![[Compaq]](../../images/compaq.gif)
![[Go to the documentation home page]](../../images/buttons/bn_site_home.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs.gif)
![[Help on this site]](../../images/buttons/bn_site_help.gif)
![[How to contact us]](../../images/buttons/bn_comments.gif)
![[OpenVMS documentation]](../../images/ovmsdoc_sec_head.gif)
| Document revision date: 19 July 1999 | |
![[Compaq]](../../images/compaq.gif) |
![[Go to the documentation home page]](../../images/buttons/bn_site_home.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs.gif)
![[Help on this site]](../../images/buttons/bn_site_help.gif)
![[How to contact us]](../../images/buttons/bn_comments.gif)
|
![[OpenVMS documentation]](../../images/ovmsdoc_sec_head.gif)
|
|
| Previous | Contents | Index |
TCP/IP protocols provide for the interconnection of networks and the
interconnection of computing systems in a network. This section
describes how TCP/IP protocols evolved to support interconnection of
networks, including the global Internet.
1.2.1 What Is Internetworking?
The technology called internetworking makes possible the interconnection of multiple diverse networks into a coordinated whole. Internetworking adds physical connections and a new set of conventions to permit networks with different underlying hardware technologies to form an internet.
An internet is a collection of packet-switching networks interconnected
by either gateways or routers; an internet supports protocols that
permit the diverse networks to function as a large, virtual network.
The largest internet, the global network formed by research,
commercial, and governmental organizations, is referred to as the
Internet.
1.2.2 Using TCP/IP for Internetworking
TCP/IP was developed as a result of research funded by the Defense Advanced Research Projects Agency (DARPA), an agency of the U.S. Department of Defense. The need to connect many computers with different hardware, operating systems, and networking technologies led to the development of the ARPANET, on which TCP/IP was first implemented. DARPA also made the TCP/IP implementation available to university researchers for use with UNIX operating systems.
The growing diversity of new networking technologies caused DARPA to study network connectivity, or internetworking. By 1983, the Department of Defense mandated that all computers connected to long-haul networks use TCP/IP. The success of the TCP/IP technology and internetworking has resulted in the enormous growth of the global Internet (see Section 1.2.3).
TCP/IP is widely used within organizations or industries to create internets that may or may not be connected to the global Internet. TCP/IP capabilities include the following:
The Internet is a worldwide network encompassing tens of thousands of individual networks linked together with a high-speed backbone network. The backbone network comprises telephone and fiber-optic links, lasers, microwaves, satellites, and other equipment connecting networks and computers throughout the world. The backbone network evolved in part from the high-speed network developed by the National Science Foundation (NSF), a U.S. government agency, to connect their supercomputer sites and make them accessible to scientists, researchers, and engineers.
Examples of the many kinds of organizations linked through the Internet are scientific research agencies, government laboratories, universities and other educational facilities, libraries and archives, commercial corporations, and groups of people with common interests. Some commercial companies act as Internet service providers, making access to the Internet available to organizations and individuals.
A great variety of information is accessible through the Internet, ranging from scientific and academic material to commercial product documentation to news databases and forums for exchanging opinions and ideas.
The Internet provides global connectivity; major Internet facilities are located on every continent and in most countries around the world. In many countries, the Internet is readily accessible to individuals as well as regional and local groups. In addition, gateways permit access to resources on many non-Internet networks. The Internet is expanding at a very rapid rate in terms of numbers of connections and the amount of message traffic.
Internet connectivity enables users to communicate with other connected hosts in distant countries as though the hosts were connected to the same local network. The design of the Internet allows an Internet user to access and retrieve vast amounts of information from anywhere in the world.
Two networking models support open systems interconnection. The first model, TCP/IP, is based on a suite of protocols in which each protocol solves a particular network communications problem. The second model, OSI, is based on international standards.
This chapter compares the models, and then provides an overview of
TCP/IP architectural design, layers and protocols, and the TCP/IP
naming mechanism.
2.1 Introduction to TCP/IP Architecture
Network software design is commonly based on a networking model made up of several layers that work together. Each layer is a group of related functions with its own characteristic protocols and purpose. The layers are built on top of one another so that each layer uses services provided by the layer beneath it. Information flows down through the layers of the sending host and up through the layers of the receiving host.
The architectural model on which networking implementations are based
defines the ways in which operating systems can communicate with each
other. Networking protocols, services, and interfaces allow systems
that implement the model to communicate.
2.1.1 OSI and TCP/IP Models
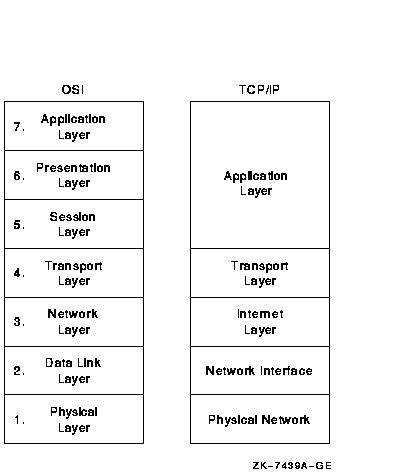
The OSI model is a layered architecture that interconnects systems from different vendors in an open systems network. The OSI model is based on a set of international standards developed by the International Organization for Standardization (ISO). The seven layers of the OSI model are shown in Figure 2-1. The lower layers (1 through 4) provide for reliable transfer of information between two communicating systems. The upper layers (5 through 7) provide services that enable user applications to communicate with each other.
The TCP/IP model can be used in a heterogeneous environment that has equipment from many different vendors. Layers in the TCP/IP model are also shown in Figure 2-1.
Figure 2-1 Comparison of Layers in the OSI and TCP/IP Models
An OpenVMS system can support both TCP/IP and OSI capabilities on the
same system. OSI protocols are incorporated in Digital's DECnet
software (DECnet-Plus for OpenVMS), which can run concurrently with
TCP/IP networking products on the same OpenVMS system.
2.1.2 Comparing the OSI Model with the TCP/IP Model
In comparing the TCP/IP model with the OSI model, TCP/IP can be viewed as supplying the functions of layers 3 and 4 of the OSI model. TCP/IP provides a number of protocols for the internet layer (corresponding to layer 3, the network layer, of the OSI model) and the transport layer (corresponding to layer 4, the transport layer, of the OSI model).
As shown in Figure 2-1, however, the TCP/IP model does not follow the OSI model exactly for all layers. For the upper-level layers, TCP/IP applications provide the services of the presentation and session layers of the OSI model. In addition, TCP/IP does not provide specific protocols for the bottom two layers that correspond to the physical layer and the data link layer of the OSI model. Instead, TCP/IP interfaces with whatever protocols are available for the physical network and the network interface.
Implementation of the OSI model places emphasis on providing a reliable data transfer service, while the TCP/IP model treats reliability as an end-to-end problem. Each layer of the OSI model detects and handles errors; all data transmitted includes checksums. The transport layer of the OSI model checks source-to-destination reliability.
In the TCP/IP model, reliability control is concentrated at the transport layer. The transport layer handles all error detection and recovery. Individual hosts or links can lose data without making any attempt at recovery. Corrupted datagrams can be discarded at internal gateways, and datagrams can be rerouted or dropped if network line problems occur. The TCP/IP transport layer uses checksums, acknowledgments, and timeouts to control transmissions and provides end-to-end verification.
Another contrast between the OSI model and the TCP/IP model is the role of the host system. Hosts on OSI implementations do not handle network operations, but TCP/IP hosts participate in most network protocols. TCP/IP hosts carry out such functions as end-to-end verification, routing, and network control. The TCP/IP internet can be viewed as a data stream delivery system involving intelligent hosts.
The following sections describe TCP/IP networking design, including the
functions of the different layers and protocols.
2.2 TCP/IP Design
Table 2-1 lists the layers into which the TCP/IP model organizes TCP/IP software functions. Figure 2-2 shows the TCP/IP layers and the protocols supported at each layer. Data can pass successively through the layers of the TCP/IP software, and each layer adds information to the message being transmitted to the remote host. If intervening hosts are required to route the data through the network to the other host, only the lower layers (the physical network, the network interface, and possibly the internet layer) are involved.
| TCP/IP Layer | Function |
|---|---|
| Application layer | A user invokes an application program that accesses a service available across a TCP/IP internet. The application passes data to and receives data from the transport layer. Protocols available at the application layer are described in Section 2.3. |
| Transport layer | This layer provides services that permit an application program on one host to communicate with an application program on a remote host. The transport layer divides the stream of data into packets, adds a destination address, and passes the packets to the next layer. The transport uses two protocols, TCP and UDP, described in Section 2.4. |
| Internet layer | This layer ensures that data is routed to the correct destination. The internet layer encapsulates the packet received from the transport layer into a datagram, adds a header, and determines the routing requirement. For incoming datagrams, it determines which transport protocol should handle the packet. The internet layer uses the Internet Protocol (IP), as described in Section 2.5. |
| Network interface layer | This layer controls access to network transmission mechanisms. The network interface is responsible for accepting IP datagrams and transmitting them over a specific network. The interface can be a device driver (connected to a LAN) or a subsystem with its own data link protocol. |
| Physical network | The hardware connection provides the physical interconnection between the host and the network. |
Figure 2-2 TCP/IP Layers and Protocols

The application layer includes all processes and services that use the transport layer to deliver data. The most widely-known applications protocols are:
Application programs send messages (streams of data) to the transport layer protocols UDP and TCP. An application is designed to choose either UDP or TCP based on the services it needs. An application chooses:
When an application sends a message to the transport layer, UDP and TCP break the information into packets, add a packet header (which includes a destination address), and send the information to the network layer for further processing. Other protocols and applications use UDP to make datagram connections and TCP to make stream connections. The socket interface implements these protocols.
UDP and TCP use IP, the underlying protocol, to transport datagrams.
Both allow programs to send messages to and receive messages from
applications on other hosts, and both use protocol
ports (abstract destination points) on the host to identify
the specific destination of the message. These protocol ports receive
and hold messages in queues until applications can retreive them.
2.4.1 Transmission Control Protocol
TCP provides reliable stream delivery of data between Internet hosts. Unlike UDP, TCP ensures that data is not damaged, lost, duplicated, or delivered out of order to a receiving process. Because of this transport reliability, application programmers are not required to build communications safeguards into their software.
TCP supplies the following services in carrying out end-to-end verification between the source and destination for detection and recovery of lost datagrams:
Before the transmission of data, TCP establishes a connection between the two transport layers through the exchange of messages. Because multiple application programs can run on a single host, TCP uses protocol port numbers to distinguish among the multiple destinations within a given host computer. A specific port on a host can be addressed by a client to request a specific service. To identify a connection, TCP specifies a pair of end points, defining each end point as consisting of a host IP address and a TCP port on that host.
The following application protocols use TCP:
TELNET and FTP applications are described in Chapter 3.
2.4.2 User Datagram Protocol
UDP is an alternative transport mechanism that relies on the underlying IP to send its datagrams and provides the same connectionless message delivery as IP. UDP does not guarantee that the data will be delivered. Applications that use UDP must have built-in safeguards to discover that a datagram was delivered out of sequence or not delivered. UDP allows the sender to specify source and destination port numbers for the message and also calculates a checksum of both the data and the header. These two features allow the sending and receiving applications to ensure the correct delivery of a message.
UDP permits an application to send a message to a destination application on another network without requiring that the destination application be active when the message is sent. UDP sends datagrams, but does not guarantee delivery or protection against duplicate datagrams. The message delivery is connectionless: UDP considers the delivery complete once the message is placed on the network.
The following protocols can use UDP:
The Internet network-level protocols (IP, ARP, ICMP) handle machine-to-machine communications. These protocols provide for transmission and reception of transport requests and handle network-level control.
The TCP/IP internet layer moves data from one host to another, even if the hosts are on different networks. The internet layers on cooperating hosts are in communication with each other while they move data across a network. Each intervening host along the logical communications path moves the data closer to the destination host.
The primary protocol used to move data is the Internet Protocol (IP), which provides the following services:
IP provides a connectionless method of delivering data from one host to
another. It does not guarantee delivery and does not provide sequencing
of datagrams (packaged in packets). IP attaches a header to the
datagram that includes the source address and the destination address,
both of which are unique internet addresses. If an intervening router
needs to change the size of a message so a router can handle the
message, IP fragments the message into smaller packets that can be
reassembled at the destination host.
2.5.1 IP Routing
IP routing involves using the destination IP address of a datagram to decide where to send the datagram. IP routing passes to the network interface software the IP address of the next machine to which the datagram should be routed. The datagram is encapsulated, the IP address is mapped to a physical address, and the frame is transmitted to the next host.
If the source and destination hosts are in the same network, the
routing is direct. If the datagram must be sent through a gateway to
another network, the routing is indirect. The host sends an indirectly
routed datagram to the nearest gateway; the datagram is then routed
from gateway to gateway until it can be routed directly across a
network to the destination host.
2.5.2 IP Addressing
Each host in a network has a unique IP address that is used in communicating with the host. Addresses, which are assigned by a central agency, are in 32-bit binary format, usually expressed as 8-bit fields separated by decimal points. Each field can have a value from 0 to 255 (for example, 97.0.5.110). IP addresses are divided into the following classes:
A subnet is a network within a network. Organizations
can use subnet addressing to divide an assigned network. For example,
an organization that uses a Class B network number, might choose to
subnet the network to effectively have more than 250 networks by using
8 bits of subnet. The Class B network number becomes a Class C network
number. Subnets can be used to add hosts without disrupting the rest of
the network, especially if the network contains a number of gateways.
2.5.3 Internet Host Names
Each host computing system in a TCP/IP network or internet is identified by a unique host name as well as a unique IP host address. TCP/IP supplies a mechanism for translating the host name to the host address that is required by the IP protocol.
The domain name system (DNS) is one example of a distributed name/address mechanism used in the global Internet. It provides for a hierarchy of host names and distributes host name and address information throughout the Internet. Another example is the BIND Resolver.
The name space for Internet hosts supports hierarchically arranged host names, called domain names. The domain name uniquely identifies a host computer that is connected to the Internet. The top-level domain name in the hierarchy can represent an organizational domain or a geographical domain. In the United States, examples of typical organizational domain names are com (for commercial organizations) and edu (for educational institutions). Internationally, the geographical domain name is a standard two-letter international country abbreviation (such as au for Australia and fr for France).
The top-level domain name can be divided into subdomain names that further identify the host. The subdomain names are arranged to the left of the top-level domain name and are separated by periods. For example, computer-name.company.com is the format.
The Internet address of a user who is logged in to an Internet host is in the form userid@domain in which userid is the user's login name.
| Previous | Next | Contents | Index |
![[Go to the documentation home page]](../../images/buttons/bn_site_home.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs.gif)
![[Help on this site]](../../images/buttons/bn_site_help.gif)
![[How to contact us]](../../images/buttons/bn_comments.gif)
|
| privacy and legal statement | ||
| 6436PRO_001.HTML | ||