![[OpenVMS documentation]](../../images/openvms_doc_banner_top.gif)
|
![[Site home]](../../images/buttons/bn_site_home_off.gif)
![[Send comments]](../../images/buttons/bn_comments_off.gif)
![[Help with this site]](../../images/buttons/bn_site_help_off.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs_off.gif)
![[OpenVMS site]](../../images/buttons/bn_openvms_off.gif)
![[Compaq site]](../../images/buttons/bn_compaq_off.gif)
|
| Updated: 11 December 1998 |
![[OpenVMS documentation]](../../images/openvms_doc_banner_top.gif)
|
![[Site home]](../../images/buttons/bn_site_home_off.gif)
![[Send comments]](../../images/buttons/bn_comments_off.gif)
![[Help with this site]](../../images/buttons/bn_site_help_off.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs_off.gif)
![[OpenVMS site]](../../images/buttons/bn_openvms_off.gif)
![[Compaq site]](../../images/buttons/bn_compaq_off.gif)
|
| Updated: 11 December 1998 |
OpenVMS System Management Utilities Reference
Manual
| Previous | Contents | Index |
Figure F-3 illustrates the format of an audit data packet. NSA$K_PKT_HDR_LENGTH defines the current size of each packet header (in bytes).
Note that audit data packets do not appear in any predefined order within an event message, and packet types can appear more than once throughout the event message.
For examples of the types of data appearing in different event messages, refer to the appendix of alarm messages in the OpenVMS Guide to System Security.
Figure F-3 Audit Data Packet Format
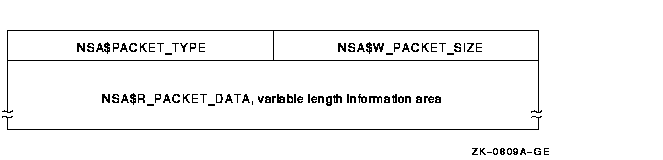
Table F-4 describes the fields contained in these packets.
| Field | Symbolic Offset | Contents |
|---|---|---|
| Packet size | NSA$W_PACKET_SIZE | Indicates the size of the data packet. (Word) |
| Packet type | NSA$W_PACKET_TYPE | Indicates the type of data in the packet, as described in Table F-5. |
| Packet data | NSA$R_PACKET_DATA | Variable length field containing the packet data. |
Table F-5 describes the types of data in audit packets.
| Symbol | Packet Contents |
|---|---|
| NSA$_ACCESS_DESIRED | Access requested or granted to the object as defined by $ARMDEF (Longword) |
| NSA$_ACCESS_MODE | Access mode of the process (Byte) |
| NSA$_ACCOUNT | Account name associated with the process (String of 1-32 characters) |
| NSA$_ALARM_NAME | Name of the user (or the security class operators terminal) to receive the record (String of 1-32 characters) |
| NSA$_ASSOCIATION_NAME | Interprocess communication (IPC) association name (String of 1-256 characters) |
| NSA$_AUDIT_FLAGS | Bit mask of enabled or disabled events. This is reserved to Compaq. (40-byte record) (String of 1-65 characters) |
| NSA$_AUDIT_NAME | Journal file to receive the audit record (String of 1-65 characters) |
| NSA$_COMMAND_LINE | Command line the user entered (String of 1-2048 characters) |
| NSA$_CONNECTION_ID | Interprocess communication (IPC) connection identification (Longword) |
| NSA$_DECNET_LINK_ID | DECnet logical link identification (Longword) |
| NSA$_DECNET_OBJECT_NAME | DECnet object name (String of 1-16 characters) |
| NSA$_DECNET_OBJECT_NUMBER | DECnet object number (Longword) |
| NSA$_DEFAULT_USERNAME | Default local user name for incoming network proxy requests (String of 1-32 characters) |
| NSA$_DEVICE_NAME | Device name where the volume resides (String of 1-64 characters) |
| NSA$_DIRECTORY_ENTRY | Directory entry associated with file system operation (Longword) |
| NSA$_DIRECTORY_ID | Directory file identification (Array of 3 words) |
| NSA$_DIRECTORY_NAME | Directory file name |
| NSA$_DISMOUNT_FLAGS | The $DMTDEF macro in STARLET defines the dismount flags; each flag is one quadword. |
| NSA$_EFC_NAME | Event flag cluster name (String of 1-16 characters) |
| NSA$_EVENT_FACILITY | Facility code for the generated event (Word) |
| NSA$_FIELD_NAME | Name of the field being modified. This is used in combination with NSA$_ORIGINAL_DATA and NSA$_NEW_DATA. (String of 1-256 characters) |
| NSA$_FILE_ID | File identification (Array of words) |
| NSA$_FINAL_STATUS | Status (successful or unsuccessful) causing the auditing facility to be invoked (Longword) |
| NSA$_HOLDER_NAME | Name of user holding the identifier (String of 1-32 characters) |
| NSA$_HOLDER_OWNER | Owner (UIC) of holder (Longword) |
| NSA$_ID_ATTRIBUTES | Attributes of the identifier, which are defined by the $KGBDEF macro in STARLET (Longword) |
| NSA$_IDENTIFIERS_USED | Identifiers (from the access control entry (ACE) granting access) used to gain access to the object (Array of longwords) |
| NSA$_ID_NAME | Name of the identifier (String of 1-32 characters) |
| NSA$_ID_NEW_ATTRIBUTES | New attributes of the identifier, which are defined by the $KGBDEF macro in STARLET (Longword) |
| NSA$_ID_NEW_NAME | New name of the identifier (String of 1-32 characters) |
| NSA$_ID_NEW_VALUE | New value of the identifier (Longword) |
| NSA$_ID_VALUE | Value of the identifier (Longword) |
| NSA$_ID_VALUE_ASCII | Identification value provided by $IDTOASC (Longword) |
| NSA$_IMAGE_NAME | Name of the image being executed when the event took place (String of 1-1024 characters) |
| NSA$_INSTALL_FILE | The name of the installed file (String of 1-255 characters) |
| NSA$_INSTALL_FLAGS | The INSTALL flags correspond to qualifiers for the Install utility (for example, NSA$M_INS_EXECUTE_ONLY); each flag is one longword. |
| NSA$_LNM_PARENT_NAME | Name of the parent logical name table (String of 1-31 characters) |
| NSA$_LNM_TABLE_NAME | Name of the logical name table (String of 1-31 characters) |
| NSA$_LOCAL_USERNAME | User name of the account available for incoming network proxy requests (String of 1-32 characters) |
| NSA$_LOGICAL_NAME | Logical name associated with the device (String of 1-255 characters) |
| NSA$_MAILBOX_UNIT | Mailbox unit number (Longword) |
| NSA$_MATCHING_ACE | ACE granting or denying access (Array of bytes) |
| NSA$_MESSAGE | Associated message code; see NSA$_MSGFILNAM for translation (Longword) |
| NSA$_MOUNT_FLAGS | The MOUNT flags defined by the $MNTDEF macro in STARLET (Longword) |
| NSA$_MSGFILNAM | Message file containing the translation for the message code in NSA$_MESSAGE (String of 1-255 characters) |
| NSA$_NEW_DATA | Contents of the field named in NSA$_FIELD_NAME after the event occurred. NSA$_ORIGINAL_DATA contains the field contents prior to the event. (String of 1-n characters) |
| NSA$_NEW_IMAGE_NAME | Name of the new image (String of 1-1024 characters) |
| NSA$_NEW_OWNER | New process owner (UIC) (Longword) |
| NSA$_NEW_PRIORITY | New process priority (Longword) |
| NSA$_NEW_PRIVILEGES | New privileges (Quadword) |
| NSA$_NEW_PROCESS_ID | New identification of the process (Longword) |
| NSA$_NEW_PROCESS_NAME | New name of the process (String of 1-15 characters) |
| NSA$_NEW_PROCESS_OWNER | New owner (UIC) of the process (Longword) |
| NSA$_NEW_USERNAME | New user name (String of 1-32 characters) |
| NSA$_NOP | Packet in static event list to omit from processing |
| NSA$_OBJECT_CLASS | Object class name, as defined by the system or by the user (String of 1-23 characters) |
| NSA$_OBJECT_MAX_CLASS | The minimum access classification of the object (20-byte record) |
| NSA$_OBJECT_MIN_CLASS | The minimum access classification of the object (20-byte record) |
| NSA$_OBJECT_NAME | Object's name (String of 1-255 characters) |
| NSA$_OBJECT_NAME_2 | Alternate object name; currently applies to file-backed global sections where the alternate name of global section is the file name. (String of 1-255 characters) |
| NSA$_OBJECT_OWNER | UIC or general identifier of the process causing the auditable event (Longword) |
| NSA$_OBJECT_PROTECTION | UIC-based protection of the object (Vector of words or longwords) |
| NSA$_OBJECT_TYPE | Object's type code, as listed in $ACLDEF. (String of 1-23 characters) |
| NSA$_OLD_PRIORITY | Former process priority (Longword) |
| NSA$_OLD_PRIVILEGES | Former privileges (Quadword) |
| NSA$_ORIGINAL_DATA | Contents of the field named in NSA$_FIELD_NAME before the event occurred. NSA$_NEW_DATA contains the field contents following the event. (String of 1-n characters) |
| NSA$_PARAMS_INUSE | Set of parameter values given to the SYSGEN command USE (String of 1-255 characters) |
| NSA$_PARAMS_WRITE | File name for the SYSGEN command WRITE (String of 1-255 characters) |
| NSA$_PARENT_ID | Process identifier (PID) of the parent process; only used when auditing events pertaining to a subprocess (Longword) |
| NSA$_PARENT_NAME | Parent's process name; only used when auditing events pertaining to a subprocess (String of 1-15 characters) |
| NSA$_PARENT_OWNER | Owner (UIC) of the parent process (Longword) |
| NSA$_PARENT_USERNAME | User name associated with the parent process (String of 1-32 characters) |
| NSA$_PASSWORD | Password used in unsuccessful break-in attempt (String of 1-32 characters) |
| NSA$_PRIVILEGES | Privilege mask (Quadword) |
| NSA$_PRIVS_MISSING | Privileges that are lacking (Longword or quadword) |
| NSA$_PRIVS_USED | Privileges used to gain access to the object (Longword or quadword) |
| NSA$_PROCESS_ID | PID of the process causing the auditable event (Longword) |
| NSA$_PROCESS_NAME | Process' name that caused the auditable event (String of 1-15 characters) |
| NSA$_REM_ASSOCIATION_NAME | Interprocess communication (IPC) remote association name (String of 1-256 characters) |
| NSA$_REMOTE_LINK_ID | Remote logical link identification number (Longword) |
| NSA$_REMOTE_NODE_ID | DECnet address of the remote process (Longword) |
| NSA$_REMOTE_NODENAME | DECnet node name of the remote process (String of 1-6 characters) |
| NSA$_REMOTE_USERNAME | User name of the remote process (String of 1-32 characters) |
| NSA$_REQUEST_NUMBER | Request number associated with the system service call (Longword) |
| NSA$_RESOURCE_NAME | Lock resource name (String of 1-32 characters) |
| NSA$_SECTION_NAME | Global section name (String of 1-42 characters) |
| NSA$_SNAPSHOT_BOOTFILE | The name of the snapshot boot file, the saved system image file from which the system just booted (String of 1-255 characters) |
| NSA$_SNAPSHOT_SAVE_FILNAM | The name of the snapshot save file, which is the original location of the snapshot file at the time that the system was saved (String of 1-255 characters) |
| NSA$_SNAPSHOT_TIME | The time the picture of the configuration was taken and saved in the snapshot boot file (Quadword) |
| NSA$_SOURCE_PROCESS_ID | Identification of process originating the request (Longword) |
| NSA$_SUBJECT_CLASS | The current access class of the process causing the auditable event (A 20-byte record) |
| NSA$_SUBJECT_OWNER | Owner (UIC) of the process causing the event (Longword) |
| NSA$_SYSTEM_ID | SCS identification of the cluster node where the event took place (SYSGEN parameter SCSSYSTEMID) (Longword) |
| NSA$_SYSTEM_NAME | System Communication Services (SCS) node name where the event took place (SYSGEN parameter SCSNODE) (String of 1-6 characters) |
| NSA$_SYSTEM_SERVICE_NAME | Name of the system service associated with the event (String of 1-256 characters) |
| NSA$_SYSTIM_NEW | New system time (Quadword) |
| NSA$_SYSTIM_OLD | Old system time (Quadword) |
| NSA$_TARGET_DEVICE_NAME | Target device name (String of 1-64 characters) |
| NSA$_TARGET_PROCESS_CLASS | The target process classification. (A 20-byte vector) |
| NSA$_TARGET_PROCESS_ID | Target process identifier (PID) (Longword) |
| NSA$_TARGET_PROCESS_NAME | Target process name (String of 1-64 characters) |
| NSA$_TARGET_PROCESS_OWNER | Target process owner (UIC) (Longword) |
| NSA$_TARGET_USERNAME | Target user name (String of 1-32 characters) |
| NSA$_TERMINAL | Name of the terminal to which the process was connected when the auditable event occurred (String of 1-256 characters) |
| NSA$_TIME_STAMP | The time that the event occurred (Quadword) |
| NSA$_TRANSPORT_NAME | Name of transport: interprocess communication (IPC), DECnet, or System Management Integrator (SMI), which handles requests from the SYSMAN utility (String of 1-256 characters) |
| NSA$_UAF_ADD | Name of the authorization record being added (String of 1-32 characters) |
| NSA$_UAF_COPY | Original and new names of the authorization record being copied (String of 1-32 characters) |
| NSA$_UAF_DELETE | Name of the authorization record being removed (String of 1-32 characters) |
| NSA$_UAF_FIELDS | Fields being changed in an authorization record and their new values. This is reserved to Compaq. (Quadword bit mask) |
| NSA$_UAF_MODIFY | Name of the authorization record being modified (String of 1-32 characters) |
| NSA$_UAF_RENAME | Name of the authorization record being renamed (String of 1-32 characters) |
| NSA$_UAF_SOURCE | User name of the source record for an Authorize utility (AUTHORIZE) copy operation (String of 1-32 characters) |
| NSA$_USERNAME | User name of process causing the auditable event (String of 1-32 characters) |
| NSA$_VOLUME_NAME | Volume name (String of 1-15 characters) |
| NSA$_VOLUME_SET_NAME | Volume set name (String of 1-15 characters) |
| Previous | Next | Contents | Index |
![[Site home]](../../images/buttons/bn_site_home_off.gif)
![[Send comments]](../../images/buttons/bn_comments_off.gif)
![[Help with this site]](../../images/buttons/bn_site_help_off.gif)
![[How to order documentation]](../../images/buttons/bn_order_docs_off.gif)
![[OpenVMS site]](../../images/buttons/bn_openvms_off.gif)
![[Compaq site]](../../images/buttons/bn_compaq_off.gif)
|
![[OpenVMS documentation]](../../images/openvms_doc_banner_bottom.gif) |
|
Copyright © Compaq Computer Corporation 1998. All rights reserved. Legal |
6048PRO_077.HTML
|