![[Compaq]](../../images/compaq.gif)
![[Go to the documentation home page]](../../images/buttons/bn_site_home.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs.gif)
![[Help on this site]](../../images/buttons/bn_site_help.gif)
![[How to contact us]](../../images/buttons/bn_comments.gif)
![[OpenVMS documentation]](../../images/ovmsdoc_sec_head.gif)
| Document revision date: 19 July 1999 | |
![[Compaq]](../../images/compaq.gif) |
![[Go to the documentation home page]](../../images/buttons/bn_site_home.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs.gif)
![[Help on this site]](../../images/buttons/bn_site_help.gif)
![[How to contact us]](../../images/buttons/bn_comments.gif)
|
![[OpenVMS documentation]](../../images/ovmsdoc_sec_head.gif)
|
|
| Previous | Contents | Index |
Move Translated Until Character
opcode srclen.rw, srcaddr.ab, esc.rb, tbladdr.ab,
dstlen.rw, dstaddr.ab
| N|| <--- srclen LSS dstlen; | |
| Z|| <--- srclen EQL dstlen; | |
| V|| <--- {terminated by escape}; | |
| C|| <--- srclen LSSU dstlen; |
| 2F | MOVTUC | Move Translated Until Character |
The source string specified by the source length and source address operands is translated. It replaces the destination string specified by the destination length and destination address operands. Translation is accomplished by using each byte of the source string as an index into a 256-byte table whose first entry address (entry number 0) is specified by the table address operand. The byte selected replaces the byte of the destination string. Translation continues until a translated byte is equal to the escape byte, or until the source string or destination string is exhausted. If translation is terminated because of escape, the condition code V-bit is set; otherwise, it is cleared.If the destination string overlaps the table, the destination string and registers R0 to R5 are UNPREDICTABLE. If the source and destination strings overlap and their addresses are not identical, the destination string and registers R0 to R5 are UNPREDICTABLE. If the source and destination string addresses are identical, the translation is performed correctly.
| R0 = | Number of bytes remaining in source string (including the byte that caused the escape); R0 is zero only if the entire source string was translated and moved without escape |
| R1 = | Address of the byte that resulted in destination string exhaustion or escape; or if no exhaustion or escape, address of 1 byte beyond the source string |
| R2 = | 0 |
| R3 = | Address of the table |
| R4 = | Number of bytes remaining in the destination string |
| R5 = | Address of the byte in the destination string that would have received the translated byte that caused the escape or would have received a translated byte if the source string were not exhausted; or if no exhaustion or escape, the address of 1 byte beyond the destination string |
Scan Characters
opcode len.rw, addr.ab, tbladdr.ab, mask.rb
| N|| <--- 0; | |
| Z|| <--- R0 EQL 0; | |
| V|| <--- 0; | |
| C|| <--- 0; |
| 2A | SCANC | Scan Characters |
The assembler successively uses the bytes of the string specified by the length and address operands to index into a 256-byte table whose first entry (entry number 0) address is specified by the table address operand. The logical AND is performed on the byte selected from the table and the mask operand. The operation continues until the result of the AND is nonzero, or until all the bytes of the string have been exhausted. If a nonzero AND result is detected, the condition code Z-bit is cleared; otherwise, the Z-bit is set.
| R0 = | Number of bytes remaining in the string (including the byte that produced the nonzero AND result); R0 is zero only if there was no nonzero AND result |
| R1 = | Address of the byte that produced the nonzero AND result; if no nonzero result, address of 1 byte beyond the string |
| R2 = | 0 |
| R3 = | Address of the table |
Skip Character
opcode char.rb, len.rw, addr.ab
| N|| <--- 0; | |
| Z|| <--- R0 EQL 0; | |
| V|| <--- 0; | |
| C|| <--- 0; |
| 3B | SKPC | Skip Character |
The character operand is compared with the bytes of the string specified by the length and address operands. Comparison continues until inequality is detected or all bytes of the string have been compared. If inequality is detected, the condition code Z-bit is cleared; otherwise, the Z-bit is set.
| R0 = | Number of bytes remaining in the string (including the unequal one) if unequal byte located; otherwise, zero |
| R1 = | Address of the byte located if byte located; otherwise, address of 1 byte beyond the string |
Span Characters
opcode len.rw, addr.ab, tbladdr.ab, mask.rb
| N|| <--- 0; | |
| Z|| <--- R0 EQL 0; | |
| V|| <--- 0; | |
| C|| <--- 0; |
| 2B | SPANC | Span Characters |
The assembler successively uses the bytes of the string specified by the length and address operands to index into a 256-byte table whose first entry (entry number 0) address is specified by the table address operand. The logical AND is performed on the byte selected from the table and the mask operand. The operation continues until the result of the AND is zero, or until all the bytes of the string have been exhausted. If a zero AND result is detected, the condition code Z-bit is cleared; otherwise, the Z-bit is set.
| R0 = | Number of bytes remaining in the string (including the byte that produced the zero AND result); R0 is zero only if there was no zero AND result |
| R1 = | Address of the byte that produced a zero AND result; if no nonzero result, address of 1 byte beyond the string |
| R2 = | 0 |
| R3 = | Address of the table |
9.2.10 Cyclic Redundancy Check Instruction
This instruction implements the calculation of a cyclic redundancy
check (CRC) string for any CRC polynomial up to 32 bits. Cyclic
redundancy checking is an error detection method involving a division
of the data stream by a CRC polynomial. The data stream is represented
as a standard VAX string in memory. Error detection is accomplished by
computing the CRC at the source and again at the destination, comparing
the CRC computed at each end. The choice of the polynomial minimizes
the number of undetected block errors of specific lengths. The choice
of a CRC polynomial is not given here.
The operands of the CRC instruction are a string descriptor, a 16-longword table, and an initial CRC. The string descriptor is a standard VAX operand pair of the length of the string in bytes (up to 65,535) and the starting address of the string. The contents of the table are a function of the CRC polynomial to be used. It can be calculated from the polynomial by the algorithm in the notes. Several common CRC polynomials are also included in the notes. The system uses the initial CRC to start the polynomial correctly. Typically, the CRC has the value zero or --1. If the data stream is represented by a sequence of noncontiguous strings, the value would vary from 0 to -1.
The CRC instruction scans the string and includes each byte of the data stream in the CRC being calculated. The instruction includes the byte of the data stream by performing a logical exclusive OR (XOR) with it and the rightmost 8 bits of the CRC. Then the instruction shifts the CRC right 1 bit and inserts a zero on the left. The instruction uses the rightmost bit of the CRC (lost by the shift) to control the logical XOR operation of the CRC polynomial with the resultant CRC. If the bit is a 1, the instruction performs a logical XOR with the polynomial and the CRC. The instruction again shifts the CRC to the right and performs a conditional logical XOR on the polynomial with the result, for a total of eight times. The actual algorithm used can shift by 1, 2, or 4 bits at a time using the appropriate entries in a specially constructed table. The instruction produces a 32-bit CRC. For shorter polynomials, the result must be extracted from the 32-bit field. The data stream must be either a multiple of 8 bits in length or right-adjusted in the string with leading zero bits.
Calculate Cyclic Redundancy Check
opcode tbl.ab, inicrc.rl, strlen.rw, stream.ab
| N|| <--- R0 LSS 0; | |
| Z|| <--- R0 EQL 0; | |
| V|| <--- 0; | |
| C|| <--- 0; |
| 0B | CRC | Calculate Cyclic Redundancy Check |
The CRC of the data stream described by the string descriptor is calculated. The initial CRC is given by inicrc; it is normally zero or --1, unless the CRC is calculated in several steps. The result is left in R0. If the polynomial is less than order 32, the result must be extracted from the low-order bits of R0. The CRC polynomial is expressed by the contents of the 16-longword table. See the notes for the calculation of the table.
| R0 = | Result of CRC |
| R1 = | 0 |
| R2 = | 0 |
| R3 = | Address 1 byte beyond the end of the source string |
polyn<n> <- {coefficient of x**{order -1-n}}
|
SUBROUTINE LIB$CRC_TABLE (POLY, TABLE)
INTEGER*4 POLY, TABLE(0:15), TMP, X
DO 190 INDEX = 0, 15
TMP = INDEX
DO 150 I = 1, 4
X = TMP .AND. 1
TMP = ISHFT(TMP,-1) !logical shift right one bit
IF (X .EQ. 1) TMP = TMP .XOR. POLY
150 CONTINUE
TABLE(INDEX) = TMP
190 CONTINUE
RETURN
END
|
CRC-16 (used in DDCMP and Bisync)
polynomial: x^16 + x^15 + x^2 + 1
poly: 120001 (octal)
initialize: 0
result: R0<15:0>
CCITT (used in ADCCP, HDLC, SDLC)
polynomial: x^16 + x^12 + x^5 + 1
poly: 102010 (octal)
initialize: -1<15:0>
result: one's complement of R0<15:0>
AUTODIN-II
polynomial: x^32+x^26+x^23+x^22+x^16+x^12
+x^11+x^10+x^8+x^7+x^5+x^4+x^2+x+1
poly: EDB88320 (hex)
initialize: -1<31:0>
result: one's complement of R0<31:0>
|
| Shift (s) | Steps per Byte (limit) | Table Index | Table Index Multiplier (i) | Use Table Entries |
|---|---|---|---|---|
| 1 | 8 | tmp3<0> | 8 | [0]=0,[8] |
| 2 | 4 | tmp3<1:0> | 4 | [0]=0,[4],[8],[12] |
| 4 | 2 | tmp3<3:0> | 1 | all |
9.2.11 Decimal String Instructions
Decimal string instructions operate on packed decimal strings.
The decimal string instructions in this section operate on the following data types:
Where the phrase "decimal string" is used, it means any of the three data types. Conversion instructions are provided between the data types. Where necessary, a specific data type is identified.
A decimal string is specified by two operands:
Each of the decimal string instructions uses general registers R0 to R3 or R0 to R5 to hold a control block that maintains updated addresses and state during the execution of the instruction. At completion, the registers containing addresses are available to the software for use as string specification operands for a subsequent instruction on the same decimal strings.
During the execution of the instructions, pending interrupt conditions are tested; if any is found, the control block is updated. The first part done is set in the processor status longword (PSL), and the instruction is interrupted (refer to Appendix E). After the interruption, the instruction resumes transparently. The format of the control block at completion is as follows:
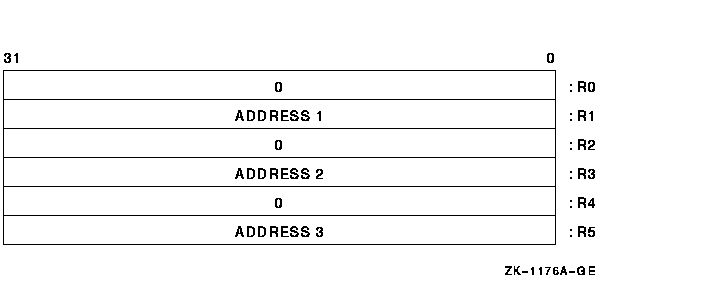
The fields ADDRESS 1, ADDRESS 2, and ADDRESS 3 (if required) contain the address of the byte containing the most significant digit of the first, second, and third (if required) string operands, respectively.
The decimal string instructions treat decimal strings as integers with
the decimal point assumed immediately beyond the least significant
digit of the string. If a string in which a result is to be stored is
longer than the result, its most significant digits are filled with
zeros.
9.2.11.1 Decimal Overflow
Decimal overflow occurs if the destination string is too short to
contain all of the digits (excluding leading zeros) of the result. On
overflow, the destination string is replaced by the correctly signed
least significant digits of the true result (even if the stored result
is --0). Note that neither the high nibble of an even-length packed
decimal string nor the sign byte of a leading separate numeric string
is used to store result digits.
9.2.11.2 Zero Numbers
A zero result has a positive sign for all operations that complete without decimal overflow, except for CVTPT, which does not change a --0 to a +0. However, when digits are lost because of overflow, a zero result receives the sign (positive or negative) of the correct result.
A decimal string with value --0 is treated as identical to a decimal
string with value +0. Thus, for example, +0 compares as equal to --0.
When condition codes are affected on a --0 result, they are affected as
if the result were +0; that is, N is cleared and Z is set.
9.2.11.3 Reserved Operand Exception
A reserved operand abort occurs if the length of a decimal string
operand is outside the range 0 to 31, or if an invalid sign or digit is
encountered in CVTSP or CVTTP. The program counter (PC) points to the
opcode of the instruction causing the exception.
9.2.11.4 UNPREDICTABLE Results
The result of any operation is UNPREDICTABLE if any source decimal string operand contains invalid data. Except for CVTSP and CVTTP, the decimal string instructions do not verify the validity of source operand data.
If the destination operands overlap any source operands, the result of
an operation will be UNPREDICTABLE. The destination strings, registers
used by the instruction, and condition codes will be UNPREDICTABLE when
a reserved operand abort occurs.
9.2.11.5 Packed Decimal Operations
Packed decimal strings generated by the decimal string instructions always have the preferred sign representation: 12 for "+" and 13 for "--". An even-length packed decimal string is always generated with a "0" digit in the high nibble of the first byte of the string.
A packed decimal string contains an invalid nibble if:
The length of a packed decimal string can be zero. In this case, the value is zero (plus or minus) and 1 byte of storage is occupied. This byte must contain a "0" digit in the high nibble and the sign in the low nibble.
The length of a trailing numeric string can be zero. In this case, no storage is occupied by the string. If a destination operand is a zero-length trailing numeric string, the sign of the operation is lost. Memory access faults do not occur when a zero-length trailing numeric operand is specified because no memory reference occurs. The value of a zero-length trailing numeric string is identically zero.
The length of a leading separate numeric string can be zero. In this case, 1 byte of storage is occupied by the sign. Memory is accessed when a zero-length operand is specified, and a reserved operand abort will occur if an invalid sign is detected. The value of a zero-length leading separate numeric string is zero.
| Previous | Next | Contents | Index |
![[Go to the documentation home page]](../../images/buttons/bn_site_home.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs.gif)
![[Help on this site]](../../images/buttons/bn_site_help.gif)
![[How to contact us]](../../images/buttons/bn_comments.gif)
|
| privacy and legal statement | ||
| 4515PRO_026.HTML | ||