 7.
Network applications specific to the Compaq TCP/IP Services can use the following application programming interfaces (APIs):
Sockets have become a popular programming interface. The Berkeley Sockets Interface is a programming interface that provides applications with access to network communication protocols. A socket is a generalized UNIX communication endpoint on which the TCP/IP protocols have been implemented. Using the socket programming interface makes it easy to implement network applications.
OpenVMS provides support for the socket interface through the C programming language and the Compaq C Run-Time Library. The benefits of using the socket interface on the OpenVMS platform include:
For more details, refer to the Compaq TCP/IP Services for OpenVMS Sockets API and System Services Programming manual.
The standard I/O programming interface on OpenVMS uses the QIO (queue input/output) system services. QIO services provide a rich set of functions for controlling devices, and connections and for performing input (read) and output (write) operations.
The benefits of using the OpenVMS QIO interface include:
Support for the QIO interface in the following programming languages:
MACRO-32 Compaq C Compaq Fortran Compaq Ada Compaq and VAX BASIC VAX BLISS-32 Compaq COBOL VAX Pascal Compaq PL/1 Ability to handle complex applications with many concurrent connections
Robust asynchronous event handling (While sockets offer the ability to do nonblocking I/O operations, they do not offer the ability to perform asynchronous I/O.)
For more details, refer to the Compaq TCP/IP Services for OpenVMS Sockets API and System Services Programming manual.
SRI QIO Compatibility
TCP/IP Services provides support for customer applications using the INETDRIVER QIO interface developed at Stanford Research Institute (SRI) in 1980-81. An SRI QIO emulator that translates non-TCP/IP Services QIO interfaces into TCP/IP Services QIO programming interfaces can be configured by using the TCPIP$CONFIG procedure.
The RPC programming interface is an industry-standard, portable API that is an efficient alternative to using sockets for application development. Programmers do not need an in-depth knowledge of networking protocols to use RPC.
One strong point of the RPC interface is its ability to distribute functions across the network. This is done in an architecture-independent manner, thereby avoiding problems with floating-point formats and byte-address ordering that often occur when interacting between architectures.
This API includes:
For more details, refer to the Compaq TCP/IP Service ONC RPC Programming manual.
The Extensible Simple Network Management Protocol (eSNMP) API provides routines for developing applications that remotely manage and collect data from network devices such as routers, bridges, and hosts.
These network devices run software that carries out management commands that either get information from devices or set operating parameters for devices.
Other network applications send commands to network devices to perform configuration management, monitor network traffic, or troubleshoot network problems.
The SNMP API provides routines for the following functions:
The SNMP API routines are almost identical in function and interface with the routines in the Compaq Tru64 UNIX API.
For more details, refer to the Compaq TCP/IP Services for OpenVMS SNMP Programming and Reference manual.
Although TCP/IP is monitored by a number of organizations, no single entity owns this protocol; its specifications are publicly available and are constantly growing as communications requirements evolve.
The process by which the specifications evolve is through a mechanism called Requests for Comments (RFCs). When someone has an idea for a new or improved capability for TCP/IP, he or she writes a proposal, posts it on the Internet as an Internet draft, and requests comments from the networking community. After a review and revision cycle, working code is developed and an RFC becomes a standard protocol.
RFCs are available on the Internet from the Internet Network Information Center (InterNIC). The following web site provides links to several RFC international repositories, lists all RFCs, and explains how you can obtain copies:
Note that, although RFCs recommend implementation guidelines, the actual implementation of an RFC can and must differ from the RFC in minor ways. When product documentation refers to specific RFCs, be aware that the RFC only sets the standard for development. Product developers must design their software for the specific environment and requirements of their customers.
An important step in planning a network host implementation is to gain an understanding of the computing environments in which the network services will run. Compaq Tru64 UNIX implementations of TCP/IP Services are often ported to OpenVMS. As a result, they often appear to be identical. However, there are many significant differences. This chapter describes key implementation differences between UNIX and OpenVMS networks. The following topics are discussed:
Things to Consider
In planning your TCP/IP Services environment, consider the following:
The issues of working in a heterogeneous computing environment that includes OpenVMS and Tru64 UNIX operating systems are complex. Consider these concepts when evaluating or implementing an interoperability strategy:
Migration occurs when software applications are rewritten as necessary to be ported from one operating system to the other. In a general sense, not only the applications but also the users migrate to another system. Migration implies a gradual replacement of the original system with the new system.
Coexistence occurs when two or more systems, such as OpenVMS and Tru64 UNIX, are maintained as part of a larger, heterogeneous computing environment. The amount of interoperability varies with the individual configurations. It is possible to set up nearly identical network configurations, thereby reducing maintenance.
The client/server model of computing means that users running applications on their PCs and workstations are networked with larger departmental systems. The departmental systems provide a variety of services to the clients, such as access to common database, print, and backup/archive services.
To best serve this model of computing, the systems must be open. Open environments support interoperability and application portability and enable developers and users to easily use different platforms. The OpenVMS operating system is an open system with an extensive list of functions.
An open system allows the OpenVMS operating system, whether powered by Alpha or VAX, to interoperate efficiently with Compaq Tru64 UNIX and with other vendors' operating systems, particularly with Windows NT and other UNIX operating systems.
Implementing open systems means using the right middleware between the operating system and the hardware platform and applications. Consistent middleware affords interoperability and portability when and where it is needed. An open systems strategy involves a consistent middleware approach that is based on standards and is embodied in layered software and in individual operating systems, such as OpenVMS and UNIX. Compaq DCE is an example of middleware, with standard interfaces supported on both OpenVMS and UNIX. Compaq DCE, or Distributed Computing Environment, is an architecture of standard programming interfaces, conventions, and server functions that transparently distributes applications across heterogeneous networks.
As shown in Figure 2-1, OpenVMS and UNIX interoperate efficiently, especially in areas that are common to both platforms: windowing interface, standard POSIX and DCE programming interfaces, compilers, networking products, and applications.
The Network File System, or (NFS) provides a standard for the exchange of data between machines running different operating systems. NFS enables users to access directories and files on remote computers transparently, as if they were on the local system. NFS accomplishes this because it is implemented on the both the remote and the local computer.
NFS protocol achieves portability between different machines, operating systems, network architectures, and transport protocols through the use of Remote Procedure Call (RPC) and External Data Representation (XDR). For more information about RPCs and XDR, refer to the Compaq TCP/IP Services for OpenVMS ONC RPC Programming manual.
Using NFS is simple. Configuring and implementing NFS, however, are more complex. For NFS concepts and considerations, as well as detailed configuration and implementation information, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
TCP/IP Services accommodates the numerous key differences between UNIX and OpenVMS to make user interaction between the two operating systems appear transparent. This enables all systems on a heterogeneous network to store and share files and applications regardless of file specification and structure differences.
This section discusses:
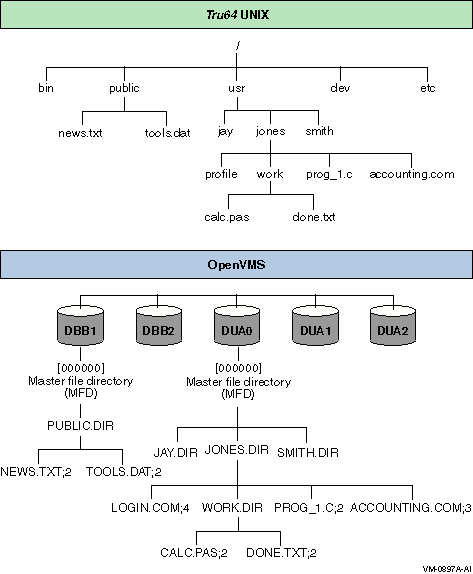
Unlike OpenVMS, the UNIX hierarchy appears as one tree (starting from the root directory, or “/”) that can be located on more than one device. Table 2-1 describes the differences between the OpenVMS and Tru64 UNIX directory hierarchies.
Table 2.1. Directory Hierarchy Differences
| OpenVMS | UNIX |
|---|---|
| Reside on one volume having one root above all directories on the volume. | Can reside on multiple volumes. |
| Device names included in file specifications. | Device names not included in file specifications. |
Figure 2-2 illustrates the differences between a UNIX file structure and an OpenVMS file structure.
There are basic differences between OpenVMS and UNIX file specifications. Table 2–2 summarizes the differences.
Table 2.2. File Specification Differences
| OpenVMS | UNIX |
|---|---|
Files are delimited in the following way: The ODS-5 file system implements extended file specifications and is a step toward improving interoperability. ODS-5 is described later in this chapter. For complete details about the ODS-5 file specification, refer to the OpenVMS product documentation. | The slash (/) is the only delimiter that the UNIX file specification format uses. The first slash in a UNIX file specification represents the root directory. Subsequent slashes separate each element of the file specification (the directories from the other directories and the file name). In theory, there is no limit to the number of directory levels in a UNIX file specification. |
OpenVMS file specification format
On a standard Files-11 On-Disk Structure Level 2 (ODS-2) volume, an OpenVMS file specification has the following format:
device:[directory.subdirectory]filename.type;version
UNIX file specification format
On a UNIX system, the file specification has the following format:
/directory/subdirectory/filename
OpenVMS and UNIX both have two types of file specifications or pathnames: absolute and relative. Table 2–3 describes the differences between the two platforms.
Table 2.3. Absolute and Relative File Specification Differences
| OpenVMS | UNIX |
|---|---|
The relative path for file calc;1 in directory usr:[jones] is: [.accounting.calc;1] The absolute path is: usr:[jones.accounting.calc;1] | The relative pathname for file calc in directory /usr/jones is accounting/calc The absolute pathname is /usr/jones/accounting/calc On UNIX systems, absolute pathnames use the entire directory path that leads to the file, beginning with the root, which is represented by an initial slash. The root directory is the first directory in the file system. All other files and directories trace their ancestry back to the root. Relative pathnames begin the directory path with the current working directory and exclude the current working directory name in the pathname. There is no initial slash in a relative pathname. |
There are fundamental differences between file names specified in OpenVMS and in UNIX. Table 2–4 describes those differences.
Table 2.4. File Specification Differences
| OpenVMS (ODS-2) | UNIX |
|---|---|
Includes, in this order: An OpenVMS file specification can have a maximum of 255 characters. The file name and file type can have up to 39 characters each and are separated by a period. For example: FILE_NAME.TXT;1 Valid characters in an OpenVMS file name or type include: A–Z, a–z, 0–9, underscore (_), hyphen (-), and dollar sign ($). The version number (preceded by a semicolon) is a decimal number from 1 to 32767; it differentiates versions of the same file. | Contains up to 1024 characters, with each element of the pathname containing up to 255 characters. UNIX file specifications have the following format: file_name.txt Some older versions of the UNIX operating system limit the size of one element to 14 characters, or have other limits that you can change if you recompile the kernel. In theory, you can use any ASCII character in a UNIX pathname except for the slash (/) and null characters. For example, avalid file name in UNIX can be: report.from.january_24 However, avoid characters (such as the pipe (|) character) that can have special meaning to the UNIX shell. |
Case sensitivity differs between the two operating systems. Table 2–5 describes the difference.
Table 2.5. Case-Sensitivity Differences
| OpenVMS (ODS-2) | UNIX |
|---|---|
Stores everything in uppercase. For example, any case variations of the following file name is stored in uppercase: CHAPTER_ONE.TXT;1 | Regards uppercase and lowercase characters as different characters. |
For example, on a UNIX system, the following file names represent three different files: |
Table 2–6 describes the file type differences between OpenVMS and UNIX.
Table 2.6. File Type Differences
| OpenVMS | UNIX |
|---|---|
Important in OpenVMS file identification The file type usually describes the kind of data in the file. | UNIX systems do not use file types. However, UNIX has certain naming conventions that resemble OpenVMS file types. |
For example, a text file typically has a file type of .TXT. All OpenVMS directories have a file type of .DIR. | For example, file names ending in txt are text files. UNIX directories do not have file types. |
Table 2–7 describes file version number differences between OpenVMS and UNIX.
Table 2.7. Version Number Differences
| OpenVMS | UNIX |
|---|---|
Every file has a version number. When a file is created, the system assigns it a version number of 1. Subsequently, when a file is edited or when subsequent versions of that file are created, the version number automatically increases by 1. Therefore, many versions of a file with the same file name can exist in the same directory. | The UNIX file system does not support automatic creation of multiple versions. In most cases, if you edit a UNIX file, the system saves only the most recently edited copy. |
For example: FILE_NAME.TXT;1FILE_NAME.TXT;2FILE_NAME.TXT;3 | For example: file_name.txt |
A link is a directory entry that refers to a file or another directory. Table 2–8 describes the differences between OpenVMS and UNIX file linking.
Table 2.8. Link Files Differences
| OpenVMS | UNIX |
|---|---|
Files can exist without links. | Files cannot exist without links. |
OpenVMS systems allows you to perform a function similar to hard links with the SET FILE/ENTER and SET FILE/REMOVE commands. The OpenVMS operating system does not maintain a count of links to a file. As a result, you can delete a file without deleting its links. | Hard links allow users to share the same file under different pathnames. A hard link cannot span file systems. On UNIX systems, any changes to the file are independent of the link used to refer to the file. The UNIX system maintains a count of the number of links to each file. If removing a link results in the link count becoming zero, the file is deleted. A file can be deleted only by removing all of its links. |
OpenVMS file systems do not support symbolic links. | Symbolic Links A symbolic link is a file that contains the name of the file to which it is connected. Symbolic links provide a path to the original file. A UNIX symbolic link can span file systems. Unlike a hard link, a symbolic link does not maintain a link count. In addition, symbolic links can exist after the file is deleted. However, the system returns an error if the symbolic link file is accessed after the file it names is deleted. |
Table 2–9 describes the differences between the OpenVMS and UNIX file structures.
Table 2.9. File Structure Differences
| OpenVMS | UNIX |
|---|---|
Supports three file structures: indexed, relative, and sequential. OpenVMS also supports the following record formats and record attributes: | Supports byte streams only. The records in UNIX text files have the same format as the OpenVMS Record Management Services (RMS) STREAM_LF record format. |
The OpenVMS and UNIX operating systems use different mechanisms for file ownership. Table 2–10 describes those differences.
Table 2.10. File Ownership Differences
The OpenVMS and UNIX operating systems use similar file protection schemes, as shown in Table 2–11.
Table 2.11. Comparison of File Protection
| Mechanism | OpenVMS | UNIX |
|---|---|---|
| User classifications | SYSTEM (S) OWNER (O) GROUP (G) WORLD (W) Classification depends on the relationship between the UIC of the accessing process and the object. | user (u) --- The user has a matching UID group (g) --- The user has a matching GID other (o) --- Any other user System category is not used; system administrators always have access to UNIX files. |
| Protection levels | READ (R) WRITE (W) EXECUTE (E) – Controls file execution and directory search access DELETE (D) | read (r) — The user has a matching UIC write (w) — Controls unlinking files to the directory. execute (x) — Controls file execution and directory search access A file is deleted if it is unlinked from the directory and had no links in other directories. Write access to the directory is refused. |
| Syntax | s:rwed, o:rwed, g:rwed, w:rwed | rwxrwxrwx The protection levels are divided into groups of three characters: |
The TCP/IP Services allows you to create a logical UNIX style file system on an OpenVMS host. Remote UNIX hosts that have NFS software can then access this file system. When a remote UNIX system accesses files, these files conform to UNIX file system rules, not to the OpenVMS rules. This ensures that existing UNIX applications work without change. The logical UNIX file system resides on a Files-11 formatted disk and is represented as a set of Files-11 files called a container file system. For information about creating a UNIX file system on an OpenVMS host, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
The UNIX file names and attributes are catalogued in the container file, one of the files in the container file system. The container file also has a representation of the UNIX directory hierarchy and a pointer to the data file for each file name. In addition to its UNIX name, each file in the container file system has a valid Files-11 file name assigned by the system. An OpenVMS directory exists for each UNIX directory stored in the container file. All files catalogued in a UNIX directory are also catalogued in the corresponding OpenVMS directory. However, the UNIX directory hierarchy is not duplicated in the OpenVMS directory hierarchy. Each UNIX file is represented as an OpenVMS data file. Therefore, OpenVMS utilities, such as BACKUP, can use standard methods to access these files.
The first step in managing your TCP/IP Services system is to decide which file system to use. NFS on OpenVMS enables you to set up and export three different kinds of file systems:
OpenVMS On-Disk Structure (ODS-2) file system, in which devices, directories, and files are stored on a Files-11 formatted disk
OpenVMS On-Disk Structure (ODS-5) file system, which enables creation and storage of files with extended file names for compatibility with other file systems, such as Windows.
UNIX, or container, file system, built on top of an OpenVMS system. If you are not familiar with OpenVMS file systems, refer to the OpenVMS System Manager's Manual: Essentials to learn how to set up and initialize a Files-11 disk. As Figure 2–2 shows, both file systems are structured as hierarchical, multilevel directories. On OpenVMS systems, the top level is called the master file directory, or MFD. This directory contains all the directories and reserved system files. The directory is named [000000]. On UNIX systems, the top-level directory is called the root, or / .
Table 2.12. NFS Server Features Available to Non-OpenVMS Clients
| Features | ODS-2 | OD2–2 with name conversion | ODS-5 | Container file system |
|---|---|---|---|---|
| Files easily shared between remote clients and local OpenVMS users | Yes | Yes | Yes | No |
| Mixed case, special characters, and extra dots in file names | No | Yes | Yes | Yes |
| Long file names | No | No | Yes | Yes |
| File names look the same to remote clients and local OpenVMS users | Uppercase to local users, lowercase to remote clients | No | Yes | N/A |
| Support for hard links, symbolic links, special files | No | No | No | Yes |
| UNIX compatible timestamps | No | No | No | Yes |
| Case-sensitive lookup | N/A | Yes | No | Yes |
The dual cataloguing of files to both OpenVMS file systems limits the set of DCL commands. OpenVMS utilities, such as BACKUP, can use standard methods to access the files. However, except for backing up and restoring files, you should not use DCL commands to manipulate files in a container file system.
Decision Point
Your file system choice depends on your environment and the user needs on the NFS client host. Consider using an OpenVMS file system if:
For More Information
For more information about the following topics, refer to the Compaq TCP/IP Services for OpenVMS Management manual:
For a list of commonly used Tru64 UNIX commands and their equivalents on OpenVMS, refer to the Compaq TCP/IP Services for OpenVMS Tuning and Troubleshooting manual.
For more details about interoperability between UNIX and OpenVMS, refer to the OpenVMS and Compaq UNIX Interoperability and Migration Guide. This guide discusses products and services, available both from Compaq and from other vendors, that might provide solutions to interoperability problems.
For more information about RPCs and XDR, refer to the Compaq TCP/IP Services for OpenVMS ONC RPC Programming manual.
For additional ACL information, refer to the OpenVMS documentation set.
There are several server and network configurations to consider before installing TCP/IP Services for OpenVMS. This chapter describes the following concepts that will enable you to make informed decisions about these configuration options:
Note
VAX development has limited continued support. VAX users should consider migrating to Alpha, if possible.
Things to Consider
In planning your TCP/IP Services for OpenVMS configurations, consider the following:
You need to consider several issues when you plan to add one or more OpenVMS Alpha systems to your OpenVMS VAX computing environment. For full details about the similarities and differences between OpenVMS Alpha and OpenVMS VAX, refer to the OpenVMS Compatibility Between VAX and Alpha guide, which is available on line at:
http://www.openvms.compaq.com/doc
The user environment on OpenVMS Alpha is virtually the same as that on OpenVMS VAX. Table 3–1 describes the similarities and differences.
Table 3.1. OpenVMS VAX and OpenVMS Alpha Similarities and Differences
| Component Similarities | OpenVMS VAX Differences | OpenVMS Alpha Differences |
|---|---|---|
DIGITAL Command Language (DCL) Essentially the same on both systems. | None | Refer to the few exceptions in the OpenVMS Compatibility Between VAX and Alpha guides available on line. |
DCL Help Most DCL help text is common to both systems. | System-specific information is identified by the phrase “On VAX.” | System-specific information is identified by the phrase “On Alpha.” |
DCL command procedures Most DCL command procedures, with commands, qualifiers, and lexical functions, work on both systems. | None | A few command procedures contain qualifiers not available on OpenVMS Alpha. |
Databases Standard databases, such as Oracle Rdb, function the same on both systems. | None | Most third-party databases available for OpenVMS VAX are also available for OpenVMS Alpha. For more information, refer to the OpenVMS Compatibility Between VAX and Alpha guide, available on line. |
Most OpenVMS VAX system management utilities, command formats, and tasks are identical on OpenVMS Alpha, with the following exceptions:
For more information about implementation differences between OpenVMS VAX and OpenVMS Alpha, refer to the OpenVMS System Manager’s Manual.
The same types of programming development tools that OpenVMS VAX programmers use are available on OpenVMS Alpha systems, such as the Linker utility, the Librarian utility, the OpenVMS Debugger (also known as the symbolic debugger),the Delta/XDelta Debugger, and run-time libraries. However, some TCP/IP Services components are available only on OpenVMS Alpha, including:
These components are introduced later in this manual.For details about the similarities and differences between the programming environment on VAX and Alpha, refer to A Comparison of System Management on OpenVMS AXP and OpenVMS VAX, which provides guidelines for developing applications that run on both OpenVMS VAX and OpenVMS Alpha, as well as additional guidelines for systems that run in a mixed-architecture OpenVMS Cluster.
Compaq TCP/IP Services for OpenVMS supports OpenVMS Cluster systems and the use of cluster aliases. The network sees the cluster as one system with one name, the cluster alias. A remote host can use the cluster alias to address the cluster as one host, or it can use the host name of a cluster member to address a cluster member individually.
In a DECnet network, it is convenient to be able to treat nodes within a homogeneous OpenVMS Cluster as though they were a single node. You can do this by establishing an alias node identifier for the cluster. You can specify the alias node identifier as either a unique node address or a corresponding node name. Any member node can elect to use this special node identifier as an alias while retaining its own unique node identification. For more information on the use of the optional cluster alias node identifier, refer to the DECnet for OpenVMS Networking Manual.
Note
DECnet–Plus software is not required in an OpenVMS Cluster configuration. However, DECnet–Plus is necessary if internode process-to-process communication using DECnet mailboxes is needed. For more information about DECnet-Plus in an OpenVMS Cluster configuration, refer to the Guidelines for OpenVMS Cluster Configurations manual.
For load balancing, an OpenVMS Cluster can consist entirely of OpenVMS Alpha nodes or of a combination of OpenVMS VAX and OpenVMS Alpha nodes.
You can have numerous OpenVMS Cluster configurations. For complete information about supported devices and configurations, refer to Guidelines for OpenVMS Cluster Configurations and the OpenVMS Cluster Software Software Product Description (SPD). For complete information about setting up and using an OpenVMS Cluster environment, refer to the OpenVMS Cluster Systems manual.
Failover capability is the hallmark of a cluster environment. If one computer , or node, in the cluster fails, the others can assume its functionality and continue. This is called automatic failover.
Each node (as a member of the host configuration in the cluster) retains a separate IP address. This is beneficial for troubleshooting the individual node because you can ping the specific node to see whether it is running.
All of the TCP/IP services support automatic failover and can run on multiple nodes in an OpenVMS Cluster. For example, if more than one node in the cluster is running the NFS server, the cluster can appear to the NFS client as a single host. For more information about configuring a specific service for cluster failover, refer to the particular service in the Compaq TCP/IP Services for OpenVMS Management guide.
Load balancing using the TCP/IP Services is defined by the load broker. The load broker is a configurable, calculated, load-balancing mechanism for distributing the work load among DNS (Domain Name System, which maintains and distributes information about Internet hosts) cluster members. For more information about DNS, see Chapter 5.
Unlike round-robin scheduling (the default method used by most DNS name servers, in which each individual node in the cluster is polled in a continual, specific order), the load broker takes into account the load on all DNS cluster participants. The load broker polls DNS cluster members and updates the metric server accordingly.
When the load broker starts, it reads its configuration file and starts polling DNS cluster members. The load broker exchanges messages with DNS cluster members that run the metric server, which calculates the current load on a DNS cluster host by using a specific equation. The metric server calculates the current rating and reports it when polled by the load broker. Periodically, the load broker sorts the list of addresses based on metric rating reports, drops the systems that do not respond after being polled three times, and compares a subset of the list with the name server information.
To do the comparison, the load broker sends a host lookup request to the specified name server. If the lists are the same, the load broker does not make changes. If the lists are different, the load broker updates the name server data by sending a dynamic update request to the specified name server. The name server uses round-robin scheduling to further balance the load across the members of a DNS cluster. Thus, every consecutive request for translating the DNS cluster name results in a returned list, is rotated by one.
For specific information about configuring the load broker, starting and stopping the metric server, and troubleshooting, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
Although host computers can have several network interface cards (NICs) installed, you can configure the host through a single, primary interface. This section introduces the following concepts:
Individual host computers can have multiple network interface cards per computer. Such a computer is called multihomed. These physical interfaces can be connected to different types of networks, such as Ethernet, FDDI, Token Ring, asynchronous transfer mode (ATM), Gigabit Ethernet, and serial communications lines. Each physical interface is associated with one device driver (network interface). A single network interface can have more than one IP address.
Note
If a host has multiple interfaces under DHCP (Dynamic Host Configuration Protocol) control and receives a different host name from a DHCP server on each of the DHCP-controlled interfaces, the DHCP client uses the host name it receives on the primary interface to configure the host name for the client. For more information about DHCP, see Chapter 5.
Although you can have multiple physical interfaces on a single computer, some of the parameters that are configurable by DHCP are interface specific. Examples of interface-specific parameters are the IP address and subnet mask. However, most DHCP configurable parameters are systemwide configurable parameters. Examples of systemwide parameters are the host name and DNS domain name. The TCP/IP Services DHCP client supports controlled configuration of systemwide configurable items by designation of a primary interface.
The primary interface is the interface on which the DHCP client uses systemwide parameters received from the DHCP server to configure the system. Systemwide parameters received on an interface that is not designated as primary are not configured on your system by the server. Although only one interface on a system is designated as the primary DHCP interface, the system is not required to have any interface designated as primary.
If a system has multiple interfaces and only one is under DHCP control, you can configure the systemwide parameters manually. DHCP client uses the following rules to resolve conflicts:
The only-one-primary-interface rule
This rule solves the potential conflict between two DHCP controlled interfaces on a host getting different systemwide parameter values. To resolve the conflict, you designate one interface to be the primary interface and the parameters that you receive on that interface are the values the DHCP client uses to configure the system. TCP/IP Services does not let you designate two primary interfaces.
The primary-interface-not-required rule
This rule solves the problem of DHCP configuring interfaces with an IP address but also keeping manual control of the systemwide parameters. In this case, the DHCP client does not designate the interface as the primary interface, and it ignores any systemwide parameters it receives from a DHCP server.
For details about configuring multiple interfaces, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
To use extended routing, you can define pseudointerfaces. A pseudointerface is a data structure that extends subnet routing using a network interface. Each network interface has one name and at most nine pseudointerface names. Each network interface and pseudointerface has its own IP address, network mask, and broadcast mask.
Like an interface, the name of an internet pseudointerface consists of three alphabetic characters, followed by the pseudointerface unit number in the range of 0 through 255. The first two characters are the same as the two characters in the internet interface name (interface type and interface class). The third character identifies the controller letter that corresponds to the OpenVMS hardware controller. For more information about interface names, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
A serial connection is made between two systems using modems and telephone lines or other serial lines. TCP/IP Services supports serial connections using PPP (Point-to-Point Protocol) and SLIP (Serial Line Internet Protocol). SLIP includes CSLIP (compressed SLIP). You can use any standard OpenVMS terminal device as a PPP or a SLIP line. However, PPP is available for OpenVMS Alpha systems only.
One of the largest applications for IP over serial lines is dialup access. With this type of configuration, your OpenVMS host answers calls and establishes a connection initiated by a user on a client host. The client host can be another OpenVMS system, a UNIX system, or a PC. Alternatively, users on your host can originate the dialup connection to a remote host or terminal server that is running the same protocol. Dedicated serial lines running PPP or SLIP can also be used to connect separate LANs into a single WAN. In such a configuration, the host at each end of the serial connection is always the same; no other hosts are allowed to connect to either serial device.
If your OpenVMS system is part of a large network, you will probably use both PPP and SLIP for your serial connections. As an Internet standard, PPP is often preferred because it ensures interoperability between systems from a wide variety of vendors. PPP provides a way for your OpenVMS Alpha system to establish a dynamic IP network connection over a serial line without additional router or server hardware.
SLIP has been in use for a longer period of time than PPP and is available for most terminal servers and in most PC implementations of TCP/IP. Because SLIP and PPP do not communicate with each other, hosts must use the same protocol in order to communicate. For example, if your terminal server supports only SLIP, remote hosts that connect through this server must also use SLIP. For more information about configuring serial lines, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
For More Information
For more information about the following topics, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
For detailed descriptions of OpenVMS Alpha and VAX similarities and differences, refer to A Comparison of System Management on OpenVMS AXP and OpenVMS VAX.
For complete information about supported devices and configurations, refer to the Guidelines for OpenVMS Cluster Configurations and the OpenVMS Cluster Software Software Product Description (SPD). For complete information about setting up and using an OpenVMS Cluster environment, refer to the OpenVMS Cluster Systems manual.
The OpenVMS operating system contains a number of features that are of specific benefit to the TCP/IP environment. This chapter discusses the following topics related to these features:
Things to Consider
In planning your TCP/IP Services for OpenVMS, consider the following:
The TCP/IP Services Management Control Program is a comprehensive, easy-to-use network management tool that includes more than 100 OpenVMS commands. TCP/IP Services provides this management command interface to configure and modify parameters of components, configure customer-developed services, enable and disable running components, and monitor the running software
To start the management control program, enter the following command:
$ TCPIPTCPIP>
At the TCPIP> prompt, you can enter commands such as the following:
You can also use UNIX management commands to manage some components of TCP/IP Services.
To use UNIX management commands at the DCL prompt, run the following command procedure:
$ @SYS$MANAGER:TCPIP$DEFINE_COMMANDS
Then enter UNIX commands as you would on a Tru64 UNIX system.
TCP/IP management commands are described fully in the Compaq TCP/IP Services for OpenVMS Management Command Reference manual, and in the TCP/IP Services online help.
TCPIP> HELP
To exit the management control program, enter the following command:
TCPIP> EXIT
To obtain information about TCP/IP Services, enter the following command at the DCL prompt:
$ HELP TCPIP_SERVICES
Logical names allow you to customize component behavior. Logical names can point to directories, database files, and log files.
To define a logical name, enter the following DCL command:
$ DEFINE logical-name
For more information about these logical names, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
The TCPIP$CONFIG database predefines logical names for various databases. During the menu-driven installation procedure, the software configures either the components you select or all of the TCP/IP Services software components. These defaults are designed to get your system up and running as an internet host with minimal effort. TCPIP$CONFIG creates the database files.
After the initial configuration of a component, you can use logical names to modify the settings of the component-specific parameters. Many logical names are defined as “existence logical names”; that is, they can be either on or off. Any value associated with them is ignored. Others require a value of text string as a definition. Every logical name has a default setting.
For more information about how TCP/IP Services components uses logical names, see relevant chapters in this manual and refer to the Compaq TCP/IP Services for OpenVMS Management guide.
TCP/IP Services for OpenVMS provides network-specific enhancements to the OpenVMS System Dump Analysis (SDA) tool. For more information about SDA enhancements, refer to DCL online help.
If your system fails, you can run the SDA tool on system reboot to analyze the system crash dump. You can do this by adding command lines to the SYSTARTUP_VMS.COM procedure.
If you are unable to analyze a process dump with the debugger, use the System Dump Analyzer (SDA) utility. Refer to the ANALYZE/CRASH command in online help for more information. For example:
$ ANALYZE/CRASH billsystem.dmp
OpenVMS (TM) Alpha system dump analyzer...analyzing a compressed process dump...
Dump taken on 24-JUL-2002 12:03:40.95SDA>
For details, refer to the OpenVMS VAX System Dump Analyzer Utility Manual and the OpenVMS Alpha System Dump Analyzer Utility Manual.
You can keep log files of events, changes, and other configuration data in two ways.
System messages are saved to either one of these utilities. Both are described in this section.
Any terminal that is connected to the operating system can be established as an operator’s terminal if OPCOM (operator communication manager) is running. When an operator who is logged in to an account with OPER privilege enters the REPLY/ENABLE command at the designated terminal, that terminal can be used to respond to user requests and to monitor device status. Operator messages are displayed on the system console terminal unless the terminal is explicitly disabled as an operator’s terminal.
To set up a terminal to receive OPCOM messages, enter the following command:
$ REPLY/ENABLE
Event logging can help you manage the TCP/IP Services software. By default, user-defined services do not log events, but event logging is enabled by default for all supplied services. You can configure the product to log events to the operator’s console or to a log file, or to both. Every component has a default log file. For more information about log files, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
To set up event logging, enter the following command:
TCPIP> SET SERVICE service-name /LOG_OPTIONS=ALL
For a list of all the logging options, refer to the SET SERVICE command description in the Compaq TCP/IP Services for OpenVMS Management Command Reference manual.
Some product components provide additional event logging capabilities. For more information, see the relevant chapters in this manual.
OpenVMS implements On-Disk Structure Level 5 (ODS-5). This structure provides the basis for creating and storing files with extended file names. The format was introduced for compatibility with other file systems, such as Windows. You can choose whether or not to convert a volume to ODS-5 on your OpenVMS Alpha systems.
The ODS-5 volume structure provides the following features:
These features are described in detail in the OpenVMS product documentation.
ODS-5 provides enhanced file-sharing capabilities for TCP/IP Services as well as for Advanced Server for OpenVMS (or PATHWORKS for OpenVMS), DCOM, and Java™ applications. Once ODS-5 volumes are enabled, some of the new capabilities can impact certain applications or layered products as well as some areas of system management.
The following sections summarize how the enabling of ODS-5 volumes can impact system management, users, and applications.
RMS access to deep directories and extended file names is available only on ODS-5 volumes mounted on OpenVMS Alpha Version 7.2 systems and higher. Compaq recommends that ODS-5 volumes be enabled only on homogeneous OpenVMS Alpha clusters. If ODS-5 is enabled in a mixed-version or mixed-architecture OpenVMS Cluster, the system manager must follow special procedures and must be aware of the following specific restriction: users must access ODS-5 files and deep directories from OpenVMS Alpha systems only because these capabilities are not supported on earlier versions of the operating system.
Users on OpenVMS Alpha systems can take advantage of all Extended File Specifications capabilities on ODS-5 volumes that are mounted on those systems. A user on a mixed-version or mixed-architecture OpenVMS Cluster is subject to some limitations in ODS-5 functionality.
For detailed information about mixed-version or mixed-architecture support, refer to the OpenVMS product documentation.
You can select ODS-5 functionality on a volume-by-volume basis. If ODS-5 volumes are not enabled on your system, all existing applications will continue to function as before. If ODS-5 volumes are enabled, be aware of the following changes:
OpenVMS file handling and command-line parsing are modified to enable them to work with extended file names on ODS-5 volumes and maintain compatibility with existing applications. The majority of existing, unprivileged applications will work with most extended file names, but some applications might need modifications to work with all extended file names.
Privileged applications that perform filename parsing and need to access ODS-5 file names or volumes should be analyzed to determine whether they require modification.
On ODS-5 volumes, existing applications and layered products that are coded to documented interfaces, as well as most DCL command procedures, should continue to work without modification.
However, applications that are coded to undocumented interfaces or that include any of the following might need to be modified to function as expected on an ODS-5 volume:
- Internal knowledge of the file system, including knowledge of:
Data layout on the disk Contents of file headers Contents of directory files File name parsing tailored to a particular on-disk structure.
Assumptions about the syntax of file specifications, such as the placement of delimiters and legal characters.
Assumptions about the case of file specifications. Mixed-case and lowercase file specifications are not converted to uppercase. This can affect string-matching operations.
Resource sharing lets users access network printers as if they were directly connected to the user’s local systems. With resource sharing, users can access these resources directly after making the initial connection. This is different from file transfer programs in which files must be transferred completely from the remote system before they can be used.
The printer-sharing components of TCP/IP Services include:
Line printer/line printer daemon (LPR/LPD), which provides print services to remote and local hosts.
The TELNET print symbiont (TELNETSYM) provides remote printing services that enables OpenVMS printing features not available with the LPR/LPD print service.
PC-NFS, which provides authentication and print services for personal computers running PC-NFS.
The Compaq TCP/IP Services for OpenVMS software provides network printing through LPR/LPD. The LPR/LPD service has both a client component (LPR) and a server component (LPD). LPD provides remote printing services for many client hosts, including OpenVMS, UNIX, and Windows NT client hosts. Each print queue is either local or remote. Local print queues handle inbound jobs; remote print queues handle outbound jobs for remote printers.
The print setup utility (TCPIP$LPRSETUP) does the following:
Users working on UNIX clients typically enter the lpr command.
To use the Compaq TCP/IP Services for OpenVMS network printer services, you need the following:
Both the client component (LPR) and the server component (LPD) are partially included in an OpenVMS queue symbiont. The client is activated when you use one of the following commands
The LPD server is activated when a remote user submits a print job to a printer that is configured on the OpenVMS server. The LPD server consists of the following two components:
LPD receiver—a process that handles the incoming request from the remote system over the network. The LPD receiver copies the control file (CF) and data file (DF) that represent the print job to the requested printer’s LPD spool directory, and places the control file in the print queue for further processing. The receiver also handles LPQ and LPRM functions from remote clients.
LPD symbiont—parses the print job’s control file, and submits the data files to the designated local printer’s print queue.
The same LPD symbiont image is used for both client and server. It acts as the client on queues that are set up for remote printers, and it acts as the server on the local LPD queue. The LPD uses the printcap database to process print requests. The printcap database, located in SYS$SPECIFIC:[TCPIP$LPD]TCPIP$PRINTCAP.DAT, is an ASCII text file that defines the print queues. The printcap entries are similar in syntax to the entries in a UNIX /etc/printcap file.
Use the printer setup program LPRSETUP to configure or modify printers. The setup program creates spool directories and log files based on the information you supply. For more information and example setup listings, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
For more information about the following network printing services, refer to the Compaq TCP/IP Services for OpenVMS User’s Guide:
The TELNET print symbiont (TELNETSYM) provides remote printing services that enables OpenVMS printing features not available with the LPR/LPD print service. With TELNETSYM, the local OpenVMS system drives a remote printer as if it were directly connected. This is achieved by attaching a printer to a remote TCP/IP terminal server. The TELNET print symbiont has the following functions:
Note
TELNET does not work with terminal servers that use only the local area transport (LAT) protocol. The terminal server must support TCP/IP.
The system that originates the print jobs handles the standard print control functions, such as header-page generation, pagination, queuing, and handling of multiple forms. TELNETSYM extends the OpenVMS print symbiont by redirecting its output to a network channel.
Each TELNETSYM process can control up to 16 print queues. You can control the maximum number of print queues by defining the TCPIP$TELNETSYM_STREAMS logical.
For detailed information about configuring and managing TELNETSYM, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
A serial connection for a remote printer is made between a system and a serial line printer. Compaq TCP/IP Services for OpenVMS supports serial connections using the PPP (Point-to-Point Protocol) and SLIP (Serial Line IP), or CSLIP protocols. You can use any standard OpenVMS terminal device as a PPP or a SLIP line. If the remote system is configured as a gateway to a network, local users can also reach other systems on that network through the serial connection. For more information about serial line configurations, see Chapter 3.
Because everyone on a network uses print services, make sure that network print operations are set up efficiently and cost effectively. The choices that you need to make might include the following:
Determine which printers you want to make available to your server community. Some considerations regarding printers include:
Select printers that are closest to the physical location of users who require their output.
You might want to restrict access to expensive-to-use printers rather than make them available to all network users. Conversely, using one network printer for several groups in a building is less expensive than using separate printers for each group in the building.
Users who frequently print graphics require printers with higher resolution. Groups who usually print text files can use lower-resolution printers.
A computer can act simultaneously as a print server and a file server. The decision to combine print and file servers might depend on security concerns. Although printers should always be available to their users, you might want to locate a file server in a secure place. Regardless of the size of your network, you most likely will install printers on a few select computers. The only special hardware requirement for print servers is that, if you are using parallel or serial printers, the print servers must have the correct output ports.
Unlike parallel and serial devices, printers with built-in network adapter cards do not have to be adjacent to the print server. Network-interface printers are attached to the network through a built-in adapter card. The location of this type of printer has no effect on printing performance, provided that users and printers are not on opposite sides of a network bridge. A Compaq Advanced Server print server can control a virtually unlimited number of network-interface printers.
The Compaq Advanced Server makes printers available to network users through print shares. In addition, you can use a generic queue when several like printers are available to the user. A generic queue can point to several execution queues and is used to distribute printer work load among several like printers by routing a print job to the first available printer through that printer's execution queue. (If you manage the shared printers from Windows NT, the Advanced Server allows you to set up a printer pool, which is similar in function to an OpenVMS generic queue.)
You can use the Advanced Server ADMINISTER command line interface to add printers (as print queues) and print shares to the Advanced Server and to manage them. Alternatively, beginning with Version 7.3 of the Advanced Server for OpenVMS, you can configure the server to allow management of shared printers from Windows NT using the Windows NT print services. The default is to use the Advanced Server ADMINISTER command line interface.
Each print share points to a single print queue with the same name as the share. Permissions that you assign to the share are applied automatically to the associated print queue. As with any other shared resource, a share can be accessed over the network by users who have the appropriate permissions. Four types of permissions apply to print shares: Print (the default), None (no access), Manage Documents, and Full (full control).
For more information about sharing network printers, refer to the Compaq Advanced Server for OpenVMS Concepts and Planning Guide.
The PC-NFS server provides authentication and print services for PCs running NFS. Users on a PC client can associate the name of the PC printer with an OpenVMS print queue and can print files to the associated queue. However, Compaq recommends that PC clients use other mechanisms for accessing OpenVMS print queues.
To access the NFS server, PC users must have an entry in the proxy database and must have corresponding OpenVMS accounts on the server. For more information about configuring PC-NFS, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
For More Information
For detailed information about configuring and managing TELNETSYM, LPD, and PC-NFS, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
For more information about network printing services, refer to the Compaq TCP/IP Services for OpenVMS User’s Guide.
For more information about the management control commands and for a list of all the logging options within the SET SERVICE command, refer to the Compaq TCP/IP Services for OpenVMS Management Command Reference manual or to online help.
For complete information about ODS-5 features, refer to the OpenVMS documentation set.
For more information about sharing network printers, refer to the Compaq Advanced Server for OpenVMS Concepts and Planning Guide.
For more information about preinstallation tasks and the step-by-step installation, refer to the Compaq TCP/IP Services for OpenVMS Installation and Configuration guide.
This chapter describes key concepts for the following network server features:
Things to Consider
In planning your TCP/IP Services for OpenVMS, consider the following:
The Network Time Protocol (NTP) synchronizes time and coordinates time distribution throughout a TCP/IP network. TCP/IP Services NTP software is an implementation of the NTP Version 4 specification and maintains compatibility with NTP Versions 1, 2, and 3.
Time synchronization is important in client/server computing. For example, systems that share common databases require coordinated transaction processing and timestamping of instrumental data.
Synchronized timekeeping means that hosts with accurate system timestamps send time quotes to each other. Hosts running NTP can be either a time server or a time client, although they often are both a server and a client. NTP does not attempt to synchronize clocks to each other. Rather, each server attempts to synchronize to Coordinated Universal Time (UTC) using the best available source and the best available transmission paths to that source. NTP expects that the time being distributed from the root of the synchronization subnet is derived from some external source of UTC (for example, a radio clock).
If your network is isolated and you cannot access other NTP servers on the internet, you can designate one of your nodes as the reference clock to which all other hosts will synchronize.
Running an NTP server is optional. If you do set up an NTP server, you must decide whether it will be the authoritative server or whether you will get time from another server.
In the NTP environment, time is distributed through a hierarchy of NTP time servers. Each server adopts a stratum that indicates how far away it is operating from an external source of UTC. NTP times are an offset of UTC. Stratum 1 servers have access to an external time source, usually a radio clock. A stratum 2 server is one that is currently obtaining time from a stratum 1 server; a stratum 3 server gets its time from a stratum 2 server, and so on. To avoid long-lived synchronization loops, the number of strata is limited to 15.
Stratum 2 (and higher) hosts might be company or campus servers that obtain time from some number of primary servers and provide time to many local clients. In general:
Internet time servers are usually stratum 1 servers. Other hosts connected to an internet time server have stratum numbers of 2 or higher and may act as time servers for other hosts on the network. Clients usually choose one of the lowest accessible stratum servers from which to synchronize.
The OpenVMS system clock is maintained as a software timer with a resolution of 100 nanoseconds, updated at 10-millisecond intervals. A clock update is triggered when a register, loaded with a predefined value, has decremented to zero. Upon reaching zero, an interrupt is triggered that reloads the register, and repeats the process.
The smaller the value loaded into this register, the more quickly it reaches zero and triggers an update. In such an instance, the clock runs more quickly. A larger value means more time between updates; therefore, the clock runs more slowly. The amount of time between clock updates is known as a clock tick.
Once NTP has selected a suitable synchronization source, NTP compares the source’s time with that of the local clock. If NTP determines that the local clock is running ahead of or behind the synchronization source, NTP uses a general drift mechanism to slow down or speed up the clock as needed. NTP accomplishes this by issuing a series of new clock ticks. For example, if NTP detects that the local clock is drifting ahead by +0.1884338 second, it issues a series of new ticks to reduce the difference between the synchronization source and the local clock.
If the local system time is not reasonably correct, NTP does not set the local clock. For example, if the new time is more than 1000 seconds off in either direction, NTP does not set the clock. In this case, NTP logs the error and shuts down.
NTP maintains a record of the resets it makes along with informational messages in the NTP log file, TCPIP$NTP_RUN.LOG. For more details about event logging and for help interpreting an NTP log file, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
Fore information regarding operating system and daylight saving time issues, refer to the OpenVMS documentation set.
As the system manager of the local host, you determine which network hosts to use for synchronization and for populating an NTP configuration file with a list of the participating hosts.
You can configure NTP hosts in one or more of the following modes:
This mode indicates that the local host wants to obtain time from the remote server and is willing to supply time to the remote server, if necessary. This mode is appropriate in configurations that involve a number of redundant time servers interconnected through diverse network paths. Most internet time servers use this mode.
This mode indicates that the local host wants to obtain time from the remote server but it is not willing to provide time to the remote server. Client mode is appropriate for file server and workstation clients that do not provide synchronization to other local clients. In general, hosts with a higher stratum use this mode.
This mode indicates that the local server will send periodic broadcast messages to a client population at the broadcast/multicast address specified. Normally, this specification applies to the local server that is operating as a sender. To specify broadcast mode, use a broadcast declaration in the configuration file.
For information about additional modes, refer to the TCP/IP Services release notes.
Your system might be using the Distributed Time Synchronization Service (DTSS). DTSS is provided as an option with DECnet-Plus and the Distributed Computing Environment (DCE). If you are using DTSS, you must use the procedures supplied with DTSS to set time zone information.
If you are running Version 7.3 or later, you can disable DTSS in favor of running NTP. Define the logical name NET$DISABLE_DTSS to keep DECnet-Plus DECdts from starting.
Routing is the act of forwarding datagrams based on information stored in a routing table. Routing allows traffic from your local network to reach its destination elsewhere on the internet. Hosts and gateways on a network use routing protocols to exchange and store routing information.
If the hosts on your network need to communicate with computers on other networks, a route through a gateway must be defined. All hosts and gateways on a network store information about routes in routing tables. With TCP/IP Services, routing tables are maintained on the disk and in dynamic memory.
The TCP/IP Services product provides two types of routing. You can define routes manually (static routing), or you can enable routing protocols that exchange information and build routing tables based on the exchanged information (dynamic routing).
Because static routing requires manual configuration, it is most useful when the number of gateways is limited and when routes do not change frequently. For information about manually configuring routing, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
Complex environments require a more flexible approach to routing than a static routing table provides. Routing protocols distribute information that reflect changing network conditions and update the routing table accordingly. Routing protocols can switch to a backup route when a primary route becomes unavailable, and can determine the best route to a given destination.
Dynamic routing tables use information that is received by means of routing protocol updates; when routes change, the routing protocol provides information about the changes.
Routing daemons implement a routing policy, that is, a set of rules that specify which routes go into the routing table. A routing daemon writes routing messages to a routing socket, which causes the kernel to add a new route or delete , or modify, an existing route.
The kernel also generates routing messages that can be read by any routing socket when events occur that might be of interest to the process (for example, the interface has gone down or a redirect has been received).
TCP/IP Services implements two routing daemons: the Routing Daemon (ROUTED) and the Gateway Routing Daemon (GATED). The following sections provide more information about these daemons.
Routing Daemon (ROUTED)
The ROUTED daemon (pronounced “route-dee”) supports the Routing Information Protocol (RIP). When ROUTED starts, it issues routing update requests and then listens for responses. A system that is configured to supply RIP information responds to the request with an update packet. The update packet contains destination addresses and routing metrics associated with each destination. After receiving a RIP update, the ROUTED uses the information to update its routing table.
For details about how to configure dynamic routing with ROUTED, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
Note
ROUTED supports Routing Information Protocol (RIP) V1 only. ROUTED is considered older technology, and many system administrators are replacing it with GATED.
Gateway Routing Daemon (GATED)
The GATED daemon (pronounced “gate-dee”) supports interior and exterior gateway protocols. It obtains information from several routing protocols and selects the best routes based on that information. You can configure GATED to use one or more of the protocols described in Table 5–1.
Table 5.1. GATED Protocols and RFCs
| Protocol | Description | Described in this RFC |
|---|---|---|
| Routing Information Protocol (RIP) supports both Versions 1 and 2 | RIP is a commonly used interior protocol that selects the route with the lowest metric (hop count) as the best route. | RFCs 1058, 1723 |
| Open Shortest Path First (OSPF) Version 2 | Another interior routing protocol, OSPF is a link state protocol (shortest path first). It is better suited than RIP for use in complex networks with many routers. | RFC 1583 |
| Exterior Gateway Protocol (EGP) | EGP exchanges reachability information between autonomous systems. An autonomous system is usually defined as a set of routers under a single administration, using an interior gateway protocol and common metric to route packets. Autonomous systems use exterior routing protocols to route packets to other autonomous systems. | RFC 904 |
| Border Gateway Protocol (BGP) | Like EGP, BGP exchanges reachability information between autonomous systems but supports nonhierarchical topologies. BGP uses path attributes to provide more information about each route. Path attributes can include, for example, administrative preferences based on political, organizational, or security considerations. | RFCs 1163, 1267, 1771 |
| Router Discovery | This protocol is used to inform hosts of the availability of routers that it can send packets to, and to supplement a statically configured default router. | RFC 1256 |
Note
The list in Table 5–1 is continually updated. For the latest details, refer to the Compaq TCP/IP Services for OpenVMS Software Product Description (SPD 46.46.xx).
The routing protocols described in Table 5–1 are configured in the GATED configuration file, TCPIP$GATED.CONF. This file contains statements that control tracing options, select routing protocols, manage routing information, and manage independent system routing.
Under GATED, load balancing provides for identical routes based on the reference count and use count (you can observe this through netstat -r). GATED chooses from among identical routes the one with the lowest reference count. If there is more than one lowest reference count, it uses the lowest use count.
Although ROUTED allows multiple default routes, it does not monitor interface states. Conversely, GATED monitors interface status changes; however, it does not allow multiple default routes.
For information about configuring dynamic routing with GATED, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
Dynamic Host Configuration Protocol (DHCP), a superset of the Bootstrap Protocol (BOOTP), provides a centralized approach to the configuration and maintenance of IP address space. DHCP allows system managers to configure various clients on a network from a single location.
DHCP allocates temporary or permanent IP addresses from an address pool to client hosts on the network. DHCP can also configure client parameters (such as default gateway parameter), domain name server (DNS) parameters, and subnet masks for each host running a DHCP client.
With DHCP, system managers can centralize TCP/IP network configurations and management tasks involved with network connections. DHCP makes network administration easier by allowing:
Consistent application of network parameters, such as subnet masks and default routers, to all hosts on a network
Static (permanent) mapping of hardware addresses to IP addresses
Dynamic (temporary) mapping of hardware addresses to IP addresses, where the client leases the IP address for a defined length of time
Note
An OpenVMS system running TCP/IP Services can be configured as either a DHCP server or a client, but not as both. Moreover, do not attempt to configure both BOOTP and DHCP; if you do, the configuration generates a warning message.
In addition, the TCP/IP Services implementation of DHCP includes support for DHCP server failover in an OpenVMS Cluster environment. For more information about the OpenVMS Cluster environment, refer to Chapter 3.
As a superset of BOOTP functionality, DHCP offers robust configuration services, including IP addresses, subnet masks, and default gateways.
DHCP is built on the client/server model in the following respects:
DHCP consists of two components:
When a DHCP client boots, it broadcasts a DHCP request, asking that any DHCP server on the network provide it with an IP address and configuration parameters.
A DHCP server on the network that is authorized to configure this client sends the client a reply that offers an IP address.
When the client receives the offer, it can accept it or wait for other offers from other servers on the network.
Once the client accepts an offer, it sends an acceptance message to the server.
When the server receives the acceptance message, it sends an acknowledgment with the offered IP address and any other configuration parameters that the client requested. (The server only responds to specific client requests; it does not impose any parameters on the client.)
If the dynamic address allocation method is used, the IP address offered to the client has a specific lease time that determines how long the IP address is valid.
During the lifetime of the lease, the client repeatedly asks the server to renew. If the client does not renew it, the lease expires.
Once the lease expires, the IP address can be recycled and given to another client. When the client reboots, it can be given the old address, if available, or it can be assigned a new address.
For more information about how DHCP operates, refer to RFC 2131 and RFC 1534.
With TCP/IP Services, DHCP uses dynamic and static IP address-mapping methods. Table 5–2 describes the allocation methods that service DHCP and BOOTP-only client requests.
Table 5.2. DHCP IP Address Allocation Methods
| Method | Applicable Client | Description |
|---|---|---|
| Dynamic | DHCP and BOOTP | The DHCP server assigns an IP address from an address pool to a client for a specified amount of time (or until the client explicitly relinquishes the address). Addresses no longer needed by clients can be reused. Use dynamic allocation when: For BOOTP clients, DHCP assigns dynamic IP addresses from the address pool and stores the addresses in the lease database by assigning each lease a time of infinity. |
| Static | DHCP and BOOTP | The system manager manually assigns an IP address to a client and uses DHCP to pass the assigned address to the client. Use static allocation in an error-prone environment where it is desirable to manage IP address assignment outside of DHCP control. |
| Finite | BOOTP-only | The DHCP server assigns an IP address from the pool to the BOOTP client and defines a lease time based on certain parameters you define in the SERVER.PCY file. When the lease expires, the DHCP server pings the IP address. If the server receives a reply, it extends the lease and does not offer the address to a new client. If not, the address is free and can be assigned to a new client. |
The typical network uses a combination of static and dynamic DHCP addressing. As the local system manager or network administrator, you must decide which IP addressing methods are appropriate for your specific policies and environment.
For detailed information about configuring the different types of addressing for clients on your network, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
From the client’s perspective, DHCP is an extension of the BOOTP functionality. DHCP allows existing BOOTP clients to operate with DHCP servers without having to change the client’s initialization software.
Based on the format of BOOTP messages, the DHCP message format does the following:
Messages that include a DHCP message-type option are assumed to have been sent by a DHCP client. Messages without the DHCP message-type option are assumed to have been sent by a BOOTP client.
DHCP improves the BOOTP-only functionality in the following ways:
With BOOTP, a client is identified by its unique media access control (MAC) address, which is associated with the network adapter card.
DHCP uses a client identifier (ID) to uniquely identify the client and to associate it with a lease. The client creates the client ID from one of the following types of addresses:
If the client does not include a client ID in the request, the server uses the client’s MAC address.
TCP/IP Services includes the following components enable users to transfer data files between local and remote hosts:
FTP is a TCP/IP standard, high-level protocol used to transfer files bidirectionally. FTP enables users to access files interactively, list directories on a remote host, delete and rename files on the remote host, and transfer files between hosts.
FTP also provides authentication control, which requires users or clients to correctly enter a login name and password to the server before requesting file transfers. The server can refuse access if login and password combinations are invalid.
FTP allows users who do not have a login name or a password to access certain files on a system using an anonymous login name. This functionality is called Anonymous FTP and might include one or more of the following restrictions:
Limited browsing through the file system. Users can access only the anonymous guest (or home) directory and a public directory. The public directory might contain general bulletin information to which the user has read-only access.
Access to files from (get) or copying files to (put) the guest directory only.
Delete privileges for files in the guest directory that are owned by the anonymous account.
For more information about setting up FTP, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
TFTP provides a simple, unsophisticated file transfer service. It is intended for applications that do not need complex interactions between a client and server. TFTP can be hardcoded in read-only memory to execute a network bootstrap program. Once it begins execution, TFTP allows the bootstrap program to use the same underlying protocols that the operating system uses. This makes it possible for one host to boot from a server on another physical network.
TCP/IP Services supports downloading of system images and other types of information for client hosts with TFTP.
TFTP transfers files from a TFTP server to diskless clients or other remote systems. The client initiates the file transfer. If the client sends a read request to the TFTP server, the server attempts to locate this file.
TFTP has the following characteristics:
For information about how to set up TFTP, refer to the Compaq TCP/IP Services for OpenVMS Installation and Configuration manual.
The TCP/IP Services software includes client and server implementations of the Berkeley Remote (R) command applications. These applications provide users with the following capabilities:
In addition to password authentication, the R commands use a system based on trusted hosts and users. Trusted users on trusted hosts are allowed to access the local system without providing a password.
Trusted hosts are also called equivalent hosts because the software assumes that users who have access to a remote host should be given equivalent access to the local host. The system assumes that user accounts with the same name on both hosts are ‘‘owned’’ by the same user. For example, the user logged in as BETHANY on a trusted system is granted the same access as a user logged in as BETHANY on the local system.
This authentication system requires databases that define the trusted hosts and the trusted users. On UNIX systems, these databases are:
On OpenVMS hosts, the proxy database TCPIP$PROXY.DAT defines trusted hosts and trusted users for the entire system.
Each of these topics is covered in detail in the Compaq TCP/IP Services for OpenVMS Management guide.
Unlike FTP, the RCP protocol provides no method of transferring file type information between the sender and the recipient. It transfers only length, a modified and created timestamp, protection mode, and the byte stream of file data. As a result, RCP is unable to determine the file type of a file it receives.
To revert the file type to a usable format in transfers between OpenVMS systems, if the original file is fixed length or undefined, you can change the attributes on the Stream_LF copy to correspond to the format of the original file. To do so, enter the DCL command SET FILE in the following format:
SET FILE/ATTR=(file-attribute[,...])
For example, the following command transfers an OpenVMS executable image file (with a fixed record length of 512-bytes, and makes the file executable again.
$ SET FILE/ATTR=(rfm:fix, lrl:512) rcp-copied-file.exe
You can also use a logical name to change the behavior set by the options.
Although RCP uses secure authentication for security, it has file size limitations that FTP does not have. FTP has no security; passwords are sent in ASCII. RCP sends only the length of the file (in ASCII format). OpenVMS interprets this length as a signed 32-bit integer. Therefore, files transferred using RCP must no more than (2 GB -1) bytes (0x7FFFFFF=2147483647 bytes or roughly 1 byte less than 4194304 RMS 512 byte blocks).
The Simple Network Management Protocol (SNMP) is network management technology that facilitates the management of a TCP/IP network or internet in a vendor-independent manner. SNMP enables a network administrator to manage the various network components using a set of well-known procedures understood by all components, regardless of the original manufacturers.
Configuring SNMP on your OpenVMS system allows a remote SNMP management client to obtain information about your host and to set system and network parameters.
Systems using SNMP fall into two categories:
The management console is the system that issues a query; the agents run on the system being queried. Queries are sent and received in the form of protocol data units (PDUs) inside SNMP messages, which are carried in user data protocol (UDP) datagrams. You can configure your host so that an SNMP client can obtain information about your host and perform updates on your host’s management information base (MIB) data items. For example, you can configure your host to:
Table 5–3 describes the SNMP components and the sample code supplied for custom subagent development.
| Component | Description |
|---|---|
| Master agent SNMP Version 2 | Process name: TCPIP$SNMP_n. Keeps track of managed objects and allows objects to register themselves. Sends information about these objects to remote SNMP management consoles. Also maintains a small set of variables for the MIB II component. |
| MIB II | Process name: TCPIP$OS_MIBS. Provides information about the TCP/IP protocol stack and other network activity. |
| Host Resources MIB | Process name: TCPIP$HR_MIB. Provides information about the host system. |
| MIB converter | Extracts a MIB definition in ASN.1 notation into a MIB definition (.MY) file. |
| MIB compiler | Compiles a MIB-definition files (for example, CHESS_MIB.MY) into source code templates for use in building subagents. |
| SNMP utility programs | Acts as a simple client to obtain a set of values for a MIB and to listen for and send trap messages. For information about using the MIB utility programs, refer to the Compaq TCP/IP Services for OpenVMS SNMP Programming and Reference guide. |
| SNMP subagent example | Implements an example based on the chess game; includes executable and source code. |
If the proxy setup between the SNMP server and the NFS server is not correct, the host resources MIB subagent cannot access data that has been mounted.
To ensure access to mounted data, set up a proxy to an anonymous user (for example, to TCPIP$NOBODY) on the NFS server system. For more information about adding proxy entries, refer to the Compaq TCP/IP Services for OpenVMS Management guide.
For More Information
For detailed information about the following topics, refer to the Compaq TCP/IP Services for OpenVMS Management guide:
For more information about NTP OpenVMS issues, visit the OpenVMS FAQ web site at:
http://www.openvms.compaq.com/wizard/
Search on keyword NTP. For information about NTP time settings, refer to the OpenVMS System Manager's Manual.
Mail Services are an extremely important part of TCP/IP Services. Everyone who uses the network — from administrators, to programmers, to users accesses — this service on a regular basis. This chapter describes Post Office Protocol (POP), SMTP, and IMAP.
Things to Consider
In planning your TCP/IP Services for OpenVMS mail services, consider the following:
Will OpenVMS mail headers be translated by the chosen protocol?
What types and sizes of files will the mail system encounter?
The Compaq TCP/IP Services for OpenVMS Post Office Protocol (POP) server and the SMTP server work together to provide a reliable mail service. POP is a mail repository used primarily by PCs to ensure that mail is accepted even when the PC is turned off. With POP, the PC user need not be concerned with configuring the system as an SMTP server. The user logs on to the client system’s mail application, and the POP server forwards any new mail messages from the OpenVMS NEWMAIL folder to the PC. The POP server is an OpenVMS implementation of the Post Office Protocol, Version 3 (RFC 1725) and is based on the Indiana University POP server (IUPOP3).
The POP server is assigned port 110, and all POP client connections are made to this port.
The POP server is installed with SYSPRV and BYPASS privileges and runs in the TCPIP$POP account, which receives the correct quotas from the TCPIP$CONFIG procedure. The POP server is invoked by the auxiliary server.
TCP/IP Services implements the UNIX internet daemon inetd function, through the security and event logging of the auxiliary server process. The auxiliary server simplifies application writing and manages overhead by reducing simultaneous server processes on the system. In addition, the auxiliary server does the following:
The POP server uses security features provided in the protocol and in the OpenVMS operating system, as well as additional security measures. These methods provide a secure process that minimizes the possibility of inappropriate access to a user’s mail file on the served system.
You can modify the POP server default characteristics, and you can implement new characteristics by defining logical names described in the Compaq TCP/IP Services for OpenVMS Management guide.
To access mail messages from the POP server, you configure a user name and password or the POP shared secret-password string, into your client mail application.
Your client system opens the TCP connection and attempts to access the server by entering applicable POP commands such as USER (user name) and PASS (password), or APOP (shared secret password). In addition, POP supports the UID command, which some POP clients use, in which the UID (user identification) that POP creates for each mail message is a concatenation of the user name and the date of arrival.
By default, the POP server reads mail from the user’s OpenVMS NEWMAIL folder. If you do not instruct the POP server to delete the mail, the server either moves the mail to the MAIL folder (if the logical name TCPIP$POP_USE_MAIL_FOLDER is defined) or keeps it in the NEWMAIL folder (if the logical name TCPIP$POP_LEAVE_IN_NEWMAIL is defined). These logical names are described in the Compaq TCP/IP Services for OpenVMS Management guide.
POP contains minimal support for mail messages that contain foreign formats. Such messages are usually binary and therefore are not transferred to the POP client. Instead, the POP server transfers the message headers, along with a brief message instructing the user to log in and extract the foreign message into a file. Foreign messages are moved into your OpenVMS MAIL folder; the POP server then never deletes.
Table 6–1 describes the methods the POP server process uses to authorize user access.
Table 6.1. POP User Authorization Methods
Mail message headers sent by the POP server must conform to the standard specified for SMTP in RFC 822. Because many of the messages received on an OpenVMS system are not in SMTP format (for example, DECnet mail or mail from another message transport system), the POP server builds a new set of headers for each message based on the OpenVMS message headers.
Table 6–2 describes POP headers on forwarded mail messages.
Table 6.2. Forwarded POP Mail Messages Header
| POP Message Header | Obtained From |
|---|---|
| Date: | Arrival date of message. Changed to UNIX format. |
| From: | OpenVMS message From: field. Rebuilt to ensure RFC 822 compatibility. |
| To: | OpenVMS Mail To: field. Not rebuilt. |
| CC: | OpenVMS Mail CC: field. Not rebuilt. |
| Subject: | OpenVMS Mail Subj: field. Not rebuilt. |
| X-VMS-From: | OpenVMS Mail From: field. Not rebuilt. |
| X-POP3-Server: | Server host name and POP version information. Sent only if logical name TCPIP$POP_SEND_ID_HEADERS is defined. |
| X-POP3-ID: | Message UID. Sent only if logical name TCPIP$POP_SEND_ID_HEADERS is defined. |
How POP Rebuilds the OpenVMS Mail From: Field
The most important message header is the From: header because it can be used as a destination address if a reply is requested from the POP client. Therefore, the POP server rebuilds the OpenVMS Mail From: field in compliance with RFC 822 before sending the header to the POP client.
Table 6–3 describes the types of addresses that can appear in the OpenVMS Mail From: field.