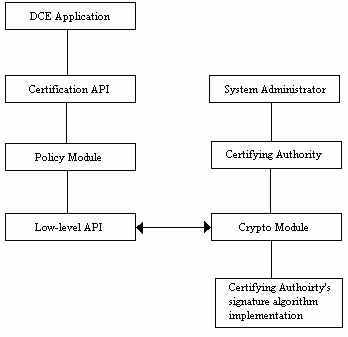
The DCE certification API is organized into four groups of routines:
· Routines for implementing and registering cryptographic modules
Cryptographic modules embody the signature algorithms that are used to sign and verify
certificates. Certificates are signed by certifying authorities (which are usually invoked by system administrators or some other specially privileged authority to create certificates), and are
retrieved (and verified) by policy modules (which are called by various applications seeking principals' public keys).
· Low-level certificate access and manipulation routines
These routines represent the primitive certificate access operations which are used in the implementation
of policy modules.
· Routines for implementing and registering policy modules
Policy modules embody the rules and mechanisms for finding the public keys that are associated with some
specific set of principals.
· High-level routines for use by applications that wish to access the certification service
The following diagram shows how these four groups of functionality are related to each other and to their two main groups of user: namely, system administrators and DCE applications.
Certification API Organization

Note that certifying authorities merely create the certificates and deposit them in a place from which they can be retrieved (the namespace); they play no part in the retrieval process itself. In fact, this could be said to be the main reason for certificates in the first place: they allow a facility such as the directory service to be used as the distribution point for public keys (that is, they allow an application to not have to arrange for getting its keys to prospective clients by some private mechanism), and at the same time they assure users that the key information that they contain has not been tampered with.