TASK DEFAULT IS
ACCESS CONTROL IS (ID=[INVENTORY,*], ACCESS=EXECUTE);
END TASK DEFAULT;
TASK GROUP IS
WORK_GROUP : TASK GROUP FILE IS "SYS$SAMPLE:WORK.TDB";
END TASK GROUP;
TASK ATTRIBUTES ARE
UPDATE_INVENTORY : TASK UPDATE_INVENTORY IN WORK_GROUP;
AUDIT;
DATR : TASK DATR IN WORK_GROUP;
ACCESS CONTROL IS (ID=[INVENTORY,SMITH], ACCESS=EXECUTE);
END TASK ATTRIBUTES;
|
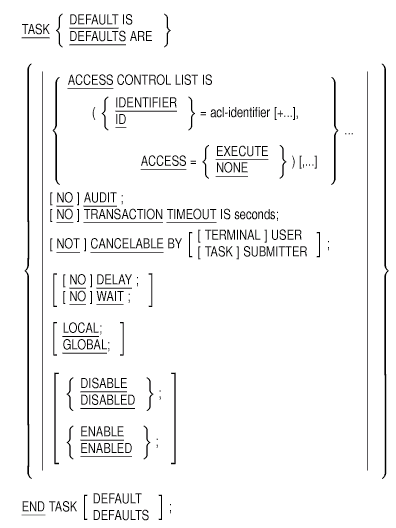
ACCESS Subclause (Task)
Defines who can and who cannot select a task.
Format

Keywords
EXECUTE
Lets users select and run a task.NONE
Prevents users from selecting and running a task.
Parameter
acl-identifier
A legal OpenVMS User Identification Code (UIC) or OpenVMS identifier.You can use the following:
- Alphanumeric UIC identifiers, numeric UICs, general identifiers, and system identifiers, or a combination of any of these.
- Wildcards for both group and member elements of a numeric or alphanumeric UIC. You can also enclose a UIC identifier in square ([ ]) or angle (< >) brackets.
- General and system identifiers set up by your system manager. Do not enclose general and system identifiers in brackets.
Clause Default
The ACMS-supplied default is ACCESS CONTROL IS (ID=[*,*], ACCESS=EXECUTE), which means any user who can log in to ACMS can run tasks. This subclause is optional.
Notes
The ACCESS subclause creates an ordered list of one or more identifier entries. Each identifier entry is called an access control list entry (ACE), and the list of all entries is called an access control list (ACL). You can specify multiple ACEs in a single ACCESS subclause, and you can specify multiple ACCESS subclauses.ACMS uses ACEs and ACLs the way the OpenVMS operating system uses them. See OpenVMS DCL Dictionary for further information on identifiers, ACEs, and ACLs.
ACMS searches an ACL from the first to the last ACE and stops searching at the first match between an identifier on the list and an identifier on a process's rights list. A process's rights list includes a UIC, system-defined identifiers, and any general identifiers assigned to that user by the system manager.
You can use the DCL command SET RIGHTS_LIST to dynamically modify a process or system rights list. This means that you can dynamically allow and deny access to tasks, without making users log out and log back in. See OpenVMS DCL Dictionary for further information on the SET RIGHTS_LIST command.
User rights lists are maintained in the rights database using the Authorize Utility. See OpenVMS System Manager's Manual for further information on the rights database and the Authorize Utility. The rights database is an optional feature of the OpenVMS operating system designed to increase the scope and flexibility of operating system object security.
Multiple ACCESS clauses in a TASK ATTRIBUTES task entry or in a TASK DEFAULTS clause are matched in the order that they appear. If ACMS does not find a match before it reaches the end of an access control list, it denies access to the task.
If one task chains to another, ACMS does not check the access control list for the second task before starting the second task.
Examples
| #1 |
|---|
ACCESS CONTROL IS (ID=[PERSONNEL,JONES], ACCESS=EXECUTE);
|
A user with UIC [PERSONNEL,JONES] can access this task or set of tasks.
| #2 |
|---|
ACCESS CONTROL IS (ID=[PERSONNEL,*], ACCESS=EXECUTE);
|
Any users in group PERSONNEL have access to this task or set of tasks.
| #3 |
|---|
ACCESS ID [300,*] ACCESS NONE;
|
No users in group 300 can access this task or group of tasks.
| #4 |
|---|
ACCESS CONTROL IS (ID=ACCOUNTING, ACCESS=EXECUTE);
|
Users who have the general identifier ACCOUNTING on their rights lists can access this task or group of tasks.
| #5 |
|---|
ACCESS CONTROL IS (ID=[300,*]+ACCOUNTING, ACCESS=EXECUTE);
|
Users who have the general identifier ACCOUNTING on their rights lists and who belong to group 300 can access this task or group of tasks.
| #6 |
|---|
ACCESS CONTROL IS ( (ID=[350,11], ACCESS=NONE),
(ID=ACCOUNTING, ACCESS=EXECUTE),
(ID=[PERSONNEL,JONES], ACCESS=EXECUTE),
(ID=[PERSONNEL,*], ACCESS=NONE) );
|
This example specifies that:
- Any user with a UIC of [350,11] cannot access the task.
- All users who hold the ACCOUNTING general identifier can access the task.
- Any user with a UIC of [PERSONNEL,JONES] can access the task, but all other users in the PERSONNEL group cannot access the task.
APPLICATION DEFAULT DIRECTORY Clause (Application)
Assigns a default device and directory for the process in which an application execution controller runs.
Format

Keyword
USERNAME DEFAULT DIRECTORY
Assigns to an application execution controller the default directory of the user name under which the application runs. ACMS derives the default directory for the execution controller from the SYSUAF entry of the application user name.
Parameter
default-directory
The disk and directory you want ACMS to use as the default for the execution controller. Include an OpenVMS file specification or assign a logical name. If you use a file specification or a logical name longer than 31 characters, enclose it in quotation marks (" ").
Clause Default
The clause APPLICATION DEFAULT DIRECTORY IS USERNAME DEFAULT DIRECTORY is the default. When the default is in effect, ACMS assigns to the application execution controller the default directory it finds in the SYSUAF entry for the application user name. This clause is optional.
Notes
If you are using a logical name, ACMS checks and translates the logical name only when the application is run, not when you are creating the definition or building the application.Use the DCL DEFINE or DCL ASSIGN command, or the APPLICATION LOGICALS clause to create any logical names that you assign with the APPLICATION DEFAULT DIRECTORY clause. If you use DEFINE or ASSIGN, the logical names must be either system logicals or group logicals in the same group as the application execution controller. You can also use the APPLICATION LOGICALS clause, in which case they are process logicals.
The APPLICATION DEFAULT DIRECTORY clause applies to the default directory of the application execution controller. The application execution controller uses this default directory if device and directory are not named for these files: task group database files (.TDB) named in the application definition, request libraries (.RLB), DECforms form files (.FORM and.EXE), and message files (.EXE) named in the task group definitions for that application.
Examples
| #1 |
|---|
DEFAULT DIRECTORY IS SYS$SAMPLE;
USERNAME IS PERSONNEL;
TASK GROUP IS
PERSONNEL_GROUP : TASK GROUP IS "SYS$SAMPLE:PERSONNEL.TDB";
END TASK GROUP;
END DEFINITION;
|
This application definition uses the logical name SYS$SAMPLE for the default device and directory that ACMS uses for the application execution controller process. When you use a logical name such as SYS$SAMPLE, be sure to use the DCL ASSIGN or DCL DEFINE command to define the logical name. Also, make sure you set up a system or group logical name.
| #2 |
|---|
DEFAULT DIRECTORY IS "DBA2:[ACMS.EMPLOYEE]";
USERNAME IS EMPLOYEE;
TASK GROUP IS
EMPLOYEE_GROUP : TASK GROUP IS "SYS$SAMPLE:EMPLOYEE.TDB";
END TASK GROUP;
END DEFINITION;
|
In this example, the DEFAULT DIRECTORY clause assigns the physical device DBA2 and the directory ACMS.EMPLOYEE to the application execution controller process.
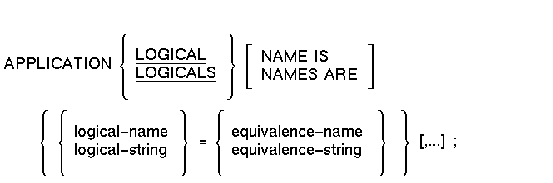
APPLICATION LOGICALS Clause (Application)
Defines one or more process logical names for the process in which an application execution controller runs.
Format
Parameters
logical-name
A 1- to 255-character logical name. If the logical name contains nonalphabetic characters or more than 31 characters, enclose the string in quotation marks (" "). You can substitute a logical name for all or part of a file specification.equivalence-name
The 1- to 255-character equivalence name for the logical name in the logical name table.If the name contains nonalphabetic characters or more than 31 characters, enclose it in quotation marks (" ").
logical-string
A 1- to 255-character logical string.equivalence-string
The 1- to 255-character equivalence string for the logical name in the logical name table.
Clause Default
ACMS defines SYS$DISK, SYS$LOGIN, SYS$SCRATCH from the default directory. This clause is optional.
Notes
Setting up logical names for an application execution controller keeps the device and directory assignments for an application execution controller independent of physical file specifications.ACMS sets up process logical names when the application execution controller is started.
You can include more than one APPLICATION LOGICALS clause in an application definition. You can also include more than one logical name assignment in a single APPLICATION LOGICALS clause.
If a logical name is defined as a system logical, or as a group logical for the user name under which the application execution controller runs, you do not need to define the name in an APPLICATION LOGICALS clause.
The logical names you assign with the APPLICATION LOGICALS clause are available only to the application execution controller, not to any server processes.
ACMS uses the APPLICATION LOGICALS clause to find task group database files (.TDB) named in the application definition, request libraries (.RLB), DECforms form files (.FORM and.EXE), and message files (.EXE) named in the task group definitions for that application.
The APPLICATION LOGICALS clause does not support logical search lists.
Example
APPLICATION LOGICAL NAMES ARE
EMPLOYEE = "ACMS$SAMPLE:EMPLOYEE.ADF"
ACMS$EXC_WSC_POOLSIZE = 50
ACMS$EXC_WS_POOLSIZE = 500
ACMS$EXC_TWSC_POOLSIZE = "ACMS$EXC_<appl_name>_TWSC_SIZE"
ACMS$EXC_TSC_POOLSIZE = "ACMS$EXC_<appl_name>_TWS_SIZE";
APPLICATION LOGICAL NAME IS EMPLOYEE = "ACMS$SAMPLE:EMPLOYEE.ADF";
APPLICATION USERNAME IS DIAL;
TASK GROUPS ARE
TERMINAL_GROUP : TASK GROUP IS "SYS$ACMS:TERM.TDB";
DATAENTRY_GROUP : TASK GROUP IS "SYS$ACMS:DATA.TDB";
END TASK GROUPS;
END DEFINITION;
|
This example redefines ACMS$SAMPLE:EMPLOYEE.ADF so you can use the logical name EMPLOYEE in its place, and defines workspace pool size logical names. In this example, <appl_name> is the name of the application. See Compaq ACMS for OpenVMS Managing Applications for information about defining the logical names for sizing workspace pools.
APPLICATION NAME TABLES Clause (Application)
Specifies one or more logical name tables the application execution controller can use.
Format
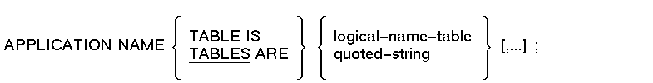
Parameters
logical-name-table
An identifier that is a valid OpenVMS logical name table.quoted-string
A character sequence that begins and ends with a double quote (") and contains a string of 1 to 255 characters.
Clause Default
If the APPLICATION NAME TABLES clause is not specified, the default is the definition of LNM$FILE_DEV in the system logical name directory table. This clause is optional.
Notes
ACMS uses the APPLICATION NAME TABLES clause to define the process logical name LNM$FILE_DEV, the logical name which translates to a search list of logical name tables used whenever file specifications or device names are translated by RMS or the I/O services. This name must translate to a search list of one or more logical name tables. You must specify the order in which they are to be searched when files specifications are translated. The application execution controller defines LNM$FILE_DEV in its process logical name directory table.The application execution controller searches these tables at run time for logicals in the order specified, and returns the first match found, if any.
The order in which you specify the logical name tables is used to define a search list. If you specify this clause, you must also specify the LNM$PROCESS, LNM$JOB, and LNM$SYSTEM logical name tables that the application execution controller can use. Logical names within these tables can be dynamically changed.
See Compaq ACMS for OpenVMS Managing Applications for further information about translating and retranslating logical name tables on a distributed ACMS system, and OpenVMS documentation for more information on logical names and logical name tables.
Example
REPLACE APPL UPDATE_APPL
USERNAME IS JONES;
APPLICATION NAME TABLES ARE
LNM$PROCESS,
LNM$GROUP,
APPL$LOG_TABLE,
LNM$SYSTEM;
|
The APPLICATION NAME TABLES clause in this example specifies that the application execution controller for the application UPDATE_APPL can use the logical name tables LNM$PROCESS, LNM$GROUP, APPL$LOG_TABLE, and LNM$SYSTEM.
APPLICATION USERNAME Clause (Application)
Assigns an OpenVMS user name under which the application execution controller runs.
Format
APPLICATION USERNAME IS user-name ;
Parameter
user-name
A valid OpenVMS user name that ACMS assigns to the process in which the application execution controller runs. The user name can have up to 12 alphanumeric characters, including underscores (_).
Clause Default
This clause is required.
Notes
The user whose user name you include with USERNAME must also be an authorized OpenVMS user.Special privileges or quotas are required for an application execution controller. Assign them to the user name under which the application is running. See Compaq ACMS for OpenVMS Managing Applications for information on these privileges and quotas.
If the ACMS/INSTALL command is used to move an application database file to ACMS$DIRECTORY, the application user name in that application database must match the one defined in the application authorization file, ACMSAAF.DAT. For information on the Application Authorization Utility, see Compaq ACMS for OpenVMS Managing Applications.
Examples
| #1 |
|---|
APPLICATION USERNAME IS ACMS_MANAGER;
TASK GROUPS ARE
ADD_GROUP : TASK GROUP IS "SYS$ACMS:ADD.TDB";
DELETE_GROUP : TASK GROUP IS "SYS$ACMS:DELETE.TDB";
END TASK GROUPS;
END DEFINITION;
|
This application definition assigns the OpenVMS user name ACMS_MANAGER to the process in which the application execution controller runs. The user name contains 12 characters, including an underscore. Include the APPLICATION USERNAME clause in each application definition.
| #2 |
|---|
USERNAME RESOURCES_21;
TASK GROUPS ARE
TERMINAL_GROUP : TASK GROUP IS "SYS$ACMS:TERM.TDB";
DATAENTRY_GROUP : TASK GROUP IS "SYS$ACMS:DATA.TDB";
END TASK GROUPS;
END DEFINITION;
|
An application user name you assign to the application execution controller can contain numbers, letters, and underscore characters. This example assigns the OpenVMS user name RESOURCES_21 to the process under which the applications execution controller runs. The clause omits the optional keywords APPLICATION IS.
AUDIT Clause (Application, Server, Task)
Writes application, server, and task events to the ACMS Audit Trail Log.
Format
[NO ] AUDIT ;
Clause Default
The NO AUDIT clause is the default. This clause is optional.
Notes
You can audit application, server, and task events in any combination. You can audit task events without auditing either application or server events. Similarly, you can audit server or application events without auditing task events.Because auditing can take up large amounts of disk space, you may want to restrict use of the Audit Trail Log by auditing individual servers or tasks.
For more information about the Audit Trail, read Compaq ACMS for OpenVMS Managing Applications.
Application Clause Example
| #1 |
|---|
AUDIT;
APPLICATION USERNAME IS PERSONNEL;
TASK GROUPS ARE
PERSONNEL_GROUP : TASK GROUP FILE IS "SYS$SAMPLE:PERSONNEL.TDB";
DEPARTMENT_GROUP : TASK GROUP FILE IS "SYS$SAMPLE:DEPART.TDB";
END TASK GROUPS;
END DEFINITION;
|
By default, ACMS does not audit the events of an application. You must include the AUDIT clause in the application definition for the Audit Trail to audit information about application events.
In this example, ACMS audits application events but does not audit task or server events unless auditing is explicitly specified at the task and server levels, as in the following examples.
Server Subclause Examples
| #1 |
|---|
USERNAME IS DEPARTMENT;
SERVER DEFAULT IS
AUDIT;
END SERVER DEFAULT;
TASK GROUP IS
DEPARTMENT_GROUP : TASK GROUP IS "SYS$SAMPLE:DEPART.TDB";
END TASK GROUP;
END DEFINITION;
|
By default, ACMS does not audit the activities of servers. To audit all servers defined in a task group, include the AUDIT subclause in a SERVER DEFAULTS clause as in this example. Use of the AUDIT subclause in a SERVER DEFAULTS clause changes the ACMS default from NO AUDIT to AUDIT. When you use the SERVER DEFAULTS clause, put the clause before the TASK GROUPS clause with which you want the new defaults associated.
| #2 |
|---|
USERNAME IS DEPARTMENT;
SERVER DEFAULT IS
AUDIT;
END SERVER DEFAULT;
TASK GROUP IS
DEPARTMENT_GROUP : TASK GROUP IS "SYS$SAMPLE:DEPART.TDB";
END TASK GROUP;
SERVER ATTRIBUTE IS
DEPART_SERVER : SERVER DEPART_SERVER IN DEPARTMENT_GROUP;
NO AUDIT;
END SERVER ATTRIBUTE;
END DEFINITION;
|
You can use the AUDIT and NO AUDIT clauses in the SERVER DEFAULTS clause to change defaults for all servers defined in a task group. You can also define AUDIT and NO AUDIT with the SERVER ATTRIBUTES clause to change defaults on a server-by-server basis. This example first uses the SERVER DEFAULTS clause to change the ACMS default from NO AUDIT to AUDIT for all of the servers in the DEPARTMENT_GROUP task group. Second, because you do not want to audit one of the servers, namely DEPART_SERVER, in the DEPARTMENT_GROUP task group, define the NO AUDIT subclause for that server in the SERVER ATTRIBUTES clause.
Task Subclause Example
| #1 |
|---|
APPLICATION USERNAME IS PERSONNEL;
TASK DEFAULT IS
AUDIT;
END TASK DEFAULT;
TASK GROUPS ARE
PERSONNEL_GROUP : TASK GROUP FILE IS "SYS$SAMPLE:PERSONNEL.TDB";
DEPARTMENT_GROUP : TASK GROUP FILE IS "SYS$SAMPLE:DEPART.TDB";
END TASK GROUPS;
END DEFINITION;
|
By default, ACMS does not audit the events of tasks. In this example, you change the default from NO AUDIT to AUDIT for all tasks in both the task groups, PERSONNEL_GROUP and DEPARTMENT_GROUP.
| Previous | Next | Contents | Index |