| Previous | Contents | Index |
By default, when the ENCRYPT software encrypts an input file and writes the resulting output file, the input file is retained. However, do not encrypt a file and then leave the plaintext file online if you are concerned about the security of the file.
You can use the DCL DELETE command with the /ERASE qualifier to remove the contents of the plaintext file from the disk, or you can use the following qualifiers with the ENCRYPT command:
The /DELETE qualifier deletes the input file after the encryption operation completes and the output file is written and closed. If you have multiple versions of the input file, they are not all deleted. /DELETE acts on only the version of the input file that you encrypted.
To delete the unencrypted input file from the disk, use the /DELETE qualifier. The following command specifies that the SAVEDMAIL.MAI file be encrypted using the TWENTYFIVECENTS encryption key. Because the /DELETE qualifier is specified, the input file is deleted after the encrypted output file is written.
$ ENCRYPT /DELETE SAVEDMAIL.MAI TWENTYFIVECENTS |
When you delete or purge a file, the file's header record is destroyed so that the file can no longer be accessed by normal means. The information in the file, however, stays on the disk until it is overwritten. Disk scavenging is a technique used to obtain such file data from a disk. To thwart disk scavenging, use the /ERASE qualifier with the /DELETE qualifier. When you specify /ERASE, the OpenVMS operating system overwrites the location in which the input file was stored with the data security pattern. The data no longer exists.
The following command specifies that after SAVEDMAIL.MAI is encrypted, the input file is erased with the data security pattern before being deleted.
$ ENCRYPT /DELETE /ERASE SAVEDMAIL.MAI TWENTYFIVECENTS |
Files are encrypted using a randomly generated data key. One benefit of this procedure is that two files identical in plaintext form and encrypted with the same command are not identical in their encrypted form.
The Encryption for OpenVMS implementation of DES uses the following modes of the DES algorithm:
These modes perform the encryption operation differently, as follows:
For details about the advantages of each mode, see one of the numerous
texts available on this subject.
3.2.7 Encryption Algorithm Qualifiers
You can choose an encryption algorithm for encrypting either the data key or the file data. Figure 3-1 shows the relationship of encryption keys and algorithms. The figure shows that:
Figure 3-1 Relationship of Keys and Algorithms
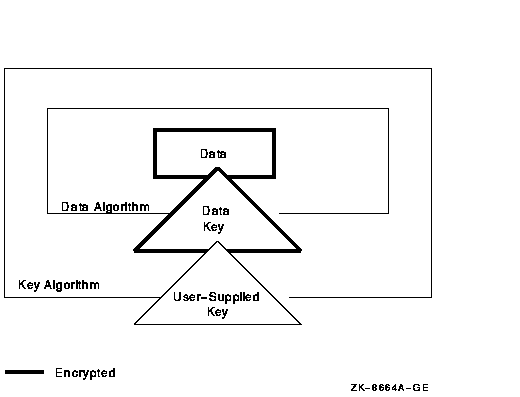
The qualifier you use affects the correct decryption procedure:
To specify an algorithm other than DESCBC to encrypt the key and initialization vector, use the /KEY_ALGORITHM qualifier. This qualifier has the format:
/KEY_ALGORITHM={DESCBC (default) | DESECB | DESCFB}
For example, the following command uses the DESCFB algorithm with the TWENTYFIVECENTS key to protect the data key and the initialization vector.
$ ENCRYPT /KEY_ALGORITHM=DESCFB SAVEDMAIL.MAI TWENTYFIVECENTS |
To specify an algorithm for encrypting files other than the default, use the /DATA_ALGORITHM qualifier. This qualifier has the format:
/DATA_ALGORITHM={DESCBC (default) | DESECB | DESCFB}
For example, the following command encrypts the SAVEDMAIL.MAI file using the Cipher Feedback mode of the DES algorithm (DESCFB).
$ ENCRYPT /DATA_ALGORITHM=DESCFB SAVEDMAIL.MAI TWENTYFIVECENTS |
If you use the default value of DESCBC for the /DATA_ALGORITHM
qualifier when encrypting a file, this qualifier is optional for
decrypting the file.
3.2.8 File Compression
To reduce the size of the plaintext file before encrypting it, use the /COMPRESS qualifier. Data compression can save media space when physically transporting encrypted files and can save time when electronically transporting encrypted files across a network.
Compression efficiency depends on the structure of the data in your file. Evaluate a performance tradeoff when deciding whether or not to use this qualifier. Decryption is generally faster on a compressed file, but encryption takes longer. You might choose to use the /COMPRESS qualifier when the following conditions apply:
The following command compresses the SAVEDMAIL.MAI file before encrypting it.
$ ENCRYPT /COMPRESS SAVEDMAIL.MAI TWENTYFIVECENTS |
If you use the /COMPRESS qualifier when encrypting a file, you need not specify this qualifier when decrypting the file. If necessary, the file is automatically decompressed when it is decrypted. |
To identify the version of Encryption software running on your system, use the /VERSION qualifier. For example:
$ ENCRYPT /VERSION Copyright (c) Compaq 2001, Digital Equipment Corporation. 1978, 1997. All rights reserved. Compaq Encryption V1.6) |
Authentication is the checking of files to determine whether or not they have been modified.
The ENCRYPT /AUTHENTICATE command detects any modification of either plaintext or ciphertext files. The software calculates a Message Authentication Code (MAC) based on the contents of the files and associates it with one or more files. An additional MAC is created that is based on security settings unless you specifically request that the security MAC not be created. At a later time, when you want to check file integrity, the software recalculates the MACs and then compares the current and stored MACs. Before you use the ENCRYPT /AUTHENTICATE command, complete the process that associates MACs with files (see Section 3.3.1).
The ENCRYPT /AUTHENTICATE command has the following syntax:
ENCRYPT /AUTHENTICATE file-spec key-name [ qualifiers ]
where
| file-spec | is the name of the file you want to check. |
| key-name |
is the name of the key.
Specify a 1-to-243-character string. |
| qualifiers | are options that control the encryption process or the selection of files you want to encrypt |
A summary report on the authentication operation is displayed on SYS$OUTPUT.
The following qualifiers are valid with ENCRYPT /AUTHENTICATE:
In addition, you can use all the file selection qualifiers available to the ENCRYPT command: /BACKUP, /BEFORE, /BY_OWNER, /CONFIRM, /EXCLUDE, /EXPIRED, /MODIFIED, and /SINCE (see Section 3.2.4).
The following sections describe how to use the /DATABASE, /LOG,
/SECURITY, /OUTPUT, and /UPDATE qualifiers with ENCRYPT /AUTHENTICATE.
3.3.1 Associating MACs with Files
To associate MACs with a file or to replace former MAC values with new MAC values, use the /UPDATE qualifier. The /UPDATE qualifer updates two different MACs created from file contents and from security settings. The following command creates MAC values for all files in the current directory.
$ ENCRYPT /AUTHENTICATE *.* whitehen /UPDATE %ENCRYPT-I-SUMMARY1, Summary: Files successfully authenticated: 0 %ENCRYPT-I-SUMMARY2, Files failing authentication: 0 %ENCRYPT-I-SUMMARY3, Files not in database: 3 %ENCRYPT-I-SECSUMM1, Summary: Security settings authenticated: 0 %ENCRYPT-I-SECSUMM2, Security settings failing authentication: 0 %ENCRYPT-I-SECSUMM3, Security settings not in database: 3 |
Two sets of summary information are displayed: the first set applies to the MAC values generated from the file contents, the second set applies to the MAC values generated from the security settings. Because this is the first time MACs are associated with these files, none are reported as authenticated (summary message 1 for each set) or as having failed authentication (summary message 2 for each set). The last message in each set reports that no previous MACs were associated with these files.
The MACs are stored in a binary database. Therefore, you cannot specify
/NODATABASE or /NOSECURITY with /UPDATE. For more information, see
Section 3.3.3.
3.3.2 Checking Files
With no other qualifiers, the ENCRYPT /AUTHENTICATE command compares previous MACs with current MACs. In addition, the software reports on files with no currently associated MACs.
The following command reports on the status of all the files in the current directory.
$ ENCRYPT /AUTHENTICATE *.* whitehen %ENCRYPT-I-NOUPDATE, database will not be updated with new authentication codes %ENCRYPT-I-SUMMARY1, Summary: Files successfully authenticated: 3 %ENCRYPT-I-SUMMARY2, Files failing authentication: 0 %ENCRYPT-I-SUMMARY3, Files not in database: 0 %ENCYRPT-I-SECSUMM1, Summary: Security settings authenticated: 3 %ENCYRPT-I-SECSUMM2, Security settings failing authenticated: 0 %ENCYRPT-I-SECSUMM3, Security settings not in database:0 |
A database file stores MAC values in binary format. By default, binary MAC values created from the file contents are stored in SYS$LOGIN:ENCRYPT$MAC.DAT. You can use the /DATABASE qualifier to store the MAC values in an alternate file.
The following command selects an alternate file in which to store the MAC values.
$ ENCRYPT /AUTHENTICATE *.com whitehen /DATABASE=[MACS]MACCHECK.DAT /UPDATE %ENCRYPT-I-NEWDB, New authentication code database has been created %ENCRYPT-I-SUMMARY1, Summary: Files successfully authenticated: 0 %ENCRYPT-I-SUMMARY2, Files failing authentication: 0 %ENCRYPT-I-SUMMARY3, Files not in database: 6 |
When you specify /NODATABASE, the MAC values are not stored. The next
time you use the ENCRYPT /AUTHENTICATE command, the files are treated
as new since there are no current MAC values to check.
3.3.4 Specifying a Security MAC File
MAC entries based on security settings are automatically generated and stored in a security database when the /UPDATE qualifier is used (see Section 3.3.1). If you do not want to generate a MAC value based on security settings, use the /NOSECURITY qualifier on the ENCRYPT /AUTHENTICATE command line.
The entries in the security database are generated by using the security settings: owner, protection settings, and an ACL if one is associated with the file. By default, security MAC values are stored in the database ENCRYPT$SEC.DAT. You can use the /SECURITY qualifier to store security MAC values in an alternate file.
The following command selects an alternate file in which to store security MAC values.
$ ENCRYPT /AUTHENTICATE *.com seveneleven /SECURITY=SECURITYMAC.DAT /UPDATE %ENCYRPT-I-NEWSECDB, New authentication security settings database has been created %ENCRYPT-I-SUMMARY1, Summary: Files successfully authenticated: 0 %ENCRYPT-I-SUMMARY2, Files failing authentication: 0 %ENCRYPT-I-SUMMARY3, Files not in database: 3 %ENCRYPT-I-SECSUMM1, Summary: Security settings authenticated: 0 %ENCRYPT-I-SECSUMM2, Security settings failing authentication: 0 %ENCRYPT-I-SECSUMM3, Security settings not in database: 3 |
In addition to a binary MAC database, Encryption stores MAC values and status information in readable form. By default, readable MAC values are stored in SYS$LOGIN:ENCRYPT$MAC.LIS.
To store readable values in an alternate file, use the /OUTPUT qualifier. The file extension defaults to .LIS. For example, this command specifies SYS$LOGIN:08MAC.LIS as the listing file:
$ ENCRYPT /AUTHENTICATE *.* whitehen /OUTPUT=08MAC %ENCRYPT-I-NOUPDATE, database will not be updated with new authentication codes %ENCRYPT-I-SUMMARY1, Summary: Files successfully authenticated: 6 %ENCRYPT-I-SUMMARY2, Files failing authentication: 0 %ENCRYPT-I-SUMMARY3, Files not in database: 0 |
To display the listing on SYS$OUTPUT, enter:
$ TYPE 08MAC.LIS
File Integrity Report 22-APR-2001 10:50:22.62 Compaq Encryption V1.6 Page 1
Authentication database: DISK_1:[000000.SCRATCH]ENCRYPT$MAC.DAT;1
File name Stored MAC Current MAC Status
================================== ================= =========== ======
DISK_1[SCRATCH]EXAMPLE.FILE;1 90E70CB4E8E96BBF (same)
owner: [1,1] prot: (RWED, RWED, RWED, )
DISK_1[SCRATCH]PICTURE.SLS;1 FCAD115A72E7934A (same)
owner: [1,1] prot: (RWED, RWED, RWED, )
DISK_1[SCRATCH]RELEASE.TXT;1 11375BD8D504ABB3 (same)
owner: [1,1] prot: (RWED, RWED, RWED, )
DISK_1[SCRATCH]RELEASE_NOTES.PS;3 2632027C133A8B5F (same)
owner: [1,1] prot: (RWED, RWED, RWED, )
DISK_1[SCRATCH]SCHEDULE.LIST;3 852D440358FBFF95 (same)
owner: [1,1] prot: (RWED, RWED, RWED, )
DISK_1[SCRATCH]WATCH_MAIL.COM;5 B75D00EC4991662C (same)
owner: [1,1] prot: (RWED, RWED, RWED, )
Summary: Files successfully authenticated: 6
Files failing authentication: 0
Files not in database: 0
Summary: Security settings authenticated: 6
Security settings failing authentication: 0
Security settings not in database: 0
|
To suppress the creation of this listing, use the /NOOUTPUT qualifier.
3.3.6 Logging the Authentication Operation
To display the results of the authentication operation on each file, use the /LOG qualifier. For example, the following command displays the results of each file authentication on your terminal screen.
$ ENCRYPT /AUTHENTICATE /LOG *.* whitehen %ENCRYPT-I-NOUPDATE, database will not be updated with new authentication codes %ENCRYPT-S-AUTHMATCH, File DISK_1:[SCRATCH]EXAMPLE.TXT;1 successfully authenticated %ENCRYPT-S-SECAUTHMATCH, Security settings for DISK_1:[SCRATCH]EXAMPLE.TXT successfully authenticated %ENCRYPT-S-AUTHMATCH, File DISK_1:[SCRATCH]TEST.TXT;1 successfully authenticated. %ENCRYPT-S-SECAUTHMATCH, Security settings for DISK_1:[SCRATCH]TEST.TXT successfully authenticated %ENCRYPT-S-AUTHMATCH, File DISK_1:[SCRATCH]RELEASE.TXT;2 successfully authenticated. %ENCRYPT-S-SECAUTHMATCH, Security settings for DISK_1:[SCRATCH]RELEASE.TXT successfully authenticated %ENCRYPT-I-SUMMARY1, Summary: Files successfully authenticated: 6 %ENCRYPT-I-SUMMARY2, Files failing authentication:0 %ENCRYPT-I-SUMMARY3, Files not in database:0 %ENCRYPT-I-SECSUMM1, Summary: Security settings authenticated: 6 %ENCRYPT-I-SECSUMM2, Security settings failing authentication:0 %ENCRYPT-I-SECSUMM3, Security settings not in database:0 |
When a key outlives its usefulness, delete it from a key storage table. Enter the ENCRYPT /REMOVE_KEY command and specify the name under which the encrypted key value was stored in the key table. The key name is the character string previously defined with an ENCRYPT /CREATE_KEY command.
The ENCRYPT /REMOVE_KEY command has the following format:
ENCRYPT /REMOVE_KEY key-name [ qualifiers ]
By default, the ENCRYPT /REMOVE_KEY command deletes the key definition from the process key storage table. Logging out a process also removes a key definition from the process key storage table.
To remove a key definition from the job, group, or system storage table, specify the /JOB, /GROUP, or /SYSTEM qualifier with the ENCRYPT /REMOVE_KEY command. Just as you need privileges to create group or system keys, you need privileges to delete them.
For example, the following command deletes the HAMLET key from the system key storage table:
$ ENCRYPT /REMOVE_KEY HAMLET /SYSTEM |
To verify key removal, use the /LOG qualifier with the ENCRYPT /REMOVE_KEY command. The following command reports that the key HAMLET is removed:
$ ENCRYPT /REMOVE_KEY HAMLET /SYSTEM /LOG %ENCRYPT-S-KEYDEL, key deleted for key name = HAMLET |
To gain access to the data in an encrypted file, decrypt the file using the DECRYPT command. Follow these steps:
The DECRYPT command has the following format:
DECRYPT file-spec key-name [ qualifiers ]
where
| file-spec | is the name of the file. |
| key-name | is the name of the key. |
| qualifiers | are options that control the decryption process or the selection of files you want to decrypt |
For the ciphertext file, which is the file to be decrypted, specify a file that resides on disk and that is not a directory file.
To specify multiple input files to the DECRYPT command, use wildcard
characters in the file specification. To control file selection,
specify the appropriate DECRYPT command qualifiers (see Section 3.5.4).
Do not use wildcard characters to specify directory files or files
containing bad blocks.
3.5.2 Output File Specification
The result of the decryption operation is a plaintext file. One plaintext file is created for each input file that is decrypted. By default, the DECRYPT command writes each plaintext file to a separate output file with a file specification that defaults to the input file specification with a version number that is one higher than that of the input file.
You can specify an alternate output file specification with the /OUTPUT qualifier. When specifying the /OUTPUT qualifier, you specify those parts of the file specification that you want to be different from the defaults. You do not need to specify an entire file specification; any fields omitted in the file specification default to the input file specification.
For example, the following DCL command selects for decryption all files in the current directory matching the wildcard file specification of *.ENC. The /OUTPUT qualifier specifies that any output files created have a file type of COM.
$ DECRYPT *.ENC/OUTPUT=.COM FRANCISSCOTT |
| Previous | Next | Contents | Index |