![[Compaq]](../../images/compaq.gif)
![[Go to the documentation home page]](../../images/buttons/bn_site_home.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs.gif)
![[Help on this site]](../../images/buttons/bn_site_help.gif)
![[How to contact us]](../../images/buttons/bn_comments.gif)
![[OpenVMS documentation]](../../images/ovmsdoc_sec_head.gif)
| Document revision date: 30 March 2001 | |
![[Compaq]](../../images/compaq.gif) |
![[Go to the documentation home page]](../../images/buttons/bn_site_home.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs.gif)
![[Help on this site]](../../images/buttons/bn_site_help.gif)
![[How to contact us]](../../images/buttons/bn_comments.gif)
|
![[OpenVMS documentation]](../../images/ovmsdoc_sec_head.gif)
|
|
| Previous | Contents | Index |
Subtitle directive
.SUBTITLE comment-string
comment-string
An ASCII string from 1 to 40 characters long; excess characters are truncated.
.SUBTITLE causes the assembler to print the line of text, represented by the comment-string, in the table of contents (which the assembler produces immediately before the assembly listing). The assembler also prints the line of text as the subtitle on the second line of each assembly listing page. This subtitle text is printed on each page until altered by a subsequent .SUBTITLE directive in the program.
The alternate form of .SUBTITLE is .SBTTL.
| #1 |
|---|
.SUBTITLE CONDITIONAL ASSEMBLY
|
This directive causes the assembler to print the following text as the subtitle of the assembly listing:
CONDITIONAL ASSEMBLYIt also causes the text to be printed out in the listing's table of contents, along with the source page number and the line sequence number of the source statement where .SUBTITLE was specified. The table of contents would have the following format:
| #2 |
|---|
TABLE OF CONTENTS
|
(1) 5000 ASSEMBLER DIRECTIVES (2) 300 MACRO DEFINITIONS (2) 2300 DATA TABLES AND INITIALIZATION (3) 4800 MAIN ROUTINES (4) 2800 CALCULATIONS (4) 5000 I/O ROUTINES (5) 1300 CONDITIONAL ASSEMBLY
Title directive
.TITLE module-name comment-string
module-name
An identifier from 1 to 31 characters long.comment-string
An ASCII string from 1 to 40 characters long; excess characters are truncated.
.TITLE assigns a name to the object module. This name is the first 31 or fewer nonblank characters following the directive.
.TITLE EVAL Evaluates Expressions
|
Transfer directive
.TRANSFER symbol
symbol
A global symbol that is an entry point in a procedure or routine.
.TRANSFER redefines a global symbol for use in a shareable image. The linker redefines the symbol as the value of the location counter at the .TRANSFER directive after a shareable image is linked.To make program maintenance easier, programs should not need to be relinked when the shareable images to which they are linked change. To avoid relinking entire programs when their linked shareable images change, keep the entry points in the changed shareable image at their original addresses. To do this, create an object module that contains a transfer vector for each entry point. Do not change the order of the transfer vectors. Link this object module at the beginning of the shareable image. The addresses of the entry points remain fixed even if the source code for a routine is changed. After each .TRANSFER directive, create a register save mask (for procedures only) and a branch to the first instruction of the routine.
The .TRANSFER directive does not cause any memory to be allocated and does not generate any binary code. It merely generates instructions to the linker to redefine the symbol when a shareable image is being created.
Use .TRANSFER with procedures entered by the CALLS or CALLG instruction. In this case, use .TRANSFER with the .ENTRY and .MASK directives. The branch to the actual routine must be a branch to the entry point plus 2 to bypass the 2-byte register save mask.
Figure 6-1 illustrates the use of transfer vectors.
Figure 6-1 Using Transfer Vectors
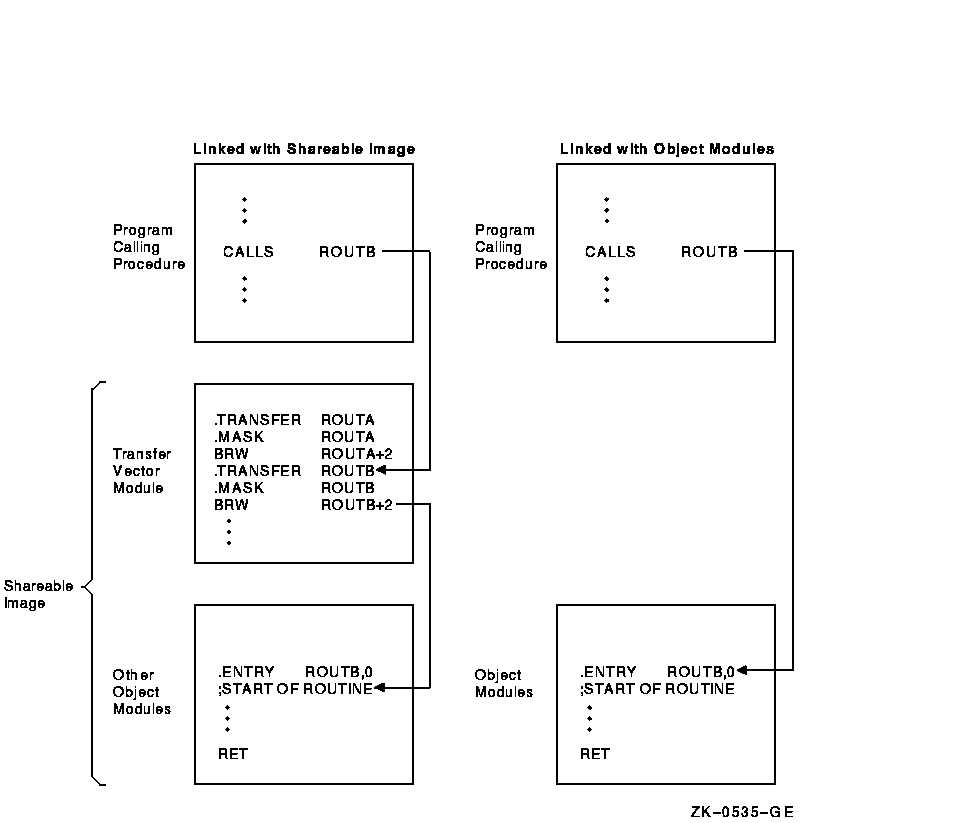
.TRANSFER ROUTINE_A
.MASK ROUTINE_A,^M<R4,R5> ; Copy entry mask
; and add registers
; R4 and R5
BRW ROUTINE_A+2 ; Branch to routine
; (past entry mask)
.
.
.
.ENTRY ROUTINE_A,^M<R2,R3> ; ENTRY point, save
; registers R2 and R3
.
.
.
RET
|
In this example, .MASK copies the entry mask of a routine to the new entry address specified by .TRANSFER. If the routine is placed in a shareable image and then called, registers R2, R3, R4, and R5 will be saved.
Warning directive
.WARN [expression] ;comment
expression
An expression whose value is displayed when .WARN is encountered during assembly.;comment
A comment that is displayed when .WARN is encountered during assembly. The comment must be preceded by a semicolon (;).
.WARN causes the assembler to display a warning message on the terminal or in the batch log file, and in the listing file (if there is one).
.IF DEFINED FULL
.IF DEFINED DOUBLE_PREC
.WARN ; This combination not tested
.ENDC
.ENDC
|
If the symbols FULL and DOUBLE_PREC are both defined, the following warning message is displayed:
%MACRO-W-GENWRN, Generated WARNING: This combination not tested
|
Weak symbol attribute directive
.WEAK symbol-list
symbol-list
A list of legal symbols separated by commas (,).
.WEAK specifies symbols that are either defined externally in another module or defined globally in the current module. .WEAK suppresses any object library search for the symbol.When .WEAK specifies a symbol that is not defined in the current module, the symbol is externally defined. If the linker finds the symbol's definition in another module, it uses that definition. If the linker does not find an external definition, the symbol has a value of zero and the linker does not report an error. The linker does not search a library for the symbol, but if a module brought in from a library for another reason contains the symbol definition, the linker uses it.
When .WEAK specifies a symbol that is defined in the current module, the symbol is considered to be globally defined. However, if this module is inserted in an object library, this symbol is not inserted in the library's symbol table. Consequently, searching the library at link time to resolve this symbol does not cause the module to be included.
.WEAK IOCAR,LAB_3
|
Word storage directive
.WORD expression-list
expression-list
One or more expressions separated by commas (,). You have the option of following each expression by a repetition factor delimited with square brackets ([]).An expression followed by a repetition factor has the format:
expression1[expression2]
expression1
An expression that specifies the value to be stored.[expression2]
An expression that specifies the number of times the value will be repeated. The expression must not contain any undefined symbols and must be an absolute expression (see Section 3.5). The square brackets are required.
.WORD generates successive words (2 bytes) of data in the object module.
.WORD ^X3F,FIVE[3],32
|
The following sections describe terminology and conventions used in
Part II of this volume.
7.1 Numbering
All numbers, unless otherwise indicated, are decimal. Where there is ambiguity, numbers other than decimal are indicated with the base in English following the number in parentheses. For example:
FF (hex) |
Results specified as UNPREDICTABLE may vary from moment to moment,
implementation to implementation, and instruction to instruction within
implementations. Software can never depend on results specified as
UNPREDICTABLE. Operations specified as UNDEFINED may vary from moment
to moment, implementation to implementation, and instruction to
instruction within implementations. The operation might vary from
causing no effect to stopping system operation. UNDEFINED operations
must not cause the processor to hang---to reach an unhalted state from
which there is no transition to a normal state in which the machine
executes instructions. Note the distinction between result and
operation. Nonprivileged software cannot invoke UNDEFINED operations.
When the operation of the VAX scalar processor becomes UNDEFINED, so
does the operation of its associated processor. The converse is not
true; when the operation of the vector processor becomes UNDEFINED, the
operation of the scalar processor need not become UNDEFINED.
7.3 Ranges and Extents
Ranges are specified in English and are inclusive (for example, a range
of integers 0 to 4 includes the integers 0, 1, 2, 3, and 4). Extents
are specified by a pair of numbers separated by a colon and are
inclusive (that is, bits 7:3 specifies an extent of bits including bits
7, 6, 5, 4, and 3).
7.4 MBZ
Fields specified as MBZ (must be zero) must never be filled by software
with a nonzero value. If the processor encounters a nonzero value in a
field specified as MBZ, a reserved operand fault or abort occurs if
that field is accessible to nonprivileged software. MBZ fields that are
accessible only to privileged software (kernel mode) cannot be checked
for nonzero value by some or all VAX implementations. Nonzero values in
MBZ fields accessible only to privileged software may produce UNDEFINED
operation.
7.5 RAZ
Fields specified as RAZ (read as zero) return a zero when read.
7.6 SBZ
Fields specified as SBZ (should be zero) should be filled by software
with a zero value. Non-zero values in SBZ fields produce UNPREDICTABLE
results and may produce extraneous instruction-issue delays.
7.7 Reserved
Unassigned values of fields are reserved for future use. In many cases,
some values are indicated as reserved to CSS and customers. Only these
values should be used for nonstandard applications. The values
indicated as reserved to Compaq and all MBZ (must be zero) fields are
to be used only to extend future standard architecture.
7.8 Figure Drawing Conventions
Figures that depict registers or memory follow the convention that increasing addresses extend from right to left and from top to bottom.
The following sections describe the basic VAX architecture, including the following:
The VAX architecture represents a significant extension of the PDP-11 family architecture. It shares byte addressing with the PDP-11 family, similar I/O and interrupt structures, and identical data formats. Although the instruction set is not strictly compatible with the PDP-11 system, it is related and can be mastered easily by a PDP-11 programmer. Likewise, the similarity allows straightforward manual conversion of existing PDP-11 programs to the VAX system. Existing user-mode PDP-11 programs that do not need the extended features of a VAX system can run unchanged in the PDP-11 compatibility mode provided in the VAX architecture.
As compared to the PDP-11 architecture, VAX architecture offers a greatly extended virtual address space, additional instructions and data types, and new addressing modes. VAX architecture also provides a sophisticated memory management and protection mechanism, and hardware-assisted process sharing and synchronization.
A number of specific goals are achieved in the VAX design. For example:
With the addition of vector processing, VAX architecture can be classified into the following two parts:
Where confusion may be possible, this manual uses the term
scalar to describe objects belonging to the scalar
part of the architecture --- as in scalar instructions and scalar
processor. Similarily, the term vector is used to
describe parts belonging to the vector part of the architecture --- as
in vector registers, and vector instructions. With the exception of
Chapter 10, instructions, exceptions, registers, and other objects
described in the rest of the this manual refer to the scalar part of
the architecture unless otherwise stated.
8.2 VAX Addressing
The basic addressable unit in VAX MACRO is the 8-bit byte. Virtual
addresses are 32 bits long. Therefore, the virtual address space is
232 (approximately 4.3 billion) bytes. Virtual addresses as
seen by the program are translated into physical memory addresses by
the memory management mechanism.
8.3 Data Types
The following sections describe the VAX data types.
8.3.1 Byte
A byte is 8 contiguous bits starting on an addressable byte boundary. The bits are numbered from right to left 0 to 7.
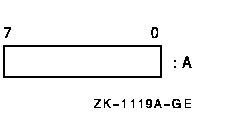
A byte is specified by its address A. When interpreted arithmetically,
a byte is a two's complement integer with bits of increasing
significance ranging from bit 0 to bit 6, with bit 7 the sign bit. The
value of the integer is in the range -128 to +127. For the purposes of
addition, subtraction, and comparison, VAX instructions also provide
direct support for the interpretation of a byte as an unsigned integer
with bits of increasing significance ranging from bit 0 to bit 7. The
value of the unsigned integer is in the range 0 to 255.
8.3.2 Word
A word is 2 contiguous bytes starting on an arbitrary byte boundary. The 16 bits are numbered from right to left 0 to 15.
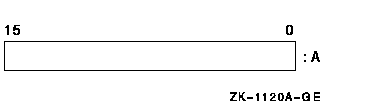
A word is specified by its address, A, which is the address of the byte
containing bit 0. When interpreted arithmetically, a word is a two's
complement integer with bits of increasing significance ranging from
bit 0 to bit 14, with bit 15 the sign bit. The value of the integer is
in the range -32,768 to +32,767. For the purposes of addition,
subtraction, and comparison, VAX instructions also provide direct
support for the interpretation of a word as an unsigned integer with
bits of increasing significance ranging from bit 0 to bit 15. The value
of the unsigned integer is in the range 0 to 65,535.
8.3.3 Longword
A longword is 4 contiguous bytes starting on an arbitrary byte boundary. The 32 bits are numbered from right to left 0 to 31.
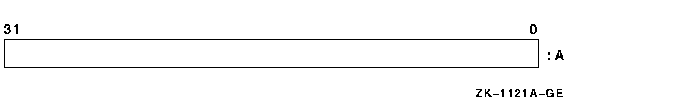
A longword is specified by its address, A, which is the address of the byte containing bit 0. When interpreted arithmetically, a longword is a two's complement integer with bits of increasing significance ranging from bit 0 to bit 30, with bit 31 the sign bit. The value of the integer is in the range -2,147,483,648 to +2,147,483,647. For the purposes of addition, subtraction, and comparison, VAX instructions also provide direct support for the interpretation of a longword as an unsigned integer with bits of increasing significance ranging from bit 0 to bit 31. The value of the unsigned integer is in the range 0 to 4,294,967,295.
| Previous | Next | Contents | Index |
![[Go to the documentation home page]](../../images/buttons/bn_site_home.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs.gif)
![[Help on this site]](../../images/buttons/bn_site_help.gif)
![[How to contact us]](../../images/buttons/bn_comments.gif)
|
| privacy and legal statement | ||
| 4515PRO_012.HTML | ||