| Previous | Contents | Index |
This chapter describes the use of the ACMS Application Authorization
Utility (AAU) to authorize ACMS applications.
See Section 4.6 for a summary of AAU commands and qualifiers. For
reference information on the commands described in this chapter, refer
to Chapter 19.
4.1 How AAU Works
System managers use the Application Authorization Utility (AAU) to create an application authorization file (ACMSAAF.DAT) that contains records, called authorizations, of an application's information. Authorizing applications lets a system manager define the characteristics of an application, such as:
Figure 4-1 shows the authorization portion of the AAU process.
Figure 4-1 AAU Application Authorization Process
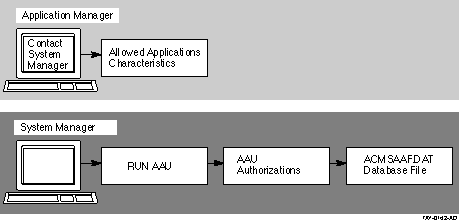
Before users can start an ACMS application, the application database file for that application must be stored in the directory pointed to by the logical name ACMS$DIRECTORY. For security reasons, this directory is set up as a protected directory to prevent an unauthorized user from storing applications containing tasks that run under privileged user names.
With the AAU commands and qualifiers, a system manager can authorize applications and grant application installation rights to users who otherwise do not have access to ACMS$DIRECTORY. Users who are authorized to install .ADB files can then install the application in ACMS$DIRECTORY by using the ACMS/INSTALL operator command.
Using AAU is optional for users who already have access to ACMS$DIRECTORY. These users can store .ADB files in ACMS$DIRECTORY without authorization in the AAU. For example, these users could use the DCL COPY command to copy an .ADB file into ACMS$DIRECTORY.
By authorizing users to install applications, you gain the following benefits:
Users named in the AAU database can use the ACMS/INSTALL operator
command to install any application for which they have installation
authorization. When a user issues this command, ACMS checks the
AAU authorization file (ACMSAAF.DAT) to see if the application has an
authorization in the file and if the user running the ACMS/INSTALL
command is authorized to install the application. If either the
application or the user trying to install it is not authorized in the
AAU authorization file, ACMS prevents the installation of the
application.
4.2 How to Run AAU
Use either of the following commands to run AAU:
$ RUN SYS$SYSTEM:ACMSAAU AAU> |
or
$ MCR ACMSAAU AAU> |
When you run AAU, ACMS displays the AAU prompt (AAU<!CLOSE>). Then enter any AAU command (including the AAU command HELP to get online help information) or press the [PF1] and [PF2] keys for access to a keypad of AAU commands. Press [Ctrl/B] to recall each AAU command you enter. To exit from AAU, use the AAU command EXIT or press [Ctrl/Z].
When you run AAU, ACMS searches for the ACMSAAF.DAT in SYS$SYSTEM. If ACMSAAF.DAT does not exist, you are asked if you want to create a new authorization file. You can store ACMSAAF.DAT in a directory other than SYS$SYSTEM by defining the executive mode system logical name ACMSAAF:
$ DEFINE/SYSTEM/EXEC ACMSAAF DEVDISK:ACMSAAF.DAT |
ACMS creates a DEFAULT authorization the first time you run AAU, or any time you run AAU from a directory that has no ACMSAAF.DAT. The DEFAULT authorization is created with an empty access control list; by default, no users are authorized to install applications in ACMS$DIRECTORY. Table 4-1 contains a list of the initial values that AAU assigns to the DEFAULT authorization when it is created.
| Qualifier | Default Setting |
|---|---|
| /ACL | (IDENTIFICATION=*, ACCESS=NONE)---the default ACL denies installation rights |
| /APPL_USERNAME | /APPL_USERNAME=* |
| /[NO]WILD_SUFFIX | /NOWILD_SUFFIX |
| /[NO]DYN_USERNAMES | /NODYN_USERNAMES |
| /SRV_USERNAMES | /SRV_USERNAMES=* |
In Table 4-1, the wildcard character (*) indicates that any user
name or ID in the application is acceptable. To ensure that an
application is running with the right user names, override the wildcard
defaults by assigning user names in application authorizations.
4.3 Before Authorizing Applications
Before starting to authorize applications, you may want to change the initial default values in the DEFAULT authorization. Do this with either the DEFAULT or the MODIFY command. The new values should reflect the characteristics that you intend to assign to the majority of applications you plan to authorize.
For example, suppose you have to authorize five applications and plan to give the same users the right to install all the applications. Assign a default value to those users in the DEFAULT authorization. When you authorize the five applications with the ADD command, you do not need to use the /ACL qualifier. The ADD command uses the default /ACL value from the DEFAULT authorization.
Because of privileges and quotas that are associated with certain user names, you must be careful about:
For example, suppose an application manager decides that several applications should run only with particular user names and server process user names, and that these applications should run without server processes having dynamic user names. The application manager can use AAU to create applications in such a way that the application is not installed unless these settings match the ones found in the .ADB file.
Figure 4-2 shows the information that must match before an application can be installed.
Figure 4-2 Conditions for Installing an Application
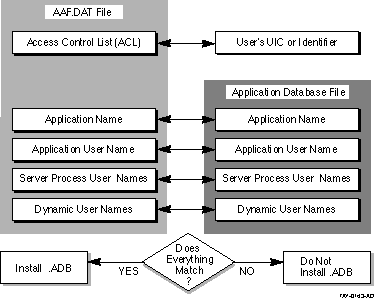
Even if the application information is changed, the application cannot
be installed unless it has the same values the application manager
originally assigned in the application authorization. This extra layer
of security ensures that each application running on an ACMS system has
passed a series of tests that protect applications from unauthorized
use.
4.4 Authorizing New Applications
The following sections show several different approaches to take when
authorizing applications. For example, if you have few applications to
authorize, you may want to write individual authorizations for each
application. If you have many applications to authorize, you may want
to take advantage of the DEFAULT authorization using the $ALL
application name.
4.4.1 Authorizing All Applications with $ALL
The quickest and simplest way to authorize applications is to create a $ALL authorization. Use $ALL as the application name when you enter the ADD command in response to the AAU prompt. For example:
AAU> ADD $ALL /ACL=(IDENTIFIER=[GORDON],ACCESS=CONTROL) |
If you have not altered the DEFAULT authorization, the $ALL
authorization takes the default values that ACMS originally sets for
all the qualifiers you do not include with the ADD command. The
preceding ADD command, therefore, creates a $ALL authorization allowing
user GORDON to install any application on the system.
4.4.2 Authorizing Individual Applications
If you choose to create individual authorizations for each application, name the application with the ADD command and assign any necessary qualifiers. For example:
AAU> ADD INVENTORY /ACL=(ID=[GORDON],ACCESS=CONTROL) - _AAU> /APPL_USERNAME=INVTRY - _AAU> /SRV_USERNAMES=(PARTS,STOCK) - _AAU> /DYNAMIC_USERNAMES - _AAU> /NOWILD_SUFFIX |
This command authorizes user GORDON to install the application INVENTORY if the application database file (.ADB) has the application user name INVTRY and two server processes with user names PARTS and STOCK. The /DYNAMIC_USERNAMES qualifier lets user GORDON install the INVENTORY application with the dynamic user name characteristic. Because all qualifiers are included, the ADD command does not use any default values from the DEFAULT authorization.
When there is an authorization in the AAU authorization file with characteristics similar to one you want to create, you can save time by using the COPY command. For example:
AAU> COPY INVENTORY ACCOUNTING /ACL=(ID=[SMITH],ACC=CON)- _AAU> /SRV_USERNAMES=(ADD,SUB) |
Here the COPY command creates an exact copy of the INVENTORY
application authorization and names it ACCOUNTING. The qualifiers with
the COPY command change the authorized user to SMITH and the two server
user names to ADD and SUB.
4.4.3 Authorizing Applications with /[NO]WILD_SUFFIX
The /[NO]WILD_SUFFIX qualifier allows a user to install or prevents a user from installing any application whose name begins with the letters of the application name you are installing.
If your ACMS system has many applications that begin with the same characters, the /WILD_SUFFIX qualifier can save you time and give you additional flexibility when you are creating authorizations. For example:
AAU> ADD TEST /WILD_SUFFIX /APPL_USERNAME=TEST_EXE - _AAU> /ACL=(ID=[SMITH],ACCESS=CONTROL) - _AAU> /SRV_USERNAMES=(TEST1,TEST2) - _AAU> /NODYN_USERNAMES |
This command lets the authorized user SMITH install any application
that starts with the letters TEST. SMITH can install applications such
as TEST, TESTA, TESTB, TESTC, TEST1.
4.5 Working with Existing AAU Authorizations
During an AAU session you may need to display, list, delete, or rename
the application authorizations in the AAU authorization file. The
following sections describe these functions.
4.5.1 Looking at AAU Authorizations with SHOW and LIST
There are many occasions when a quick check of authorizations in the AAU authorization file is helpful. For example, you may need to check the DEFAULT authorization if you cannot remember its current settings. To display application authorizations on your terminal screen, use the SHOW command. The output from the SHOW command is shown in Example 4-1.
When you use the wildcard character (*), AAU displays all authorizations in the AAU authorization file. To see a particular application authorization, include the application name with the SHOW command.
To obtain a hardcopy listing of information in the authorization file, use the LIST command with the application name at the AAU> prompt. For example:
AAU> LIST CREDITOR |
This command copies the contents of the CREDITOR application authorization to the ACMSAAU.LIS file in your default directory.
| Example 4-1 AAU SHOW Command |
|---|
AAU> SHOW * |
================================================================== Appl Name: $ALL Appl Username: * Server Usernames: * Access Control List: (IDENTIFIER=[*,*],ACCESS=CONTROL) ================================================================== Appl Name: CREDITOR Appl Username: CREDIT Server Usernames: CREDIT1 CREDIT2 Access Control List: (IDENTIFIER=[PAYUP,*],ACCESS=CONTROL) =================================================================== Appl Name: DEFAULT WILD SUFFIX Appl Username: DEBT Server Usernames: DEBT1 DEBT2 Access Control List: (IDENTIFIER=[PERSONNEL,*],ACCESS=CONTROL) =================================================================== AAU> |
If an application is no longer being used, you need to remove its
authorization from the AAU authorization file. When you identify unused
applications, you can delete them with the REMOVE command. The REMOVE
command deletes the application authorization from the authorization
file and prints a message confirming the action. The application name
can be that of an application, or it can be $ALL.
4.5.3 Renaming AAU Authorizations
You can use the RENAME command when you want to change the name of an
authorization. Because the RENAME command uses the same qualifiers as
the ADD, COPY, DEFAULT, and MODIFY commands, you can change any of the
original authorization's characteristics while you change the
authorization's name.
4.6 Summary of AAU Commands and Qualifiers
AAU commands allow you to create, change, and remove device definitions stored in the AAU authorization file. Table 4-2 lists the AAU commands and qualifiers and provides a brief description of each command. See Chapter 19 for a complete description of each AAU command and qualifier.
| Commands and Qualifiers | Description |
|---|---|
|
ADD
/ACL=(ace[,...]) /APPL_USERNAME=appl-username /[NO]DYNAMIC_USERNAMES /[NO]WILD_SUFFIX /SRV_USERNAME [=(srv-username[,...])] |
Creates authorizations so that AAU authorized users can install application database files in ACMS$DIRECTORY. If you omit the qualifiers, the new definition takes qualifier information from the DEFAULT definition. |
|
COPY
/ACL=(ace[,...]) /APPL_USERNAME=appl-username /[NO]DYNAMIC_USERNAMES /[NO]WILD_SUFFIX /SRV_USERNAME [=(srv-username[,...])] |
Creates a new authorization by copying information from an existing authorization and, with qualifiers, changes other information. |
|
DEFAULT
/ACL=(ace[,...]) /APPL_USERNAME=appl-username /[NO]DYNAMIC_USERNAMES /[NO]WILD_SUFFIX /SRV_USERNAME [=(srv-username[,...])] |
Changes information in the DEFAULT authorization. If you omit one or more qualifiers from the ADD command, the new authorization takes information from the existing DEFAULT authorization. |
| EXIT | Ends the AAU session and returns you to the DCL prompt. |
|
HELP
/[NO]PROMPT |
Displays information about AAU commands, parameters, and qualifiers. |
|
LIST
/BRIEF /OUTPUT=[file-spec] |
Writes AAU definitions to ACMSAAU.LIS in your default directory or to an output file you specify. |
|
MODIFY
/ACL=(ace[,...]) /APPL_USERNAME=appl-username /[NO]DYNAMIC_USERNAMES /[NO]WILD_SUFFIX /SRV_USERNAMES [=(srv-username[,...])] |
Changes information in AAU authorizations. |
| REMOVE | Deletes an authorization from the authorization file (ACMSAAF.DAT). |
|
RENAME
/ACL=(ace[,...]) /APPL_USERNAME=appl-username /[NO]DYNAMIC_USERNAMES /[NO]WILD_SUFFIX /SRV_USERNAMES [=(srv-username[,...]) ] |
Changes the name of an application authorization and, with qualifiers, other information in the AAU authorization. |
|
SHOW
/BRIEF |
Displays application authorizations at your terminal. |
| Previous | Next | Contents | Index |