This topic presents a three-part walkthrough of the shared-secret authentication protocol:
· A Walkthrough of User Authentication explains what happens when a user logs in using the default DCE login tool.
· A Walkthrough of DCE Application Authentication Using Authenticated RPC explains what happens when the logged-in user runs an application that uses authenticated RPC.
· A Walkthrough of DCE Application Authentication Using GSSAPI explains what happens when the logged-in user runs an application that uses GSSAPI.
The walkthrough is seen primarily from the user and the associated application-client side. Schematic representations of events related to the protocol accompany the discussions. The illustrations in this topic show only a high-level view (not low-level details) of what happens when a user logs in and runs an authenticated application; they are intended only to provide a general understanding of the protocol. (See the Security Volume of the Application Environment Specification/Distributed Computing for full details.)
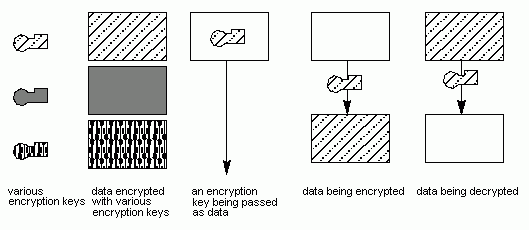
In these figures, fill patterns represent encryption key values and encrypted data. The key symbol within a box indicates that a key is being passed as data. The key symbol on a line indicates that encryption or decryption is taking place, depending on whether the resulting data is represented as encrypted or not. These conventions are shown in the following figure.
Conventions Used in Authentication Walkthrough Illustrations

Note: All computer-to-computer communications initiated by DCE security are processed through the RPC mechanism, although the integration of security with client and server RPC runtimes are not illustrated or explained in any detail here.
Finally, note that to use shared-secret protocol, you do not need to understand how it works. It is described here so that application developers can determine whether it provides sufficient security for their needs. The discussion that follows is technical and detailed and may not be of interest to every reader.
More: