![[OpenVMS documentation]](../../images/openvms_doc_banner_top.gif)
|
![[Site home]](../../images/buttons/bn_site_home_off.gif)
![[Send comments]](../../images/buttons/bn_comments_off.gif)
![[Help with this site]](../../images/buttons/bn_site_help_off.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs_off.gif)
![[OpenVMS site]](../../images/buttons/bn_openvms_off.gif)
![[Compaq site]](../../images/buttons/bn_compaq_off.gif)
|
| Updated: 11 December 1998 |
![[OpenVMS documentation]](../../images/openvms_doc_banner_top.gif)
|
![[Site home]](../../images/buttons/bn_site_home_off.gif)
![[Send comments]](../../images/buttons/bn_comments_off.gif)
![[Help with this site]](../../images/buttons/bn_site_help_off.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs_off.gif)
![[OpenVMS site]](../../images/buttons/bn_openvms_off.gif)
![[Compaq site]](../../images/buttons/bn_compaq_off.gif)
|
| Updated: 11 December 1998 |
OpenVMS System Management Utilities Reference
Manual
| Previous | Contents | Index |
Indicates the utility must operate on records dated with the specified time or after the specified time.
/SINCE [=time]
/NOSINCE
time
Specifies the time used to select records. Records dated the same or later than the specified time are selected. You can specify an absolute time, a delta time, or a combination of the two. Observe the syntax rules for date and time described in the OpenVMS User's Manual.If you specify /SINCE without the time, the utility uses the beginning of the current day.
| #1 |
|---|
$ ANALYZE/AUDIT /SINCE=25-NOV-1998 -
_$ SYS$MANAGER:SECURITY.AUDIT$JOURNAL
|
The command in this example selects records dated later than November 25, 1998.
| #2 |
|---|
$ ANALYZE/AUDIT /SINCE=25-NOV-1998:15:00 -
_$ SYS$MANAGER:SECURITY.AUDIT$JOURNAL
|
The command in this example selects records written after 3 P.M. on November 25, 1998.
Specifies that a summary of the selected records be produced after all records are processed.You can use the /SUMMARY qualifier alone or in combination with the /BRIEF, the /BINARY, or the /FULL qualifier.
/SUMMARY =presentation
/NOSUMMARY
presentation
Specifies the presentation of the summary. If you do not specify a presentation criterion, ANALYZE/AUDIT summarizes the number of audits.You can specify either of the following presentations:
COUNT
Lists the total number of audit messages for each class of security event that have been extracted from the security audit log file. This is the default.PLOT
Displays a plot showing the class of the audit event, the time of day when the audit was generated, and the name of the system where the audit was generated.
| #1 |
|---|
$ ANALYZE/AUDIT/SUMMARY SYS$MANAGER:SECURITY.AUDIT$JOURNAL
|
The command in this example generates a summary report of all records processed.
Total records read: 9701 Records selected: 9701 Record buffer size: 1031 Successful logins: 542 Object creates: 1278 Successful logouts: 531 Object accesses: 3761 Login failures: 35 Object deaccesses: 2901 Breakin attempts: 2 Object deletes: 301 System UAF changes: 10 Volume (dis)mounts: 50 Rights db changes: 8 System time changes: 0 Netproxy changes: 5 Server messages: 0 Audit changes: 7 Connections: 0 Installed db changes: 50 Process control audits: 0 Sysgen changes: 9 Privilege audits: 91 NCP command lines: 120
| #2 |
|---|
$ ANALYZE/AUDIT/FULL/EVENT_TYPE=(BREAKIN,LOGFAIL)/SUMMARY -
_$ SYS$MANAGER:SECURITY.AUDIT$JOURNAL
|
The command in this example generates a full format listing of all logged audit messages that match the break-in or log failure event classes. A summary report is included at the end of the listing.
| #3 |
|---|
$ ANALYZE/AUDIT/FULL/EVENT_TYPE=(BREAKIN,LOGFAIL)/SUMMARY=PLOT -
_$ SYS$MANAGER:SECURITY.AUDIT$JOURNAL
|
This command generates a histogram that you can display on a character-cell terminal.
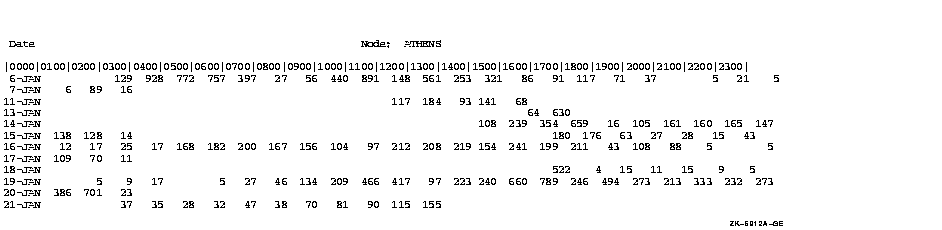
4.4 ANALYZE/AUDIT Commands
This section describes the interactive commands available with the
Audit Analysis utility (ANALYZE/AUDIT). The qualifiers for this section
follow the standard rules of DCL grammar.
The utility runs interactively by default; you disable the feature with
the /NOINTERACTIVE qualifier to the ANALYZE/AUDIT command. To enter
interactive commands, press Ctrl/C at any time during the processing of
a full or brief interactive display. At the COMMAND> prompt, you can
enter any command listed in this section. Use the CONTINUE command to
resume processing of the event records, or use the EXIT command to
terminate the session.
CONTINUE
Resumes processing of event records.
CONTINUE
None.
None.
COMMAND> DISPLAY/SINCE=25-JAN-1998/SELECT=USERNAME=JOHNSON
COMMAND> CONTINUE
|
The first command in this example selects only event records generated by user JOHNSON after January 25, 1998. The second command in the example displays a report based on the new selection criteria.
Changes the criteria used to select event records.
DISPLAY
None.
For a more complete description of any one of the following qualifiers, refer to the description of the qualifier in the preceding ANALYZE/AUDIT Qualifiers section.
/BEFORE=time
Controls whether only those records dated earlier than the specified time are selected./BRIEF
Controls whether a brief (one-line-per-record) format is used in ASCII displays./EVENT_TYPE=event-type[,...]
Controls whether only those records matching the specified event type are selected./FULL
Controls whether a full format for each record is used in ASCII displays./IGNORE=criteria[,...]
Controls whether records matching the specified criteria are excluded. If you specify /IGNORE two or more times, the criteria are combined. To specify a new set of exclusion criteria, include the /REMOVE qualifier with the /IGNORE qualifier./PAUSE=seconds
For full-format displays (/FULL), specifies the length of time each record is displayed./REMOVE
Controls whether the criteria specified by the /IGNORE and the /SELECT qualifiers are no longer to be used to select event records to be displayed./SELECT=criteria[,...]
Controls whether only those records matching the specified criteria are selected. If you specify /SELECT two or more times, the criteria are combined. To specify a new set of selection criteria, include the /REMOVE qualifier with the /SELECT qualifier./SINCE[=time]
Controls whether only those records dated the same or later than the specified time are selected.
| #1 |
|---|
COMMAND> DISPLAY/EVENT_TYPE=SYSUAF
COMMAND> CONTINUE
|
The first command in this example selects records that were generated as a result of a modification to the system user authorization file (SYSUAF). The second command displays the selected records.
| #2 |
|---|
COMMAND> DISPLAY/SELECT=USERNAME=CRICK
COMMAND> CONTINUE
.
.
.
[Ctrl/C]
COMMAND> DISPLAY/SELECT=USERNAME=WATSON
COMMAND> CONTINUE
|
The first DISPLAY command in this example selects records that were generated by user CRICK. The second command displays the selected records. The next DISPLAY command selects records that were generated by user WATSON. The last command in the example displays all records generated by users CRICK and WATSON.
Terminates the session.
EXIT
None.
None.
Provides online help information for using ANALYZE/AUDIT commands.
HELP [topic]
topic
Specifies the command for which help information is to be displayed. If you omit the keyword, HELP displays a list of available help topics and prompts you for a particular keyword.
None.
COMMAND> HELP DISPLAY
|
The command in this example displays help information about the DISPLAY command.
Changes the criteria used to select event records. The LIST command is synonymous with the DISPLAY command.
LIST
None.
See the description of the DISPLAY command.
COMMAND> LIST/EVENT_TYPE=SYSUAF
COMMAND> CONTINUE
|
The first command in this example selects records that were generated as a result of a modification to the system user authorization file (SYSUAF). The second command displays the selected records.
Controls whether the current security audit log file is closed and the next log file opened. The command is useful when you supply a wildcard file specification to the ANALYZE/AUDIT command; for example *.AUDIT$JOURNAL. If there are no other audit log files to open, the audit analysis session terminates and control returns to DCL.
NEXT FILE
None.
None.
Controls whether the next audit record is displayed. The NEXT RECORD command is the default for interactive mode.This command is synonymous with the POSITION command.
NEXT RECORD
None.
None.
Moves the full-format display forward or backward the specified number of event records.
POSITION number
number
For positive numbers, displays the record that is the specified number of records after the current record. For negative numbers, displays the record that is the specified number of records before the current record.
None.
| #1 |
|---|
COMMAND> POSITION 100
|
The command in this example moves the display forward 100 event records.
| #2 |
|---|
COMMAND> POSITION -100
|
The command in this example moves the display back 100 event records.
Displays information about the selection or exclusion criteria currently being used to select event records.
SHOW option[,...]
option[,...]
Displays information about selection or exclusion criteria currently being used to select records. Specify one or more of the following options:
ALL Displays all criteria being used to select event records. EXCLUSION_CRITERIA Displays the criteria being used to exclude event records. SELECTION_CRITERIA Displays the criteria being used to select event records.
None.
COMMAND> SHOW SELECTION_CRITERIA
|
The command in this example displays the selection criteria currently in use to select records.
5.1 AUTHORIZE Description
The Authorize utility (AUTHORIZE) is a system management tool used to
control access to the system and to allocate resources to users.
AUTHORIZE creates new records or modifies existing records in the
following files:
These files store system authorization information. By default, they are owned by the system (UIC of [SYSTEM]) and are created with the following protection:
SYSUAF.DAT S:RWED, O:RWED, G, W NETPROXY.DAT S:RWED, O:RWED, G, W NET$PROXY.DAT S, O, G, W RIGHTSLIST.DAT S:RWED, O:RWED, G, W: |
To use AUTHORIZE, you must have write access to all three of these files (you must have an account with the user identification code (UIC) of [SYSTEM] or the SYSPRV privilege).
Note that you must have read access to the RIGHTSLIST.DAT file (or sufficient privileges) to display the rights identifiers held by other users.
Because certain images (such as MAIL and SET) require access to the system user authorization file (UAF) and are normally installed with the SYSPRV privilege, ensure that you always grant system access to SYSUAF.DAT.
When you install a new system, the software distribution kit provides the following records in the system user authorization file in SYS$SYSTEM:
On VAX systems:
On Alpha systems:
If the SYSUAF.DAT becomes corrupted or is accidentally deleted, you can use the template file SYSUAF.TEMPLATE in the SYS$SYSTEM directory to recreate the file, as follows:
$ SET DEFAULT SYS$SYSTEM $ COPY SYSUAF.TEMPLATE SYSUAF.DAT |
The file SYSUAF.TEMPLATE contains records that are identical to those defined when the system was installed.
To make an emergency backup for the system SYSUAF file, you can create a private copy of SYSUAF.DAT. To affect future logins, copy a private version of SYSUAF.DAT to the appropriate directory, as shown in the following example:
$ COPY MYSYSUAF.DAT SYS$COMMON:[SYSEXE]:SYSUAF.DAT- _$ /PROTECTION=(S:RWED,O:RWED,G,W) |
The Authorize utility (AUTHORIZE) is a system management tool that enables you to control access to the system and to allocate resources to users.
RUN SYS$SYSTEM:AUTHORIZE
None.Usage Summary To invoke AUTHORIZE, set your default device and directory to SYS$SYSTEM and enter RUN AUTHORIZE at the DCL command prompt. At the UAF> prompt, you can enter any AUTHORIZE command described in the following section.
To exit from AUTHORIZE, enter the EXIT command at the UAF> prompt or press Ctrl/Z.
If you move the SYSUAF.DAT file, be sure the logical name SYSUAF is defined and points to an existing file. If AUTHORIZE is unable to locate the SYSUAF.DAT file, it displays the following error message:
%UAF-E-NAOFIL, unable to open SYSUAF.DAT -RMS-E-FNF, file not found Do you want to create a new file? |
A response of YES results in creation of a new SYSUAF file containing a
SYSTEM record and a DEFAULT record. These records are initialized with
the same values set when the system was installed.
5.3 AUTHORIZE Commands
This section describes the AUTHORIZE commands and provides examples of their use. You can abbreviate any command, keyword, or qualifier as long as the abbreviation is not ambiguous. The asterisk (*) and the percent sign (%) can be used as wildcard characters to specify user names, node names, and UICs.
AUTHORIZE commands fall into the following four categories:
The following table summarizes the AUTHORIZE commands according to these categories.
| Command | Description |
|---|---|
| Managing System Resources and User Accounts with SYSUAF | |
| ADD | Adds a user record to the SYSUAF and corresponding identifiers to the rights database. |
| COPY | Creates a new SYSUAF record that duplicates an existing record. |
| DEFAULT | Modifies the default SYSUAF record. |
| LIST | Writes reports for selected UAF records to a listing file, SYSUAF.LIS. |
| MODIFY | Changes values in a SYSUAF user record. Qualifiers not specified in the command remain unchanged. |
| REMOVE | Deletes a SYSUAF user record and corresponding identifiers in the rights database. The DEFAULT and SYSTEM records cannot be deleted. |
| RENAME | Changes the user name of the SYSUAF record (and, if specified, the corresponding identifier) while retaining the characteristics of the old record. |
| SHOW | Displays reports for selected SYSUAF records. |
| Managing Network Proxies with NETPROXY.DAT or NET$PROXY.DAT | |
| ADD/PROXY | Adds proxy access for the specified user. |
| CREATE/PROXY | Creates a network proxy authorization file. |
| LIST/PROXY | Creates a listing file of all proxy accounts and all remote users with proxy access to the accounts. |
| MODIFY/PROXY | Modifies proxy access for the specified user. |
| REMOVE/PROXY | Deletes proxy access for the specified user. |
| SHOW/PROXY | Displays proxy access allowed for the specified user. |
| Managing Identifiers with RIGHTSLIST.DAT | |
| ADD/IDENTIFIER | Adds an identifier name to the rights database. |
| CREATE/RIGHTS | Creates a new rights database file. |
| GRANT/IDENTIFIER | Grants an identifier name to a UIC identifier. |
| LIST/IDENTIFIER | Creates a listing file of identifier names and values. |
| LIST/RIGHTS | Creates a listing file of all identifiers held by the specified user. |
| MODIFY/IDENTIFIER | Modifies the named identifier in the rights database. |
| REMOVE/IDENTIFIER | Removes an identifier from the rights database. |
| RENAME/IDENTIFIER | Renames an identifier in the rights database. |
| REVOKE/IDENTIFIER | Revokes an identifier name from a UIC identifier. |
| SHOW/IDENTIFIER | Displays identifier names and values on the current output device. |
| SHOW/RIGHTS | Displays on the current output device the names of all identifiers held by the specified user. |
| General Commands | |
| EXIT | Returns the user to DCL command level. |
| HELP | Displays HELP text for AUTHORIZE commands. |
| MODIFY/SYSTEM_PASSWORD | Sets the system password (equivalent to the DCL command SET PASSWORD/SYSTEM). |
Adds a user record to the SYSUAF and corresponding identifiers to the rights database.
ADD newusername
newusername
Specifies the name of the user record to be included in the SYSUAF. The newusername parameter is a string of 1 to 12 alphanumeric characters and can contain underscores. Although dollar signs are permitted, they are usually reserved for system names.Avoid using fully numeric user names (for example, 89560312). A fully numeric user name cannot receive a corresponding identifier because fully numeric identifiers are not permitted.
/ACCESS[=(range[,...])]
Specifies hours of access for all modes of access. The syntax for specifying the range is:
/[NO]ACCESS=([PRIMARY], [n-m], [n], [,...],[SECONDARY], [n-m], [n], [,...])
Specify hours as integers from 0 to 23, inclusive. You can specify single hours (n) or ranges of hours (n-m). If the ending hour of a range is earlier than the starting hour, the range extends from the starting hour through midnight to the ending hour. The first set of hours after the keyword PRIMARY specifies hours on primary days; the second set of hours after the keyword SECONDARY specifies hours on secondary days. Note that hours are inclusive; that is, if you grant access during a given hour, access extends to the end of that hour.
Previous Next Contents Index
![[Site home]](../../images/buttons/bn_site_home_off.gif)
![[Send comments]](../../images/buttons/bn_comments_off.gif)
![[Help with this site]](../../images/buttons/bn_site_help_off.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs_off.gif)
![[OpenVMS site]](../../images/buttons/bn_openvms_off.gif)
![[Compaq site]](../../images/buttons/bn_compaq_off.gif)
![[OpenVMS documentation]](../../images/openvms_doc_banner_bottom.gif)
Copyright © Compaq Computer Corporation 1998. All rights reserved.
Legal6048PRO_008.HTML